🚨 Updated #Tycoon tactics: new PDF lures and redirects.
Today, we have a guest post from WatchingRac (@RacWatchin8872 on X)
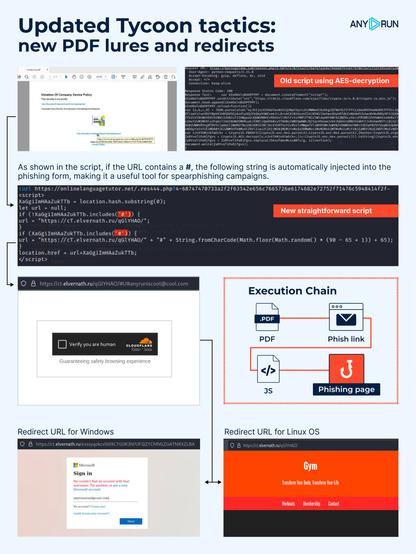
The attack is executed through a PDF sent by the threat actor, tricking the victim into believing they have violated a Company Device Policy. To review the alleged evidence, the victim is prompted to click a button within the PDF, triggering multiple redirects that lead to a fake Outlook website.
🔗 #Phishing chain:
PDF ➡️ Phish link ➡️ /.res444.php/ ➡️ Phishing Outlook website
Victims receive a phishing PDF containing a link to check a violation of the Company Device Policy. By opening it, the victim is directed to /.res444.php/, which loads a script.
👾 After loading the script, the victim is redirected to the phishing page.
❗️ The use of a PHP file containing #JavaScript code to redirect victims to the phishing page was already known within the community. To bypass potential rules designed to alert analysts of such attacks, Tycoon modified the script.
🔙 The previous file, named res444.php, contained JS code that decoded a #Base64 string, split it into parts, and used each segment for AES decryption, ultimately redirecting the victim to the Outlook phishing domain.
🔜 The new file, named .res444.php, contains simple and straightforward #JS code that automatically redirects the victim to the Outlook phishing domain. If the current URL includes a hash (#), it appends a random uppercase letter (A-Z) before redirecting; otherwise, the redirection occurs without modifications.
📌 The value of the phishing domain is always in the URL in hexadecimal form.
The phishing page displays different content based on the operating system. If the User-Agent contains "Linux," it presents a fake gym website. However, if it contains "Windows," it loads the Outlook phishing page.
👨💻 Take a look at the analysis in #ANYRUN Interactive Sandbox: https://app.any.run/tasks/c37665dd-c315-429b-a452-797f551bbd16/?utm_source=mastodon&utm_medium=post&utm_campaign=updated_tycoon&utm_term=270225&utm_content=linktoservice
References:
🔹https://x.com/orlof_v/status/1892944298452165104
🔹https://validin.com/blog/tycoon_2fa_analyzing_and_hunting_phishing-as-a-service_domains/
Analyze and investigate the latest #malware and phishing threats with #ANYRUN 🚀
#cybersecurity #infosec