Laptop only recognizes bootable USB in Legacy but not UEFI? #boot #grub2 #uefi
#grub2
Full_Disk_Encryption_Howto_2019 fails at installing grub #boot #partitioning #grub2 #encryption #externalhdd
Fedora 42 is kinda messing with my mind right now... the GRUB2 entry all become "Fedora Linux 42 (Workstation Edition)" without Kernel version... After some investigation, realized on line 192 in `/usr/lib/kernel/install.d/90-loaderentry.install`, for all kernel entries generated to /boot/loader/entries/, it only uses $PRETTY_NAME from /etc/os-release for $title while GRUB2 loads only the $title... after modifying the title, it finally went normal...
Dual booting of Windows 11 pro and Ubuntu #dualboot #grub2 #windows11
Free space in boot partition while installing updates/ Failed to install grub #dualboot #grub2 #updates #bootpartition
Ubuntu 20.04.6 no longer going to login screen after updates #boot #dualboot #grub2 #gui #loginscreen
Security Week 2515: уязвимости в загрузчике GRUB2
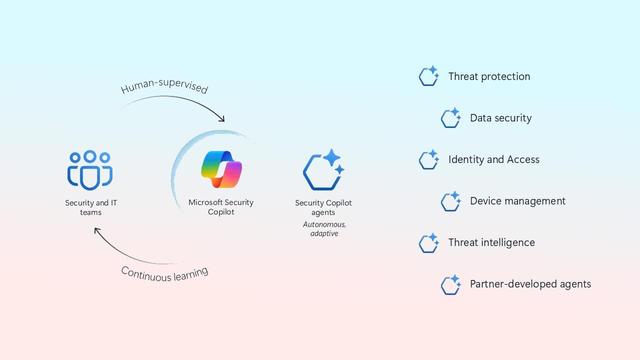
На прошлой неделе компания Microsoft отчиталась об обнаружении 11 уязвимостей в загрузчике GRUB2 с открытым исходным кодом. Мотивацией для Microsoft проанализировать опенсорсный проект была потенциально высокая опасность уязвимостей в GRUB: их эксплуатация может привести к компрометации операционной системы и открыть для потенциального атакующего полный доступ к пользовательским данным. Отдельным интересным моментом данного исследовательского проекта стало использование искусственного интеллекта, версии Microsoft Copilot, специально разработанной для устранения прорех в безопасности. В Microsoft прямо говорят, что использования Security Copilot самого по себе недостаточно для эффективного обнаружения уязвимостей, сервис лишь способен ускорить процесс поиска проблем в исходном коде. Помимо ИИ, в проекте также были задействованы традиционные инструменты, такие как статический анализ кода, фаззинг и ручной анализ. Тем не менее была показана эффективность языковой модели для обнаружения потенциально опасных участков кода, которые затем можно проверить и вручную.
#Microsoft used its #AI-powered #SecurityCopilot to discover 20 previously unknown vulnerabilities in the #GRUB2, #UBoot, and #Barebox #opensource #bootloaders.
GRUB2 (GRand Unified Bootloader) is the default boot loader for most #Linux distributions, including Ubuntu, while U-Boot and Barebox are commonly used in embedded and #IoT devices.
https://www.bleepingcomputer.com/news/security/microsoft-uses-ai-to-find-flaws-in-grub2-u-boot-barebox-bootloaders/ #ITSec
Microsoft AI Security Copilot Finds Hidden Flaws in GRUB2 and Other Bootloaders
#Cybersecurity #Microsoft #SecurityCopilot #GRUB2 #Uboot #Barebox #AI #OpenSourceSecurity #UEFI #Linux #VulnerabilityResearch
The North Koreans and Russians have been busy, Insiders abound, and attacker tradecraft continues to evolve!
Catch all this and more in our latest wrap-up of the day's news:
🗞️ https://opalsec.io/daily-news-update-monday-april-1-2025-australia-melbourne/
There are a few noteworthy stories to get across - here's the TL;DR to get you up to speed:
🕵️ North Korean Infiltration: This is way bigger than many think. DPRK nationals are landing jobs inside global companies, gaining privileged access ("keys to the kingdom" level!). DTEX reports active investigations in 7% of their Fortune Global 2000 clients, and CrowdStrike notes nearly 40% of their NK-related IR cases involved insiders. They move fast post-hire, pivoting to supply chains and installing RATs disguised as onboarding. Watch out for highly anomalous login behaviour (like days-long sessions!). Rigorous remote hiring checks (camera on, resume checks, comms style) are crucial.
🎣 ClickFix Tactics by Lazarus: The infamous North Korean group is evolving its 'Contagious Interview' campaign (now dubbed 'ClickFake' by Sekoia). They're targeting crypto job seekers (shifting focus to non-tech roles too!) with fake website/document errors ('ClickFix'). These prompt users to run PowerShell/curl commands, dropping the 'GolangGhost' backdoor. Watch out for lures impersonating giants like Coinbase or Kraken. Sekoia has shared YARA rules – definitely worth checking out.
💻 WordPress MU-Plugin Abuse: Bad actors are getting stealthy by hiding malicious code in WordPress "Must-Use Plugins" (wp-content/mu-plugins/). These execute automatically on every page load without activation, making them hard to spot. Sucuri is seeing redirects to fake browser updates, webshell backdoors fetching code from GitHub, and JS hijackers replacing content or links. Keep those instances patched, clean up unused plugins/themes, and lock down admin accounts (MFA!).
Check out what else happened in the past 24 hours, and subscribe to get each edition straight to your inbox:
📨 https://opalsec.io/daily-news-update-monday-april-1-2025-australia-melbourne/#/portal/signup
#CyberSecurity #InfoSec #ThreatIntelligence #Hacking #DataBreach #Phishing #Malware #WordPress #NorthKorea #Russia #Ukraine #AI #SecurityCopilot #GRUB2 #Bootloaders #InsiderThreat #DataProtection #CyberAttack #infosecurity #cybersecuritynews #ClickFix
So, what to do? First, enter in the 3rd OS (Open SUSE) (before going in Windows!!!) and copy the contents being in /boot/grub/grub.cfg (to use in the 2nd OS, so use some Internet or USB or whatever). Second, in the 2nd OS (Debian-like) paste those contents in a new file /boot/grub/custom.cfg (see https://forums.debian.net/viewtopic.php?p=781500#p781500, https://forums.debian.net/viewtopic.php?t=159094) And 3rd, it is possible you have to replace in that file the entries /boot with entries /@/boot (https://forums.opensuse.org/t/trying-to-dualboot-opensuse-and-linux-mint-by-adding-mint-to-opensuse-grub-but-when-selecting-entry-i-get-error-you-need-to-load-kernel-first/179906).
You can check this in the grub: press c to enter in the command line tool, press ls -l to see the partitions, and for example if (hd0,gpt1) is one of them, 'ls (hd0,gpt1)'+tab will show you the possible paths, being of the form '/boot' or being first '/@' and then '/@/boot'... (https://askubuntu.com/a/616821/830271)
Anyway, I got Open SUSE Tumbleweed installed and accessible with Debian Grub2 after all the previous afternoon+evening+night looking for a solution.
2/2
GRUB developers are preparing 73 security patches for 2025 — a major cleanup effort tackling old CVEs, long-standing issues, and security debt. Most fixes are already upstream. #SecureBoot users, keep an eye on this.
Details: https://www.phoronix.com/news/GRUB2-73-Patches-Security-2025
#Linux #Grub #grub2 #Security #OpenSource
#FOSDEM25: Booten ohne #Bootloader | heise online https://www.heise.de/news/FOSDEM-25-Booten-ohne-Bootloader-10267072.html #FOSDEM #FOSDEM2025 #Grub2 #Linux :tux: