Top 5 #Security Features of #Imunify360
Imunify360 is a Linux server security solution designed to safeguard your web-based business against cyber attacks. It includes features like Intrusion Prevention and Detection system, Real-time #Antivirus Protection, Network #Firewall and Patch Management. ...
Continued 👉 https://blog.radwebhosting.com/top-5-security-features-of-imunify360/?utm_source=mastodon&utm_medium=social&utm_campaign=mastodon.raddemo.host #businesscontinuance #intrusiondetection #intrusionprevention #wordpresssecurity #hipaacomplianthosting #webapplicationfirewall #malwareremoval #malwarescanner
#intrusiondetection
Top 5 #Security Features of #Imunify360
Imunify360 is a Linux server security solution designed to safeguard your web-based business against cyber attacks. It includes features like Intrusion Prevention and Detection system, Real-time #Antivirus Protection, Network #Firewall and Patch Management. ...
Continued 👉 https://blog.radwebhosting.com/top-5-security-features-of-imunify360/?utm_source=mastodon&utm_medium=social&utm_campaign=ReviveOldPost #malwarescanner #hipaacomplianthosting #businesscontinuance #wordpresssecurity #intrusionprevention #webapplicationfirewall #malwareremoval #intrusiondetection
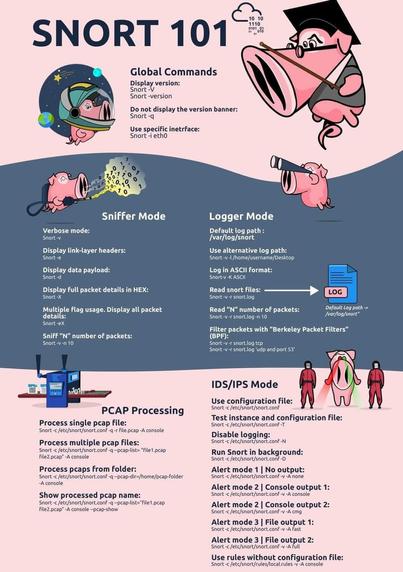
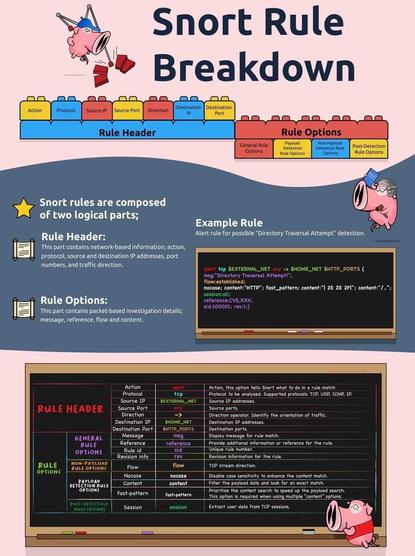
🐽 Snort Command Cheat Sheet: Understand Network Threats Like a Pro
Snort is a powerful open-source tool used for Network Intrusion Detection and Prevention (NIDS/NIPS). It's widely adopted by blue teams and security professionals to monitor, alert, and defend against malicious network activity.
🧠 Key Usage Modes (No Code Needed):
• Test Mode: Check configuration files before deployment
• Packet Sniffing Mode: Monitor live traffic and display it in real time
• Packet Logging Mode: Capture packets and store them for analysis
• IDS Mode: Analyze traffic against rule sets and raise alerts
• Silent Mode: Run in the background while logging events
🛡️ Snort is great for:
• Detecting port scans and suspicious payloads
• Monitoring traffic for policy violations
• Integrating with SIEM solutions
• Practicing blue team defensive strategies
Disclaimer: This content is intended strictly for educational and awareness purposes. Use intrusion detection systems responsibly and ethically.
#Snort #NetworkSecurity #CyberSecurity #InfoSec #BlueTeam #IDS #EducationOnly #IntrusionDetection #SOCTools #PacketAnalysis
Top 5 #Security Features of #Imunify360
Imunify360 is a Linux server security solution designed to safeguard your web-based business against cyber attacks. It includes features like Intrusion Prevention and Detection system, Real-time #Antivirus Protection, Network #Firewall and Patch Management. ...
Continued 👉 https://blog.radwebhosting.com/top-5-security-features-of-imunify360/?utm_source=mastodon&utm_medium=social&utm_campaign=ReviveOldPost #businesscontinuance #webapplicationfirewall #hipaacomplianthosting #malwareremoval #intrusionprevention #wordpresssecurity #intrusiondetection #malwarescanner
Top 5 #Security Features of #Imunify360
Imunify360 is a Linux server security solution designed to safeguard your web-based business against cyber attacks. It includes features like Intrusion Prevention and Detection system, Real-time #Antivirus Protection, Network #Firewall and Patch Management. ...
Continued 👉 https://blog.radwebhosting.com/top-5-security-features-of-imunify360/?utm_source=mastodon&utm_medium=social&utm_campaign=ReviveOldPost #webapplicationfirewall #intrusiondetection #wordpresssecurity #malwarescanner #intrusionprevention #hipaacomplianthosting #businesscontinuance #malwareremoval
Top 5 #Security Features of #Imunify360
Imunify360 is a Linux server security solution designed to safeguard your web-based business against cyber attacks. It includes features like Intrusion Prevention and Detection system, Real-time #Antivirus Protection, Network #Firewall and Patch Management. ...
Continued 👉 https://blog.radwebhosting.com/top-5-security-features-of-imunify360/?utm_source=mastodon&utm_medium=social&utm_campaign=ReviveOldPost #businesscontinuance #webapplicationfirewall #hipaacomplianthosting #malwarescanner #malwareremoval #wordpresssecurity #intrusionprevention #intrusiondetection
Top 5 #Security Features of #Imunify360
Imunify360 is a Linux server security solution designed to safeguard your web-based business against cyber attacks. It includes features like Intrusion Prevention and Detection system, Real-time #Antivirus Protection, Network #Firewall and Patch Management. ...
Continued 👉 https://blog.radwebhosting.com/top-5-security-features-of-imunify360/?utm_source=mastodon&utm_medium=social&utm_campaign=ReviveOldPost #malwarescanner #wordpresssecurity #businesscontinuance #webapplicationfirewall #malwareremoval #intrusionprevention #intrusiondetection #hipaacomplianthosting
Top 5 #Security Features of #Imunify360
Imunify360 is a Linux server security solution designed to safeguard your web-based business against cyber attacks. It includes features like Intrusion Prevention and Detection system, Real-time #Antivirus Protection, Network #Firewall and Patch ...
Keep reading 👉 https://blog.radwebhosting.com/top-5-security-features-of-imunify360/?utm_source=mastodon&utm_medium=social&utm_campaign=ReviveOldPost #intrusionprevention #wordpresssecurity #hipaacomplianthosting #malwarescanner #businesscontinuance #malwareremoval #intrusiondetection #webapplicationfirewall
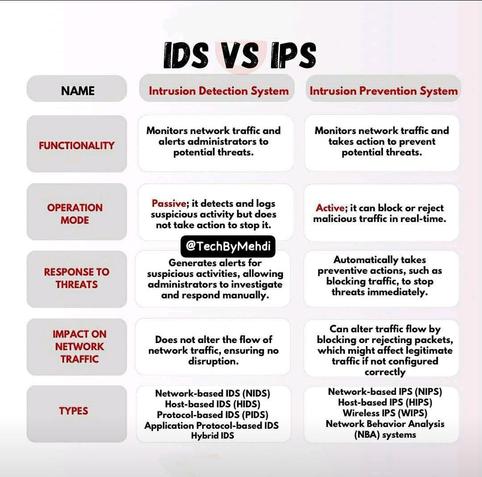
🚨 IDS vs IPS: Understanding the Key Differences in Cybersecurity 🔐
When it comes to network security, two crucial components that you’ll often hear about are IDS (Intrusion Detection System) and IPS (Intrusion Prevention System). Both are designed to protect systems from cyberattacks and malicious activity, but they operate in different ways.
#Cybersecurity #IDS #IPS #NetworkSecurity #IntrusionDetection #IntrusionPrevention #SecuritySystems
Top 5 Security Features of Imunify360
#antivirus #businesscontinuance #firewall #hipaacomplianthosting #imunify360 #intrusiondetection #intrusionprevention #malwareremoval #malwarescanner #security #webapplicationfirewall #wordpress #wordpresssecurity #Guides #ServiceAnnouncement #WebHosting
https://blog.radwebhosting.com/top-5-security-features-of-imunify360
🔢 Overwhelmed by the increasing complexity of #security systems? Don’t worry—let’s break it down in 5 key points!
Adopting integrated security systems allows for coordinated and intelligent management of #videosurveillance, #intrusiondetection, and #firesafety, simplifying operations for both end users and installers. Here’s what you need to know 👇
Link
#IntegratedSecurity #ComelitSolutions #SecurityManagement #SmartSecurity #TechSimplified #EfficientSecurity
Top 5 Security Features of Imunify360
#antivirus #businesscontinuance #firewall #hipaacomplianthosting #imunify360 #intrusiondetection #intrusionprevention #malwareremoval #malwarescanner #security #webapplicationfirewall #wordpress #wordpresssecurity #Guides #ServiceAnnouncement #WebHosting
https://blog.radwebhosting.com/top-5-security-features-of-imunify360
Do you even secure if you don't snort? 😏
#CyberSecurity #NetworkSecurity #Snort #IDS #PacketAnalysis #Infosec #IntrusionDetection #NetworkMonitoring #SecurityTools #SnortLife
For those who don't know (which is most of you), this project has been the intense focus of my work, taking up a huge amount of my time, energy, and investigative effort for the past 14 months - while still helping others at Sophos publish their research; running an election campaign where I was a candidate for school board; speaking at Blue Hat, @defcon #Saintcon, #VirusBulletin and other conferences; guest lecturing to classes at CU Boulder; volunteering my time canvassing for political candidates; serving as a docent at the @mediaarchaeologylab; working as a poll worker during the current US election cycle; and starting up the Elect More Hackers (electmorehackers.com) organization.
Whew. It's actually kind of daunting just to read that. I also sometimes sleep and eat.
@SophosXOps has been, at its core, an institution that values radical transparency, and this story (and the earlier research investigations into the Operation Pacific Rim threat actors and incidents) demonstrates Sophos' commitment to truth and journalistic integrity, following a story wherever it leads.
I hope our publication today starts a larger conversation and collaboration within the cybersecurity industry - inside and outside the Cyber Threat Alliance, which Sophos actively supports and where I am proud to represent my employer - to work together to thwart the ambitions of nation-state threat actors such as the perpetrators of Operation Pacific Rim, in order to protect the privacy and safety of everyone, everywhere.
#PacificRim #OperationPacificRim #malware #china #hacking #hacks #infosec #firewalls #intrusiondetection
Top 5 Security Features of Imunify360
#antivirus #businesscontinuance #firewall #hipaacomplianthosting #imunify360 #intrusiondetection #intrusionprevention #malwareremoval #malwarescanner #security #webapplicationfirewall #wordpress #wordpresssecurity #Guides #ServiceAnnouncement #WebHosting
https://blog.radwebhosting.com/top-5-security-features-of-imunify360
Pawel Krawczyk: DevOps guide to the galaxy of self-defending applications (Devoxx Ukraine 2019)
https://video.echelon.pl/videos/watch/99793951-d08d-4250-992a-ac0f4c10fe07
Did you miss our SysAdmin Day gift? There's still time to download your copy of 10 Terrific Tools for the Busy Admin. Special thanks to our partner #TuxCare https://mailchi.mp/admin-magazine.com/sysadmin-day-2024
#SysAdminDay #tools #security #gift #firmware #Linux #IntrusionDetection #OpenSource #utilities #admin
There is something so satisfying in kicking off an entire RFC1918 scan.
Doing a single port at a brisk but safe (for my environment) pace.
~/# nmap -Pn -n -p <single port number> -T4 --open 10.0.0.0/8
~/# nmap -Pn -n -p <single port number> -T4 --open 172.16.0.0/12
~/# nmap -Pn -n -p <single port number> -T4 --open 192.168.0.0/16
(command broken out for dramatic effect - also note that I break out each of those CIDRs into /24's so that if anything breaks, I can pick up easier where the last known good ended. It's scripted and I prefer it this way.)
I am not doing a ping sweep or a DNS resolution. I'm assuming all hosts are up. And I'm looking for every host with a single port open. So even if they dont respond to pings (or something is preventing pings), I should get an answer back.
Note, I could certainly do faster (T5 or masscan, gawd) - but this is about as fast as I'm going to do in my environment and still be safe.
Also, only looking for open ports right now - no fingerprinting yet.
A cool thing about this approach is many intrusion detection still will only look for multiple ports on a single host to trigger an alert. Some still ignore many hosts / single port scans (to their detriment).
We've long sense purple teamed this, so I sent a notification to SOC letting them know my actions and asking them nicely (I bribed them last week) to not stop me, lol.
Should take a couple weeks to a month at this pace and in my environment to hit every single one of the just shy of 18,000,000 hosts 😂
#pentesting #hacking #infosec #penetrationtesting #blueteam #redteam #intrusionDetection
Cyber threats are becoming more advanced every day, making it crucial to stay informed and prepared. Social engineering and deepfake attacks are two significant concerns that require robust security measures.
https://linuxexpert.org/cybersecurity-rising-threats-and-how-to-protect-against-them/
#Cybersecurity #SocialEngineering #DeepfakeAttacks #ZeroTrust #ContinuousMonitoring #LinuxSecurity #NetworkSecurity #OpenSourceSecurity #MFA #SecurityTraining #IntrusionDetection #OSSEC #Suricata #OpenLDAP #LeastPrivilege #GnuPG #ITSecurity #linux