http://blog.foxio.io/ja4+-network-fingerprinting
https://github.com/FoxIO-LLC/ja4
#ja4+ #blueteam #redteam
#ja4
Masz VPN, zmieniony user-agent, prywatną przeglądarkę – a mimo to serwer wie, kim jesteś?
Bo dziś identyfikacja to coś więcej niż ciasteczka. W grze są JA3, JA4, PeetPrint, fingerprinting HTTP/2 od Akamai, kolejność nagłówków, ALPN, WebGL, fonty, język systemu…
Prywatność nie kończy się na adresie IP.
#Fingerprinting #PrivacyMatters #JA3 #JA4 #PeetPrint #Akamai #CyberSecurity #DigitalIdentity #VPN #Infosec
PolarProxy 1.0.1 Released
🆔 More #JA4
🔂 Fail-open on #TLS errors
⏩ Better performance
https://netresec.com/?b=2523c96
實作更多功能的 curl-impersonate fork
從「Curl-Impersonate (github.com/lexiforest)」這邊看到的消息。
前情提要可以在「修正 Curl 的 TLS handshake,避開 bot 偵測機制」這邊看到,當時介紹了 curl-impersonate 這個專案,可以修改 TLS 的行為 (尤其是 handshake 階段),讓
#Browser #Computer #GoogleChrome #Murmuring #Network #Privacy #Security #Software #WWW #curl #fingerprint #fork #impersonate #ja3 #ja4 #tls
VirusTotal adds JA4 support!
https://blog.virustotal.com/2024/10/unveiling-hidden-connections-ja4-client.html
#VirusTotal #JA4
CloudFront 宣布支援 JA4 (更多的 fingerprint)
在「Amazon CloudFront launches support for JA4 fingerprinting」這邊看到的,Amazon CloudFront 宣佈支援 JA4。
JA3 是一套取得 TLS client fingerprint 的方式,
#AWS #CDN #Cloud #Computer #Murmuring #Network #Privacy #Security #Service #amazon #aws #cdn #cloud #cloudfront #fingerprint #ja4 #network #service #ssl #tls
FWIW the #ja4 ja4t is 8192_2-1-3-1-1-4_1260_2 from past IP's:
183.134.104.146
183.134.104.147
183.134.104.173
202.107.226.4
218.75.38.210
218.75.38.211
60.190.226.186
60.190.226.187
JA4T and JA4TS are the latest additions to the suite of JA4+ network fingerprints.
JA4T can identify intermediary proxies, VPNs, load balancers, tunneling, and fingerprint client/server OS, devices, applications and hosting/provider characteristics. When paired with additional JA4 hashes, this allows WAF tuning to focus on a set of hashes to limit false positives versus a constantly changing list of IPs. This will make a great addition to infrastructure hunting and DDoS attribution.
https://medium.com/foxio/ja4t-tcp-fingerprinting-12fb7ce9cb5a
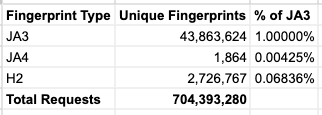
I did a very quick comparison of JA3, JA4 and H2 client fingerprinting over ~700M recent requests to our websites.
Looking at the number of unique fingerprints per fingerprint type, JA4 fingerprints are 4 orders of magnitude lower cardinality (via normalisation of fingerprint components which can be randomised by the client) than JA3 and 3 orders lower than H2.
JA4 fingerprints do appear to offer enough differentiation of clients to be useful still.
#InfoSec #JA3 #JA4 #WebDev
PSA: JA4 fingerprinting is now available on Fastly in VCL via the tls.client.ja4 variable.
Edit: ICYDK, JA4 is an evolution of JA3 fingerprinting which has better resistance to randomisation of elements of the TLS handshake client params.
https://www.fastly.com/documentation/reference/vcl/variables/client-connection/tls-client-ja4/
CapLoader has been updated to version 1.9.6.1 to fix a bug in the #JA4 fingerprint generator. The “Select similar flows” has also been improved to support UDP flows and services, which helps users to identify clusters of proprietary protocols even when CapLoader doesn’t recognize the application layer protocol.
https://www.netresec.com/?page=CapLoader
CapLoader 1.9.6 Released!
👾 More malware protocols detected
🔎 #JA4 fingerprints
🦊 Submit to @abuse_ch's ThreatFox
⚠️ Better alerts
https://netresec.com/?b=23B6bcd