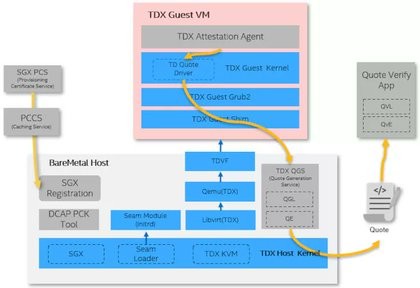
This is a great paper on the status of remote attestation of confidential VMs in public clouds. tl;dr None allow you to independently verify that you run the OS you think you run. But shoutout to AWS for having a reproducible build of their firmware! https://systex24.github.io/papers/systex24-final21.pdf #tdx #sev #aws #azure #gcp
#tdx
And, once again, "trusted computing" should not be trusted…
L. Wilke et al, "TDXdown: Single-Stepping and Instruction Counting Attacks against Intel TDX"¹
[…]
Intel recently launched Intel TDX, its second generation TEE, which protects whole virtual ma- chines (VMs). To minimize the attack surface to side-channels, TDX comes with a dedicated single-stepping attack countermeasure.
In this paper, we systematically analyze the single-stepping coun- termeasure of Intel TDX and show, for the first time, that both, the built-in detection heuristic as well as the prevention mechanism, can be circumvented. We reliably single-step TDX-protected VMs by deluding the TDX security monitor about the elapsed processing time used as part of the detection heuristic. Moreover, our study reveals a design flaw in the single-stepping countermeasure that turns the prevention mechanism against itself: An inherent side- channel within the prevention mechanism leaks the number of instructions executed by the TDX-protected VM, enabling a novel attack we refer to as StumbleStepping. Both attacks, single-stepping and StumbleStepping, work on the most recent Intel TDX enabled Xeon Scalable CPUs.
Using StumbleStepping, we demonstrate a novel end-to-end at- tack against wolfSSL’s ECDSA implementation, exploiting a con- trol flow side-channel in its truncation-based nonce generation algorithm. We provide a systematic study of nonce-truncation im- plementations, revealing similar leakages in OpenSSL, which we exploit with our single-stepping primitive. Finally, we propose de- sign changes to TDX to mitigate our attacks.
[…]
#TDX #TrustedComputing #Intel
__
¹ https://uzl-its.github.io/tdxdown/
#BSI WID-SEC-2024-3126: [NEU] [niedrig] #Intel #TDX #Module #Firmware: Schwachstelle ermöglicht Offenlegung von Informationen
Ein lokaler Angreifer kann eine Schwachstelle in Intel TDX Module Firmware ausnutzen, um Informationen offenzulegen.
https://wid.cert-bund.de/portal/wid/securityadvisory?name=WID-SEC-2024-3126
I'm still saddened by all the work that goes into supporting TDX instead of building lasting trusted computing for x86. See my earlier rants: https://x86.lol/generic/2023/06/28/intel-tdx-2.html #kvmforum #kvm #linux #tdx
#Canonical Shipping Updated #Intel #TDX Software For #Ubuntu #Linux 24.04 LTS
https://www.phoronix.com/news/Intel-TDX-2.1-Ubuntu-24.04-LTS
We should demand providing affordable #hardware for these technologies like NUC7 in the past for #SGX. IMHO, a technology should not land to the kernel in most cases, unless a college student can afford to buy at least some hardware for testing the tech in question.
I'm wondering why there is so little fuzz about this considering how much FUD was spread all over the community about #TPM's in the past.
What confidential computing would desperately need is new versions of Intel NUC (or is it now Asus NUC) and new UDOO BOLT for testing SEV-SNP.. Otherwise innovation will not exist.
#unpopular #opinion
I wrote another blog post about Intel TDX. Main points:
- You still trust the cloud vendor unless you inflict SGX-style pain on yourself.
- Our only hope are trustworthy virtualization stacks and not silver bullets from CPU vendors.
#Google researchers found multiple security issues in #Intel #TDX
https://securityaffairs.com/145268/security/intel-tdx-flaws.html
#securityaffairs #hacking
108 Patches Sent Out In Latest Revision Of #Intel #TDX KVM Support For #Linux
https://www.phoronix.com/news/Intel-TDX-KVM-v10-Patches
Original tweet : https://twitter.com/phoronix/status/1586651169082036224