Lorenzo, your book is excellent, and certainly one of best books (by far) that I've read in the last years.It is really an outstanding work.
Vulnerability Researcher | Exploit Developer | Reverse Engineer (speaker 3x at DEF CON).
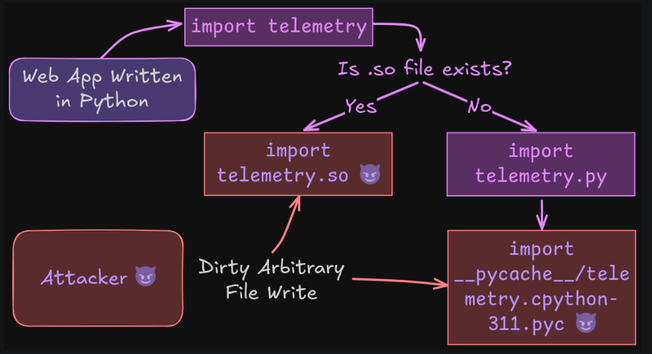
Python Dirty Arbitrary File Write to RCE via Writing Shared Object Files Or Overwriting Bytecode Files:
#python #cve #informationsecurity #rce #vulnerability #exploitation
Analysis of CVE-2024-38063 - Exploiting The Kernel Via IPv6 [EN]:
https://0xreverse.com/analysis-of-cve-2024-38063
#cve #kernel #cybersecurity #vulnerability #ipv6 #infosec #windows
Technical analysis of CVE-2025-31201: reverse engineering the diff between iOS 18.4 and 18.4.1 to study the changes made to RPAC.:
https://blog.epsilon-sec.com/cve-2025-31201-rpac.html
#iOS #apple #cybersecurity #reversing #pac #security #cve #vulnerability
DEFCON 33 CTF Write-Up Series #1: jxl4fun2 (pwn):
https://blog.cykor.kr/2025/04/DEFCON-33-Series-jxl4fun-pwn
DEFCON 33 CTF Write-Up Series #2: tinii (rev):
Unpacking APT38: Static and Dynamic Analysis of Lazarus Group Malware:
https://blog-en.itochuci.co.jp/entry/2025/03/12/140000
#apt #lazarus #informationsecurity #cybersecurity #threathunting #reversing #infosec
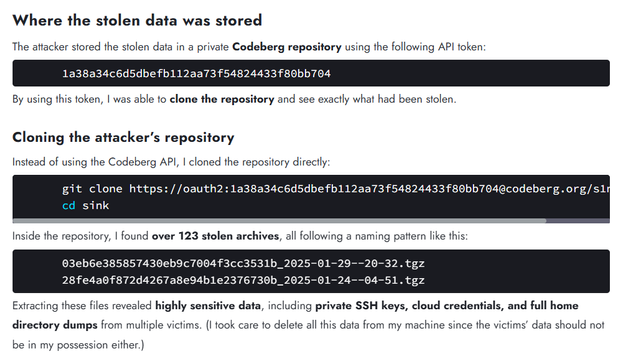
A Warning about Malicious PoCs:
https://chocapikk.com/posts/2025/s1nk/
#cybersecurity #exploit #malware #informationsecurity #hacking
CVE-2025-21299: Unguarding Microsoft Credential Guard:
#cybersecurity #microsoft #exploitation #vulnerability #infosec #credential
@kedislav Ked, I think it is possible with eventual changes or even small new procedures, but it certainly takes time. Anyway, the procedure is interesting, isn't it? Have an excellent
Unlocking secret ThinkPad functionality for emulating USB devices:
https://xairy.io/articles/thinkpad-xdci
#reverseengineering #informationsecurity #hardware #hacking #infosec #cybersecurity
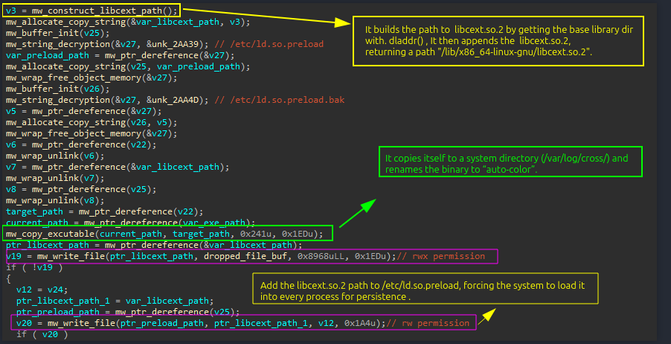
Auto-color - Linux backdoor :
https://zw01f.github.io/malware%20analysis/auto-color/
#linux #backdoor #informationsecurity #cybersecurity #redteam #malware
C++20 in Chromium (a playlist with four hours of videos):
https://www.youtube.com/playlist?list=PL9ioqAuyl6UK-d0CS7KF9ToelBJVzxrkv
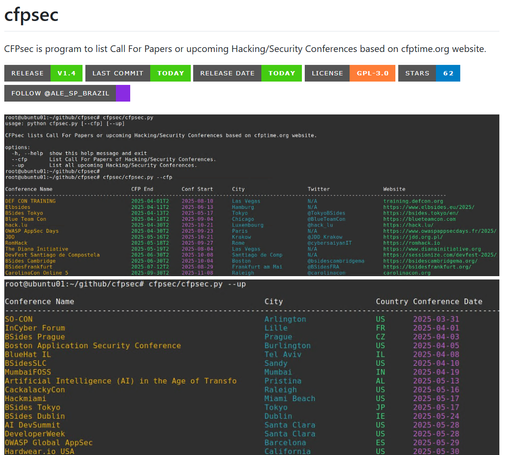
Version 1.4 of CFPsec, a simple client that lists call for papers and upcoming Hacking/Security Conferences from the command line, has been released:
https://github.com/alexandreborges/cfpsec
To install it: pip install -U cfpsec
Finally, this trivial project has been updated.
Even though I've been away from the field for years, it's great to see that a simple tool that I initially launched in 2018 and with great collaborators (Artur Marzano, Corey Forman and Christian Clauss) has been used by so many professionals.
https://www.helpnetsecurity.com/2025/03/26/malwoverview-first-response-tool-threat-hunting/
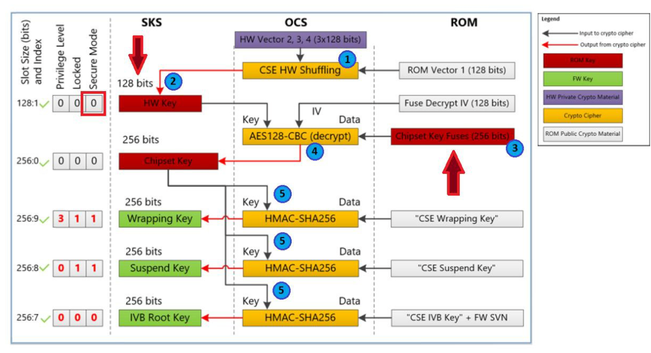
Last barrier destroyed, or compromise of Fuse Encryption Key for Intel Security Fuses:
#intel #me #reverseengineering #cybersecurity #processor #managementengine
@claushoumann Claus, your suggestion is great and yes, I do know OST and the work done by them is excellent. However, I don't consider migrate to there for multiple reasons. First of all, I've already written over 1.000 pages, which is too much and I prefer to keep writing to my own blog, which is my free space to help other professionals.. There are other points that are related to my work. For example, I have been teaching (and writing) different courses for Blackstorm Security since 2017 (private classes), and I don't have authorization to "author courses for any other place". Eventually, I could teach classes in conferences, but I have never had enough time to do it (I hope doing it this year or the next one). I've been away from conferences since 2020 (SANS) and dedicated to vulnerability research and mainly exploit development, but presenting about these topics is complicated because they are "sensitive". Therefore, the blog is still a way to balancing between my work and helping people without suffering extra pressure. By the way, Luxembourg is an amazing place to discuss about information security (I have a few friends living there), and someday I want to visit the city to speak in local conferences and interact with professionals. Thank your for your kind message, Claus. Have an excellent day.
To date, I have published 15 articles (1045 pages) with the strict goal of helping the cybersecurity community.
ERS (439 pages, so far):
[+] ERS 05: https://exploitreversing.com/2025/03/12/exploiting-reversing-er-series-article-05/
[+] ERS 04: https://exploitreversing.com/2025/02/04/exploiting-reversing-er-series-article-04/
[+] ERS 03: https://exploitreversing.com/2025/01/22/exploiting-reversing-er-series-article-03/
[+] ERS 02: https://exploitreversing.com/2024/01/03/exploiting-reversing-er-series-article-02/
[+] ERS 01: https://exploitreversing.com/2023/04/11/exploiting-reversing-er-series/
MAS (606 pages -- finished):
[+] MAS 10: https://exploitreversing.com/2025/01/15/malware-analysis-series-mas-article-10/
[+] MAS 09: https://exploitreversing.com/2025/01/08/malware-analysis-series-mas-article-09/
[+] MAS 09: https://exploitreversing.com/2024/08/07/malware-analysis-series-mas-article-08/
[+] MAS 07: https://exploitreversing.com/2023/01/05/malware-analysis-series-mas-article-7/
[+] MAS 06: https://exploitreversing.com/2022/11/24/malware-analysis-series-mas-article-6/
[+] MAS 05: https://exploitreversing.com/2022/09/14/malware-analysis-series-mas-article-5/
[+] MAS 04: https://exploitreversing.com/2022/05/12/malware-analysis-series-mas-article-4/
[+] MAS 03: https://exploitreversing.com/2022/05/05/malware-analysis-series-mas-article-3/
[+] MAS 02: https://exploitreversing.com/2022/02/03/malware-analysis-series-mas-article-2/
[+] MAS 01: https://exploitreversing.com/2021/12/03/malware-analysis-series-mas-article-1/
The blog home page is: https://exploitreversing.com/
I will be back in a few months with the next articles in the Exploiting Reversing series, which will focus on vulnerability and exploitation, once I have laid all the necessary groundwork. I'm currently taking a break from writing to focus on research.
Enjoy reading and have an excellent day.
#windows #iOS #macOS #cybersecurity #infosec #chrome #kernel #malware #reverseengineering #vulnerability #research #hypervisor
The fifth article (57 pages) of the Exploiting Reversing Series (ERS) is available on:
https://exploitreversing.com/2025/03/12/exploiting-reversing-er-series-article-05/
I would like to thank Ilfak Guilfanov @ilfak and Hex-Rays SA @HexRaysSA for their constant and uninterrupted support, which have helped me write these articles.
I hope you enjoy reading it and have an excellent day.
#hypervisor #hyperv #architecture #cybersecurity #research #internals #idapro #informationsecurity #microsoft
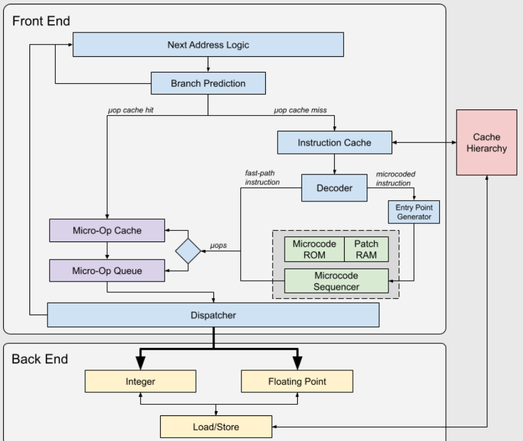
Zen and the Art of Microcode Hacking:
https://bughunters.google.com/blog/5424842357473280/zen-and-the-art-of-microcode-hacking
#processor #cybersecurity #microcode #microcodehacking #hacking #exploitation
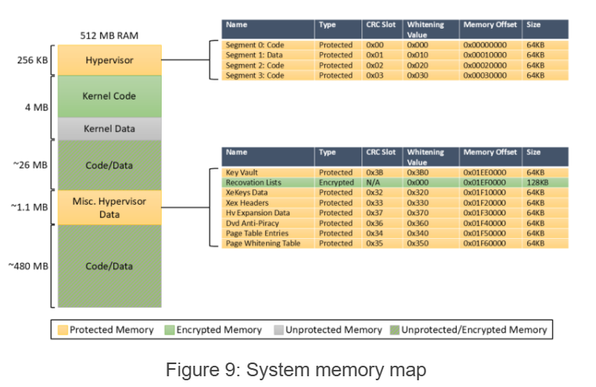
Hacking the Xbox 360 Hypervisor:
01. Hacking the Xbox 360 Hypervisor Part 1: System Overview: https://icode4.coffee/?p=1047
02. Hacking the Xbox 360 Hypervisor Part 2: The Bad Update Exploit: https://icode4.coffee/?p=1081
#hacking #exploit #exploitation #xbox #reversing #informationsecurity #hardware #cybersecurity #hypervisor