🔍 Technical Analysis: Smoke Loader Malware Leveraging Wi-Fi Access Points for Geolocation
📅 Date: August 28, 2023
🖋️ Author: Eswar
📌 Tags: #Malware #SmokeLoader #Geolocation #Wi-FiScanning #Cybersecurity
🛠️ The Smoke Loader malware, recently discovered, employs a novel technique to locate infected systems through Wi-Fi access points and Google's Geolocation API. This technical analysis sheds light on the key mechanisms used by this malware.
🔗 System Location Identification:
The malware, also known as "Whiffy Recon," utilizes a custom Wi-Fi scanning tool to identify an infected system's precise coordinates using nearby Wi-Fi access points. This is achieved by leveraging the Windows WLANSVC service and Google's Geolocation API.
🔒 Infection Process:
The malware checks the existence of the WLANSVC service, regardless of its operational status. If the service exists, the malware creates a wlan.lnk shortcut in the Startup folder pointing to the malware's original location. On the other hand, if the service is absent, the malware terminates execution.
🔄 Malware Loops:
There are two loops in the malware's execution flow:
- The first loop checks for the presence of the file %APPDATA%\wlan\str-12.bin. If valid parameters are found, the malware proceeds to the next loop for Wi-Fi scanning.
- In the absence of the file, the malware registers the bot with the Command and Control (C2) server, sending a JSON payload in an HTTPS POST request with a hard-coded UUID for bot identification.
📥 Registration and Communication:
Upon successful registration, the server responds with a secret UUID, replacing the initial bot ID for future requests. Both UUIDs are stored in the str-12.bin file. The malware then scans for Wi-Fi access points using the Windows WLAN API, sending results to Google's Geolocation API via HTTPS POST requests.
🌐 Google Geolocation API:
The Geolocation API provides system coordinates based on Wi-Fi access points and mobile network data. The obtained coordinates are integrated into a JSON structure along with encryption methods of access points. This data is sent to the C2 server through HTTP POST requests with Authorization UUID and specific URLs.
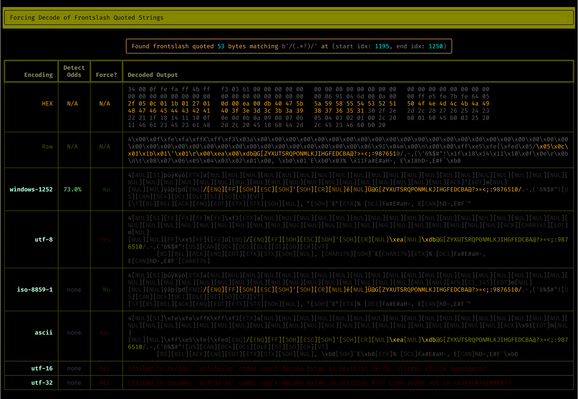
🔎 Indicators of Compromise:
Whiffy Recon sample dropped by Smoke Loader
- MD5 hash: 009230972491f5f5079e8e86e19d5458
- SHA256 hash: 935b44784c055a897038b2cb6f492747c0a1487f0ee3d3a39319962317cd4087
Whiffy Recon sample dropped by Smoke Loader
- SHA1 hash: 8532e67e1fd8441dc8ef41f5e75ee35b0d12a087
Whiffy Recon C2 server
Whiffy Recon payload URL
🛡️ Recommendations:
Cybersecurity professionals are advised to be vigilant against Smoke Loader malware and Whiffy Recon malware. Monitoring for these indicators of compromise can aid in identifying and mitigating potential threats.
Source: https://cybersecuritynews.com/smoke-loader-malware-locates-using-wi-fi/
#Cybersecurity #ThreatAnalysis #MalwareDetection #GeolocationTracking #WindowsMalware