Not only has the Frob #Atari2600 #Gamedev System for #Apple2 been #reveng, Golden Child from #MAMEDEV has emulated it in MAME!
https://youtu.be/FkfZBKysvFE
#RevEng
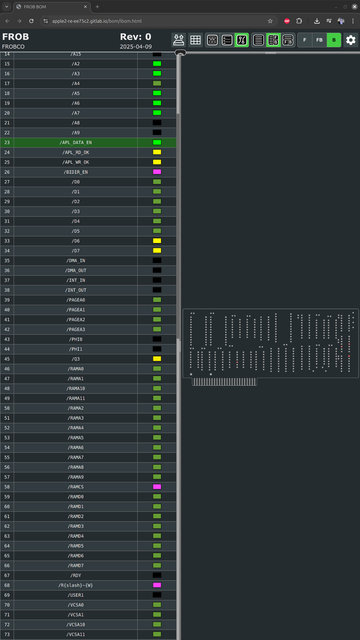
#Apple2 #Atari2600 Frob #RevEng status: mostly done. a few nets not 100% certain, so i'm pinging them out on my actual board using a multimeter in continuity mode. Thanks to Bradley Bell and Curt Sampson.
alright i just did a badass darkwavey jungle loop on the thing and it crashed and rebooted :(
the other funny thing about the #mc303 is that the #datasheet for its #cpu (#motorola iirc?) is nowhere to be found
but the datasheet for sibling models are available. one of the things i'd like to do one day is piece together that datasheet and instruction set and #reveng the mc303...
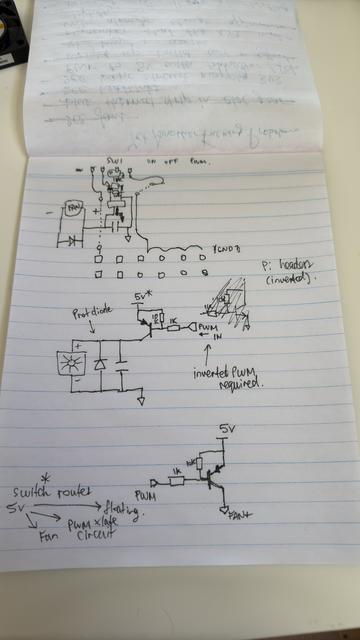
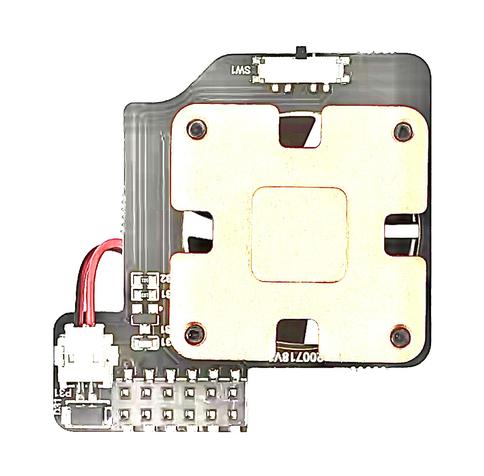
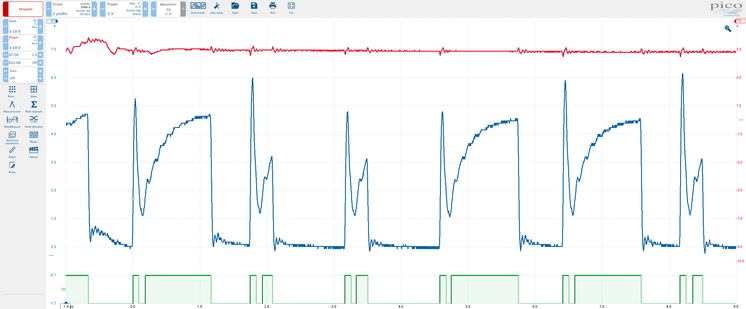
Reverse engineering designs from crappy pictures and experience... I was curious as to how this PWM fan for Pi worked and whether it would use a similar approach that I would have done. The answer: yep, pretty much. I might make it a bit more energy efficient by using a tiny mosfet instead, though. Maybe.
#reveng
#electrogirl
#electronics
Sooo … I ditched the logic analyzer and pulled out my scope and … I'm afraid I have to peel off that label again.
Because I don't know if that looks like #WS2812 to you, but it sure doesn't to me. Apparently there's a short pulse, followed by a another pulse that's either short or long. I guess that's the binary encoding.
I'm open to suggestions which #LED protocol that is.
Alt text has some more details and timings.
#RGBLED #ReverseEngineering #RevEng #electronics #RGBIC #protocol
Strange electronic devices that you have partially reverse engineered should have a label explaining why they are strange electronic devices and what you have reverse engineered.
#electronics #LED #RGBLED #RGBIC #WS2812 #WS2812B #ReverseEngineering #RevEng
@sustainoss with @richlitt
One idea to explore further from today's Sustain Together meeting:
A legal defense fund and team to fight against take-downs of legal reverse engineering discoveries.
#RightToRepair #DigitalRights #RevEng #OpenSource #Law #Interoperability #i14y
@neil
It is *always* worth searching around to see if someone, somewhere has already done just what you describe - especially after a device goes EOL.
I think we're going to see a lot more citizen-level reverse engineering projects bare fruit, as the #enshittification epidemic spreads like #covid.
We're fed up, and those of us who have the skills and time to do these kinds of projects, *are*.
I know I am.
I just saw a guy #reveng his Phillips electric toothbrush. Another replaced the controller board of an otherwise unusable video router with his own microcontroller and code. Tip of the iceberg.
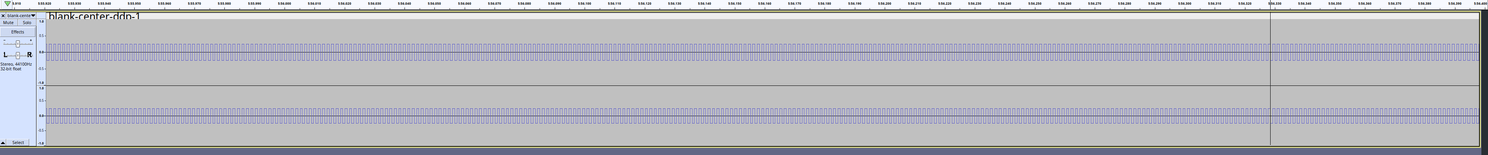
#ColecoAdam A few weeks ago, I posted how to use #MAME's castool utility to generate a .WAV file containing the formatting tracks for a center directory DDP.
When recorded to an actual data pack, e.g. in an audio tape deck, this can rejuvinate a degraded tape (it will however delete any existing data) WITHOUT THE NEED FOR A DONOR TAPE.
I will be recording a video shortly showing the entire process of constructing the blank DDP image, the WAV file, and recording the WAV file using a USB enabled audio cassette player.
Hopefully this will be a great preservation boost for data packs, both factory and third-party alike.
I feel horrible even attempting to pull every string I may or may not have, but...
I have a #GRiDCASE 1537 that was govt surplus. It malfunctioned, and Curt Vendel offered to fix it. After almost 5 years, I got it back, but it's in pieces, and am looking for some1 to fix it.
This is a tall order, because the schematics for this thing are classified, and will require someone versed in hardware #reveng to do it.
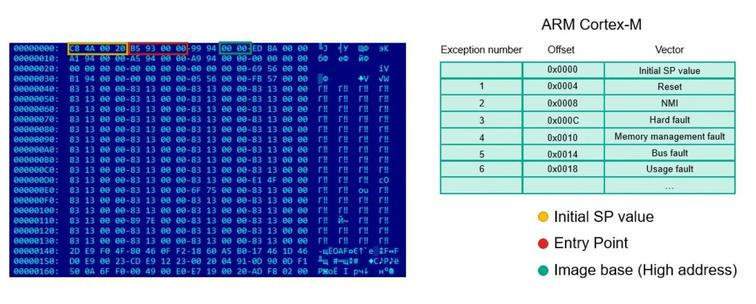
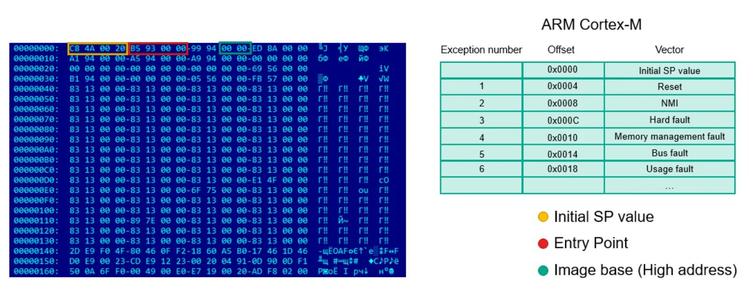
On reverse engineering the firmware of the Cortex M0 microcontroller used by PS4 counterfeit gamepads
https://securelist.com/hacking-microcontroller-firmware-through-a-usb/89919/
#reveng #infosec #cybersecurity #hacking #microcontroller #ps4
What is a good place to find schematics of PCBs found in off-the-shelf, big brand routers, IoT-devices, set top boxes etc?
Really loving the @binaryninja plugin highlights. So many cool tools and plugins to try!
Nice analysis of "Salt Lake 2002".
The InstallShield script memcheck nonsense is a classic, but then going on to estimate VRAM by filling it up with dummy objects only to not use the result is truly next-level. #SaltLake2002 #reveng #gamehacking
Live at https://www.twitch.tv/cyberkaida ! Today we're looking at datatypes in Ghidra and how to extract them from one binary and apply to another! 👩💻🐉
This is really useful when working with common libraries and makes RE much easier! ✨
Come hang out!
Dear #hackaday #Berlin: unturned, I could not attend. Where can I find out more about "openepaperlink" (infrastructure) and those e-ink/e-paper displays? @Atc1441 have you been involved? Could this system be used to send notifications during a camp over a campsite on the outside? It seems as I guess that this has been used during the conference to "spread" the schedule/ next talks, right?
I started to build a simulator of u-blox 6 serial communication protocol (UBX) used by u-blox GPS receiver modules. It's quite dumb at the moment. Support for generating location and other data may be added.
https://github.com/maehw/ubx-gps-simulator
#gps #simulator #embedded #reveng #ublox #receiver #uart #ubx #foss
"Reversing UK mobile rail tickets"
https://eta.st/2023/01/31/rail-tickets.html
"But what data is inside the barcode of a mobile ticket, and how do they work? Could people who aren’t ticket inspectors get the data out of them? It turns out that the answer is a bit more interesting than I initially expected!"
#reversing #reverseengineering #reveng #hacking #mobileticket #barcode #itsec #decompilation #decompile
Yesterday I've learned what USB filter drivers are on Windows and that it's apparently pretty easy to install libusb0 as one. (Thanks @patagona)
Having done that, my initial plan worked on the second try. I can now send the command for switching the color palette, wohoo \o/
I only needed to make sure that I send the USB control transfers after the video capture has already been started, otherwise the call to #libusb will just hang indefinitely for whatever reason.
Great blog post by Boris Larin on reverse engineering microcontroller firmwares.
The case of a Cortex M0 used by PS4 counterfeit gamepads.
https://securelist.com/hacking-microcontroller-firmware-through-a-usb/89919/
#reveng #infosec #cybersecurity #hacking #microcontroller #ps4