Eric Schmidt, former Google CEO, said the current AI boom is unlikely to collapse like the dot-com bubble, citing investor confidence in long-term returns, but warned of security vulnerabilities and the need for global cooperation to prevent misuse.
#YonhapInfomax #EricSchmidt #Google #ArtificialIntelligence #AIBubble #SecurityVulnerabilities #Economics #FinancialMarkets #Banking #Securities #Bonds #StockMarket
https://en.infomaxai.com/news/articleView.html?idxno=84968
#securityvulnerabilities
Computer motherboard hardware and software must be so full of security vulnerabilities and backdoors.
#motherboards #securityvulnerabilities #rootkits #computersecurity #computerviruses #viruses #trojans #bios #uefi #bootsector #backdoors #proprietarysoftware #firmware #closedsourcesoftware
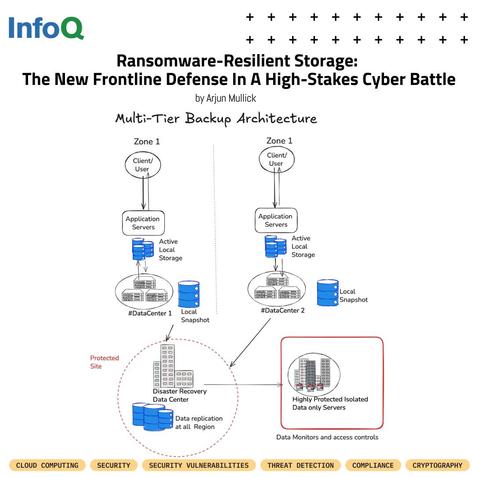
⚠️ As #Ransomware attacks grow in frequency, scale, and sophistication, endpoint security & reactive backups are no longer enough.
🔐 Defense has moved beyond traditional antivirus - the new focus is the storage layer:
✅ Immutable backups
✅ AI-powered detection
✅ Isolated vaults
📰 Read the #InfoQ article by Arjun Mullick (Engineering Manager, Meta): https://bit.ly/4623E3x
#CloudSecurity #ThreatDetection #AI #SecurityVulnerabilities
Perplexity’s Comet AI browser is making headlines for all the wrong reasons—tricked into clicking phishing links and even putting orders on fake sites. Can our smart tech really stay one step ahead of cyber crooks?
https://thedefendopsdiaries.com/security-challenges-in-perplexitys-comet-ai-browser/
#ai
#cybersecurity
#phishing
#securityvulnerabilities
#promptinjection
🚨 A Security Nightmare?
AI-powered developer tools built on the #ModelContextProtocol (MCP) are introducing critical #SecurityVulnerabilities like:
➡️ Credential leaks
➡️ Unauthorized file access
➡️ Remote code execution
Details on #InfoQ: https://bit.ly/3Jako0A
Where and How is your Website Hosted?
websites are more than virtual entities; they are anchored by physical servers across the globe. This preface illuminates the journey from domain registration to server allocation, bridging the gap between virtual and physical realms of web hosting.
https://hertfordshirewebdesign.com/where-and-how-is-your-website-hosted/
#WebHosting #PhysicalServers #ServerAllocation #HostingOptions #SharedHosting #VPSHosting #DedicatedHosting #CloudHosting #HostingProviders #ServerMaintenance #SecurityVulnerabilities
A tiny metadata error turned a routine Windows update into a security headache—delaying critical patches and leaving systems exposed. What went wrong, and how are IT pros fixing it? Check out the details.
#windowsupdate
#metadataerrors
#cybersecurity
#securityvulnerabilities
#itmanagement
Docker launches #DockerHardenedImages (DHI) – a security-focused set of base images designed to cut vulnerabilities by up to 95%.
Using a #distroless approach, DHI removes unnecessary components, supports automatic patching, and remains compatible with existing Dockerfiles.
🔎 More on #InfoQ: https://bit.ly/4nfy3TB
4chan Restored After Hackers Exploited Years of Neglected Tech Debt
#CyberSecurity #4chan #DataBreach #Hacked #Outage #TechDebt #Ghostscript #Moderator #Privacy #InfoSec #SoyjakParty #SecurityVulnerabilities
🇬🇧 #Cybercrimeinfo #Newsletter361 provides updates on #cyberthreats, #securityvulnerabilities in #VMware and #WordPress, #ransomware trends, #policeactions, #cryptomoneylaundering, and #darkweb dangers.
https://www.walknews.com/791606/ Appleの最新世代CPUに新たなサイドチャネル脆弱性が影響 – InfoQ #Apple #AppleCpuSideChannelSlapFlop #DevOps #Science #Science&Technology #SecurityVulnerabilities #Technology #セキュリティ #テクノロジー #デベロップメント #科学 #科学&テクノロジー
Went on @trtworld over the weekend to provide live commentary on the Crowdstrike global IT outage on the Newshour programme and explain why it isn't an easy fix, as well as why we really should be looking at Microsoft to make changes in order to avoid this happening again. Thanks for the chat Maria Ramos!
Here's a clip from the segment, you can watch the full video here 📹:
https://www.youtube.com/watch?v=NNDg52RPhMY
#Crowdstrike #Crowdstrikeoutage #Microsoft #IToutage #bigtech #kernel #cybersecurity #securityvulnerabilities #technologynews
It looks like it might be time to replace the network gear. I hate #unifi and the #uniquity platform (named for the ubiquitous #securityvulnerabilities) but I couldn't exactly afford to rip it all out and replace it. That is, until they EOLd the fancy "enterprise-class" gateway I bought 3 years ago. In proper #unifi style it was never actually capable of the enterprise-class features they promoted, but that doesn't mean I'm not using it anyway.
Some quick examples from my 'prosumer' home use. If you turn on traffic inspection, the total throughput drops to about 30%. If you want to add (or disable, or rename) a firewall rule you can expect 5 minutes of reloading where connectivity sometimes just goes spinning beachball.. And I'm not getting into the terrible no good web interface, the increasing push towards monthly subscriptions, or what a mess the guest network setup is.
The only 'enterprise' feature that actually functions is the WAN failover. It doesn't support custom routes or anything, just a choice of 50/50 or failover, but it works.
The question is, do I buy the replacement gateway? It isn't the cost, the thing is cheap, but I just don't want to keep encouraging them. Supposedly the new one can do everything the enterprise one originally claimed, except for the only feature that actually worked.. :rick: (It doesn't do failover, but I only had failover for like a month anyway before elmo went nuts and we cancelled.)
#networking #wifi #selfhosting
Have clients that are still on Ruby versions well beyond #EOL (end-of-life)? For some of them, it may be a lack of budget, staff, or skills to perform system-wide upgrades. Performing #majorVersionUpgrades can be hard, but opening yourself up to known #securityvulnerabilities is more costly in the long run.
If you're still on an old Ruby version, it's past time to upgrade. It's well worth the effort from both a security and a performance perspective!
#Cloudflare, Google & #AWS revealed a new zero-day vulnerability known as the "HTTP/2 Rapid Reset" attack: https://bit.ly/40xtSYA
This attack exploits a weakness in the #HTTP2 protocol to generate enormous #DDoSAttacks, up to almost 400 million rps.
Stay informed with #InfoQ!
Dive into the lessons learned from three major #opensource security events:
1️⃣ The Equifax breach via Struts
2️⃣ The Log4j vulnerabilities
3️⃣ The Spring4Shell exploit
#InfoQ video with #transcript included: https://bit.ly/3EXsy7p
✅Hear about prevention security strategies that help build a more secure solution in the cloud.
✅Learn how to address some security issues as prevention measures rather than having them develop as painful problems.
#InfoQ video by Travis McPeak: https://bit.ly/44Wmw1f
#transcript & Q&A included
⚠️ Beware of "alert fatigue" in your security processes!
Learn why integrating #SoftwareCompositionAnalysis in your CI/CD pipeline is crucial for safeguarding your software from vulnerabilities: https://bit.ly/3LnT6Ci
#InfoQ article by Lukáš Křečan
DeepSec 2023 Talk: Zero-Touch-Pwn: Abusing Zoom’s Zero Touch Provisioning for Remote Attacks on Desk Phones – Moritz Abrell
Cloud communication platforms like Zoom have become a fundamental aspect of modern communication and
https://blog.deepsec.net/deepsec-2023-talk-zero-touch-pwn-abusing-zooms-zero-touch-provisioning-for-remote-attacks-on-desk-phones-moritz-abrell/
#Conference #DeepSec2023 #DesktopPhone #RemoteAttacks #SecurityVulnerabilities #Talk #Zoom #ZoomZeroTouchProvisioning