I've got a quick favour to ask. If you're reading this post on Mastodon (or the Fediverse), please click boost.
How come?
I recently moved across to my own self-hosted single-user server (using GoToSocial.org). For a bunch of reasons, including visibility across the Fedi, it would really help out.
#Fediverse #FediHelp #gotosocial #mastohelp
Infosec enthousiast since 1999, Threat Intelligence & Hunting, Hacking, Sci-Fi, Astrophotographer (beginner), petrol head, husband, dad of 2, hybrid personality, little weird, loves life.
@GossiTheDog 🤣🤣🙏🏼👌🏼
Northern lights over Ramsele, Sweden
Hobby update! 🔭🛸👾
Last week some clear nights; and with my second set I didn’t knew what to target and shoot. So kinda was hopping around and found this very very very faint target. Didn’t knew what it was; had to look it up.
Ultimately I had to do 600 second and 1200 second 🫣 subs. Yeah. That’s 20 minutes for one shot. And that a challenge I didn’t tackle before.
But. Here she is: CTB-1 Supernova remnant in HOO (Garlic Nebula)
William Optics RedCat 61 WIFD
ZWO AM3, ZWO EAF, ZWO ASI 120MM mini, ASIAir Pro
69x 600" @ Gain 252 -10c
21x1200" @ Gain 252 -10c
20 Flats + darkflats
40 Darks (600/1200")
Updated. Entire post edit proces redone, I messed up previously. Sorry 😆
NGC 1907 - NGC 1931 - IC 417 some hydrogen alpha violence. #astrophotography #space #deepsky #astro -updated edit
NGC 7822 is a young star forming complex in the constellation of Cepheus. The complex encompasses the emission region designated Sharpless 171, and the young cluster of stars named Berkeley 59.
3 nights with the ZWO FF80 and ASI2600mc pro. #space #astronomy #astrophotography #astro #astronomie
The best nights are the ones spent under clear skies!🥰
Can anyone spot the space saucepan in the second photo?!
Where's your happy place?
#Astrophotography #Astro #Space #Stars #SelfCare #Photography
Over the past few nights, I’ve been running the RedCat with the ASI2600MC exclusively on IC 443, with the Monkey Head Nebula also in the frame. The nebula is processed in HOO (extract) using the APP RGB Combine process, while the stars were handled separately in pure RGB.
Dates: February 16–19, 2025
Sub-frames:
-Altair Ha Oiii DualBand ULTRA 4nm CERTIFIED CMOS Filter 2": 191×300″ (15h 55′) (gain: 100) at -10°C
-Optolong L-Quad Enhance 2": 13×300″ (1h 5′) (gain: 100) at -10°C
Total Integration: 17h
Calibration Frames:
Darks: 20
Flats: 20
Flat Darks: 20
Bias: 30
Processing followed my usual PixInsight flow, but after a NoiseX Light pass, I focused on TGVDenoise in CIE Lab* mode using an inverted lightness mask (see this guide). Final tweaks to the stars and composite were done in Photoshop. Edited on a BenQ in P3 with final checks in sRGB (P3 shows deeper reds, by the way). #astronomy #astrophotography #space #deepspace #pixinsight
Here’s the result so far:
Orion m42; arcsinh stretched in hdr. Core re-edit and some other results of short and long exposures. #astrophotography #space #OrionNebula #m42
Link to hi-res version: https://www.astrobin.com/musswp/
M42 Orion Nebula, Running man, Horse head etc in a 2-panel mosaic - HDR processed. #astrophotography #space #hobby #OrionNebula
Hacker infects 18,000 "script kiddies" with fake #malware builder
Tl:dr “there is no honour among thieves” 🥹
A threat actor targeted low-skilled hackers, known as "script kiddies," with a fake malware builder that secretly infected them with a backdoor to steal data and take over computers.
Security researchers at CloudSEK report that the malware infected 18,459 devices globally, most located in Russia, the United States, India, Ukraine, and Turkey.
"A trojanized version of the #XWorm #RAT builder has been #weaponized and propagated," reads the CloudSEK report.
I do this, in a safe way, internally as well. Typical action ofc is a #rickroll 😆
While I am at it anyway; #Phishing meets #SMB: Exploiting network trust to capture #NTLM hashes (#pentesting fun)
One effective phishing method leverages SMB connections to capture #NetNTLM hashes for offline #cracking, providing attackers with credentials for the next phase (for example social engineering or other tech attacks). Oh; BIT B.V. (bit.nl) did send my a set of abuse mails, … sorry 😆 … but very nice and thx 🙏🏼, anyway;
Exploit Path: Initial Phishing Vector: The attack starts with a phishing email or download website or something something, containing a payload (e.g., a malicious document or shortcut file, whatever, choose your poison).
The payload initiates an SMB request to the attacker-controlled server (`\\<C2IP>\share`), tricking the victim’s system into authenticating with it. Modern browsers like edge won’t fly; you need to get a bit more creative to execute this and no it’s not a hyperlink. Think Java. Or macro (although; meh).
Then we have SMB Request Redirection: Tools like Responder on the attacker’s C2 server capture NetNTLMv2 hashes during these authentication attempts. This works over IPv4 and IPv6, with IPv6 often prioritized in networks and less monitored. Hence #mitm6. But that’s another story.
Captured hashes are cracked offline using tools like #Hashcat, potentially giving credentials for further attacks. It’s also an excuse for my new RTX 5090 card. 😉
Observations from recent penetration tests where I executed this attack;
-Firewall Rules: not excisting … at all. 🥹
Many environments have outbound 'any-any' rules on firewalls, even on critical nets like Citrix farms. This unrestricted outbound traffic allows SMB authentication requests to reach attacker-controlled servers on the internet. And there is something with remote workers and open internet access lately…
-#Azure and #2FA Gaps, here we go again (see https://lnkd.in/g2ctMEDG); 2FA exclusions are another common issue:
- Trusted locations (e.g., `192.168.x.x` or specific IP ranges) configured to bypass 2FA/MFA.. intended to improve usability, such exclusions can be exploited once an attacker gains access to these "trusted" locations; simply put a VM inside a 192.168 range and chances are…. Good.
These misconfigurations reduce the effectiveness of otherwise robust security measures like MFA and firewall segmentation, giving attackers unnecessary opportunities.
The Takeaway: Attackers thrive on overlooked gaps in configuration. Whether it's outbound "any-any" firewall rules or MFA bypasses for trusted locations, these lapses provide unnecessary pathways for compromise. By combining phishing, SMB exploitation, and tools like Responder, we can target foundational weaknesses in even hybrid environments. I’ve seen soc’s only respond after mission target; because most are monitoring just on the endpoint (EDR/XDR), poorly.
#CyberSecurity #Phishing #SMB #NTLM #MFA #FirewallSecurity #infosec
The meme is absolutely intended as shitposting. Sorry 🤣
A plunge into darkness
I was drawn by the sense of mystery this river gave me, falling between the black, rugged rocks, glistening in contrast with the fog hovering above the deep valley beneath my feet.
I was in a dark place at that time and it felt like an introspective journey into the mysteries that lie hidden in the darkness of my soul
#photography #landscapephotography #blackandwhite #nikon #fineart
Combining a good write up in #aitm and #entra and recent real-world-attack scenarios. Moving forward on my previous post tabout legacy #MFA (debatable, again… can’t stress this enough). I keep seeing (and exploiting) not very well configured #EntraID environments but I sadly lack the time to do a full write up at the moment. But it’s not new and all known material…. Anyway, summarized (the lazy way): here’s a combined post integrating the Adversary-in-the-Middle (AiTM) #2FA phishing attacks with the #Microsoft Entra write-up on attacking Entra, where AiTM Phishing adds a new dimension 🔭👾
SpecterOps recently published a two-part series detailing attacker methodologies targeting #Microsoft #Entra environments, with a focus on the synchronization between Active Directory (AD) and EntraID. Coupled with evolving Adversary-in-the-Middle (AiTM) phishing kits, attackers now have a broader arsenal to exploit hybrid identity setups.
Hybrid Identity Risks: A Multi-Pronged Attack Vector
The Entra Connect Sync’s “#metaverse” aggregates data from AD and Entra ID. Any key materials, like Windows #Hello for Business or #FIDO2 keys, added to an Entra user are synchronized to the on-premises user's `msDS-KeyCredentialLink` attribute. This synchronization means that compromising an Entra user (via AiTM phishing) could lead to the compromise of their corresponding on-premises identity.
AiTM #phishing kits like 'Sneaky 2FA' intercept real-time 2FA codes and credentials, bypassing MFA protections. Using these stolen credentials, attackers could gain access to Entra accounts, potentially elevating privileges or manipulating synchronization accounts.
Cross-Domain Attacks: Once an attacker has access to a synchronization account in one domain, they could manipulate credentials or attribute flows across connected domains in the same Entra tenant, leveraging trust relationships to expand their foothold.
Key Takeaways:
- AiTM and Hybrid Identity Synergy: AiTM phishing attacks offer attackers an efficient method to bypass MFA, securing entry into Entra ID. Once inside, hybrid identity synchronization can be exploited to compromise on-premises accounts or propagate attacks across domains.
- Trust Boundary Risks: The Entra tenant serves as a central trust boundary. A breach in one domain, facilitated by AiTM phishing or other techniques, can impact all domains under the tenant.
- Proactive Defense:
- Use phishing-resistant MFA methods (e.g., hardware security keys).
- Monitor for unusual authentication patterns in both cloud and on-premises environments.
Hybrid identity environments are critical to modern organizations but can also amplify risks when combined with advanced phishing tactics like AiTM. Protecting against these evolving threats requires a layered, adaptive defense strategy.
I haven’t fully exploited the entire attack path, so feel free to share anything.
*sorry for the typos, should have used AI 🤣 meh
Source on attack; https://thehackernews.com/2025/01/new-sneaky-2fa-phishing-kit-targets.html?m=1
Sources on the write up:
https://posts.specterops.io/attacking-entra-metaverse-part-1-c9cf8c4fb4ee
and part 2
https://posts.specterops.io/entra-connect-attacker-tradecraft-part-2-672df0147abc
A flaw in the W3 Total Cache plugin exposes hundreds of thousands of #WordPress sites to Attacks
https://securityaffairs.com/173219/security/w3-total-cache-wordpress-plugin-cve-2024-12365.html
#securityaffairs #hacking
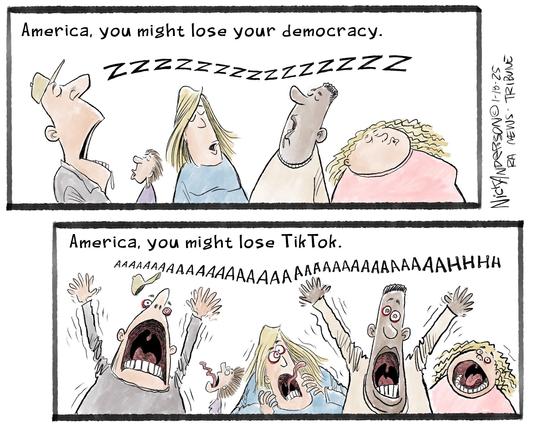
Tiktok, by Nick Anderson.
Oh… #privacy where.. oh, wait .. 🥹
Massive breach at #location data seller: “Millions” of users affected
Like many other #data #brokers, #Gravy is a company you may never have heard of, but it almost certainly knows a lot about you if you’re a #US #citizen.
Gravy Analytics specializes in location intelligence, meaning it collects #sensitive #phone location and #behavior data.
One of the buyers is the US #government who increasingly circumvents the need to get a #warrant by simply buying what they want to know from a data broker. Ironic, given that the #FTC sued Gravy Analytics after saying it routinely collects sensitive phone location and behavior data without getting the #consent of #consumers.
And now, apparently, it’s Gravy Analytics’ turn to be #breached. According to 404 Media, #cybercriminals breached Gravy Analytics and stole a massive amount of data, including customer lists, information on the broader industry, and location data harvested from #smartphones which show peoples’ precise #movements.
The cybercriminals claim to have stolen 17TB of data and are threatening to publish the data. Considering the sensitivity of location data for some groups, this breach could potentially be just as significant as the National Public Data leak.
The whole ordeal, whether the data will be published or not, proves once again why data brokers should stop trading health and location data. 📊
NGC 1499 (aka California nebula) is an emission nebula visible in the constellation Perseus. The bright star is Menkib (Xi Persei), visible to the naked eye. 25h cumulated exposure from my backyard, in the north of Montpellier (south of France).
More technical details: https://www.astrobin.com/wha8qc/