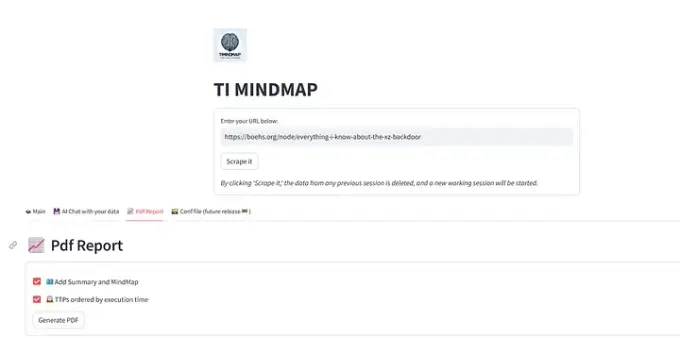
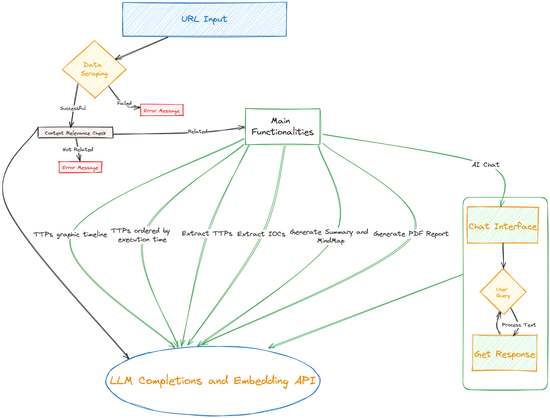
How GenAI can be used to transform 𝐮𝐧𝐬𝐭𝐫𝐮𝐜𝐭𝐮𝐫𝐞𝐝 𝐜𝐲𝐛𝐞𝐫 𝐭𝐡𝐫𝐞𝐚𝐭 𝐫𝐞𝐩𝐨𝐫𝐭𝐬 𝐢𝐧𝐭𝐨 𝐒𝐓𝐈𝐗 2.1 𝐛𝐮𝐧𝐝𝐥𝐞𝐬
https://medium.com/@antonio.formato/from-unstructured-threat-intelligence-to-stix-2-1-bundles-with-generative-ai-1065ce399e63
GitHub: https://github.com/format81/GenAI-STIX2.1-Generator/
#threatintelligence #GenAI #stix #timindmap #openai #llm #cyber #Security #CyberSecurity
(🧵 2/2) Resources 📚
Code 🔗: https://github.com/microsoft/graphrag
Documentation 📖: https://microsoft.github.io/graphrag/
Release notes 📝: https://www.microsoft.com/en-us/research/blog/graphrag-new-tool-for-complex-data-discovery-now-on-github/
(🧵1/2) Data discovery with GraphRAG 🚀
Microsoft open-sourced this week GraphRAG, a Python library for extracting insights from unstructured text using LLMs. The GraphRAG uses LLM-generated knowledge graphs to extract information and answer questions from private datasets and documentation.
Installation 🛠️: 𝘱𝘪𝘱 𝘪𝘯𝘴𝘵𝘢𝘭𝘭 𝘨𝘳𝘢𝘱𝘩𝘳𝘢𝘨
License 🪪: MIT 🦄
🔈Monthly release of 𝐖𝐡𝐚𝐭'𝐬 𝐧𝐞𝐰 𝐢𝐧 𝐓𝐈 𝐌𝐢𝐧𝐝𝐦𝐚𝐩 | 𝐌𝐚𝐲 2024. 🔈
Article and tool co-authored with Oleksiy Meletskiy.
📢 New Features:
➡𝐖𝐫𝐢𝐭𝐞-𝐮𝐩 𝐬𝐜𝐫𝐞𝐞𝐧𝐬𝐡𝐨𝐭
➡𝐕𝐢𝐫𝐮𝐬𝐓𝐨𝐭𝐚𝐥 𝐈𝐎𝐂𝐬 𝐞𝐧𝐫𝐢𝐜𝐡𝐦𝐞𝐧𝐭
➡𝐄𝐦𝐛𝐞𝐝𝐝𝐞𝐝 𝐌𝐈𝐓𝐑𝐄 𝐀𝐓𝐓&𝐂𝐊® 𝐍𝐚𝐯𝐢𝐠𝐚𝐭𝐨𝐫
➡𝐏𝐃𝐅 𝐫𝐞𝐩𝐨𝐫𝐭 𝐢𝐦𝐩𝐫𝐨𝐯𝐞𝐦𝐞𝐧𝐭𝐬
📰𝐁𝐥𝐨𝐠: https://lnkd.in/dgTnd-uD
💻 𝐀𝐩𝐩: https://lnkd.in/dSVdG2B4
⏩ 𝐆𝐢𝐭𝐇𝐮𝐛: https://lnkd.in/dJDSQx8Y
𝐇𝐨𝐰 𝐭𝐨 𝐠𝐞𝐭 𝐢𝐧𝐯𝐨𝐥𝐯𝐞𝐝
The project is open to external contributions.
To collaborate, please check the GitHub repository: https://lnkd.in/dJDSQx8Y
If you find TI Mindmap useful, please consider starring ⭐ the repository on GitHub.
hashtag
#timindmap #ti #mindmap hashtag#mistral #ai #mistralai #threatintelligence #llm #llmapp #openai #azureopenai #largelanguagemodel #cybersecurity #cyber #security #python #streamlit #infer #embedding #chat #ioc #mitre
#ttp #cyberreport #report #mermaid #genai #generativeai #cyberthreatintelligence #github #prompt #promptengineering #FewShotPrompting #gpt hashtag#gpt4 #api #DataVisualization #threat #infosec #threatreport hashtag#oai #analyst #soc #cert #thumbnail #virustotal #stix #GPTo
🌟 Excited to announce that I'll be presenting a talk at 𝐁𝐒𝐢𝐝𝐞𝐬 𝐀𝐭𝐡𝐞𝐧𝐬 on June 29th! 🌟
🎤 Title of the talk: "𝐅𝐫𝐨𝐦 𝐃𝐚𝐭𝐚 𝐃𝐞𝐥𝐮𝐠𝐞 𝐭𝐨 𝐀𝐜𝐭𝐢𝐨𝐧𝐚𝐛𝐥𝐞 𝐈𝐧𝐬𝐢𝐠𝐡𝐭𝐬 𝐰𝐢𝐭𝐡 𝐋𝐋𝐌𝐬: 𝐈𝐧𝐭𝐫𝐨𝐝𝐮𝐜𝐢𝐧𝐠 𝐓𝐈 𝐌𝐢𝐧𝐝𝐦𝐚𝐩"
📜 I'll introduce TI Mindmap, an open-source project designed to empower Infosec professionals in navigating the complexities of Threat Intelligence write-ups. I'll explore how TI Mindmap leverages the capabilities of LLMs to enhance the efficiency of processing and extracting crucial information from a variety of Threat Intelligence sources.
Key Features of TI Mindmap:
▶Summarizing Threat Intelligence articles
▶Mapping entity relationships with Mindmaps
▶Engaging in AI-driven chats on your data
▶Generating comprehensive PDF reports
▶IOCs extraction
▶Extract adversary tactics, techniques, and procedures
▶TTPs by execution time
During the session, I'll not only showcase the capabilities of TI Mindmap but also share insights from development journey. I'll discuss the challenges we've encountered, the lessons we've learned, and the future directions of this open-source project.
🔗 Learn more about TI Mindmap, GitHub Repository: https://lnkd.in/dJDSQx8Y
BSides Athens: https://www.bsidesath.gr/
Tracks: https://lnkd.in/dC9znupr
#BSidesAthens #Cybersecurity #ThreatIntelligence #OpenSource #LLMs hashtag#AIdriven #TIMindmap #streamlit hashtag#mermaid #mindmap #TI #genai #python #mistral #openai #azureopenai #stix #ttp #conference #bsides
𝐆𝐞𝐭𝐭𝐢𝐧𝐠 𝐬𝐭𝐚𝐫𝐭𝐞𝐝 𝐰𝐢𝐭𝐡 𝐌𝐢𝐜𝐫𝐨𝐬𝐨𝐟𝐭’𝐬 𝐏𝐡𝐢-3 𝐨𝐧 𝐎𝐥𝐥𝐚𝐦𝐚
My initial journey into Small Language Models
https://medium.com/@antonio.formato/getting-started-with-microsofts-phi-3-on-ollama-c4e50be1e52d
#genai #ollama #phi3 #microsoft #smalllanguagemodel #sml #llm #language #reasoning #coding #prompt #generative #ai #azure #app
New 𝐓𝐈 𝐌𝐢𝐧𝐝𝐦𝐚𝐩 demo in action. 📽
New features coming soon, stay tuned. 🆕
𝐒𝐭𝐫𝐞𝐚𝐦𝐥𝐢𝐭 𝐀𝐩𝐩: https://ti-mindmap-gpt.streamlit.app/ 💿
𝐆𝐢𝐭𝐇𝐮𝐛: https://github.com/format81/TI-Mindmap-GPT ✨
𝐖𝐫𝐢𝐭𝐞-𝐮𝐩 used in the demo: https://www.microsoft.com/en-us/security/blog/2024/05/01/dirty-stream-attack-discovering-and-mitigating-a-common-vulnerability-pattern-in-android-apps/
𝘚𝘱𝘰𝘪𝘭𝘦𝘳: 𝘪𝘧 𝘺𝘰𝘶 𝘸𝘢𝘵𝘤𝘩𝘦𝘥 𝘵𝘩𝘦 𝘷𝘪𝘥𝘦𝘰 𝘤𝘢𝘳𝘦𝘧𝘶𝘭𝘭𝘺, 𝘺𝘰𝘶 𝘸𝘰𝘶𝘭𝘥 𝘩𝘢𝘷𝘦 𝘯𝘰𝘵𝘪𝘤𝘦𝘥 𝘵𝘩𝘦 𝘴𝘶𝘱𝘱𝘰𝘳𝘵 𝘧𝘰𝘳 𝘔𝘪𝘴𝘵𝘳𝘢𝘭𝘈𝘐. 😊
#timindmap #mindmap #streamlit #threatintelligence #cyberthreatintelligence #openai #azure #azureopenai #mistral #mistralai #python #llm #ai #genai #embeddings #completition
🔈Second monthly release of 𝐖𝐡𝐚𝐭'𝐬 𝐧𝐞𝐰 𝐢𝐧 𝐓𝐈 𝐌𝐢𝐧𝐝𝐦𝐚𝐩 | 𝐦𝐚𝐫 2024. 🔈
Article and tool co-authored with Oleksiy Meletskiy.
📢 New Features:
➡Session management
➡Scraping enhancements
➡Code optimization
➡PDF Report enhancements
➡Mitre ATT&CK Navigator layer
📰𝐁𝐥𝐨𝐠: https://lnkd.in/diuJTfrH
💻 𝐀𝐩𝐩: https://lnkd.in/dSVdG2B4
⏩ 𝐆𝐢𝐭𝐇𝐮𝐛: https://lnkd.in/dJDSQx8Y
𝐇𝐨𝐰 𝐭𝐨 𝐠𝐞𝐭 𝐢𝐧𝐯𝐨𝐥𝐯𝐞𝐝
The project is open to external contributions.
To collaborate, please check the GitHub repository: https://lnkd.in/dJDSQx8Y
If you find TI Mindmap useful, please consider starring ⭐ the repository on GitHub.
#timindmap #ti #mindmap #threatintelligence #llm #llmapp #openai #azureopenai #largelanguagemodel #cybersecurity #cyber #security #python #streamlit #infer #embedding #chat #ioc #mitre #ttp #cyberreport #report #mermaid #genai #generativeai #cyberthreatintelligence
#github #prompt #promptengineering #FewShotPrompting #gpt #gpt4
#api #DataVisualization #threat #infosec #threatreport #oai #analyst #soc
Excited to share a series of periodic articles on the developments of TI Mindmap: 𝐖𝐡𝐚𝐭’𝐬 𝐧𝐞𝐰 𝐢𝐧 𝐓𝐈 𝐌𝐢𝐧𝐝𝐦𝐚𝐩, first issue.
Article and tool co-authored with Oleksiy Meletskiy.
New Features:
➡Extract adversary tactics, techniques, and procedures
➡Tactics, techniques and procedures by execution time
➡Tactics, techniques and procedures timeline
➡AI Chat on your article
➡Mermaid live editor integration
➡PDF report
➡Tweet Mindmap
𝐇𝐨𝐰 𝐭𝐨 𝐠𝐞𝐭 𝐢𝐧𝐯𝐨𝐥𝐯𝐞𝐝
The project is open to external contributions.
To collaborate, please check the GitHub repository: https://github.com/format81/TI-Mindmap-GPT/
If you find TI Mindmap useful, please consider starring the repository on GitHub.
To learn more:
https://medium.com/@antonio.formato/whats-new-in-ti-mindmap-feb-2024-14cf3b383833
#timindmap #ti #mindmap #threatintelligence #llm #llmapp #openai #azureopenai #largelanguagemodel #cybersecurity #cyber #security #python #streamlit #infer #embedding #chat #ioc #mitre #ttp #cyberreport #report #mermaid #genai #generativeai #cyberthreatintelligence
#github #prompt #promptengineering #FewShotPrompting #gpt #gpt4
#api #DataVisualization #threat #infosec #threatreport #oai #analyst #soc #cert
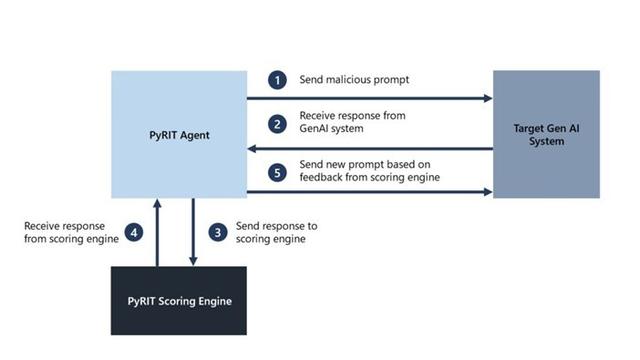
𝐀𝐧𝐧𝐨𝐮𝐧𝐜𝐢𝐧𝐠 𝐌𝐢𝐜𝐫𝐨𝐬𝐨𝐟𝐭’𝐬 𝐨𝐩𝐞𝐧 𝐚𝐮𝐭𝐨𝐦𝐚𝐭𝐢𝐨𝐧 𝐟𝐫𝐚𝐦𝐞𝐰𝐨𝐫𝐤 𝐭𝐨 𝐫𝐞𝐝 𝐭𝐞𝐚𝐦 𝐠𝐞𝐧𝐞𝐫𝐚𝐭𝐢𝐯𝐞 𝐀𝐈 𝐒𝐲𝐬𝐭𝐞𝐦𝐬
𝐏𝐲𝐑𝐈𝐓 automates AI Red Teaming tasks to allow operators to focus on more complicated and time-consuming tasks and can also identify security harms such as misuse (e.g., malware generation, jailbreaking), and privacy harms (e.g., identity theft).
Find out more:
GitHub repo: https://github.com/Azure/PyRIT
How to Guide: https://github.com/Azure/PyRIT/blob/main/doc/how_to_guide.ipynb
#redteam #airedteam #redteaming #PyRIT #ml #ai #framewrok #python #cyber #llm #ai #aisecurity #microsoft #microsoftsecurity #opensource #MicrosoftAIRedTeam #GenAI #jailbreaking #promtp #promptinjection #malware #privacy #responsibleai #cybersecurity #aisecurity #secureai #machinelearning #generativeai
No cybersecurity and genAI in this post, just a bit of coding. 😉
𝐌𝐞𝐫𝐦𝐚𝐢𝐝.𝐥𝐢𝐯𝐞 𝐂𝐨𝐝𝐞 𝐑𝐞𝐧𝐝𝐞𝐫𝐞𝐫: https://encode-mermaid-diagram.streamlit.app/
🚀 I've just developed a Streamlit app that takes input in Mermaid.js code and outputs a rendered link for mermaid.live.
This functionality enables users to seamlessly edit their code, addressing any errors or dynamically modifying the diagram as needed. I believe this tool could be useful for those working with Mermaid charts.
Feel free to check it out and see how it can streamline your workflow!
Read more:
https://medium.com/@antonio.formato/mermaid-live-code-renderer-with-python-2e8cb677e963
Spoiler: soon this will be an integrated feature in 𝐓𝐈 𝐌𝐢𝐧𝐝𝐦𝐚𝐩: https://ti-mindmap-gpt.streamlit.app/ 📊✨
#Streamlit #MermaidJS #DataVisualization #pyhton #mermaid #timindmap #coding
I share this report generated with 𝐓𝐈 𝐌𝐢𝐧𝐝𝐦𝐚𝐩.
Tool: https://ti-mindmap-gpt.streamlit.app/
I invite you to contribute and add a star on GitHub: https://github.com/format81/TI-Mindmap-GPT
Title: 𝐍𝐞𝐛𝐮𝐥𝐚 𝐁𝐫𝐨𝐤𝐞𝐫: 𝐈𝐭𝐚𝐥𝐢𝐚𝐧-𝐛𝐚𝐬𝐞𝐝 𝐓𝐡𝐫𝐞𝐚𝐭 𝐎𝐩𝐞𝐫𝐚𝐭𝐢𝐨𝐧
Summary: 𝘛𝘩𝘦 𝘳𝘦𝘱𝘰𝘳𝘵 𝘱𝘳𝘦𝘴𝘦𝘯𝘵𝘴 𝘢𝘯 𝘢𝘯𝘢𝘭𝘺𝘴𝘪𝘴 𝘰𝘧 𝘰𝘧𝘧𝘦𝘯𝘴𝘪𝘷𝘦 𝘰𝘱𝘦𝘳𝘢𝘵𝘪𝘰𝘯𝘴 𝘤𝘰𝘯𝘥𝘶𝘤𝘵𝘦𝘥 𝘣𝘺 𝘢𝘯 𝘐𝘵𝘢𝘭𝘪𝘢𝘯 𝘵𝘩𝘳𝘦𝘢𝘵 𝘢𝘤𝘵𝘰𝘳 𝘬𝘯𝘰𝘸𝘯 𝘢𝘴 𝘕𝘦𝘣𝘶𝘭𝘢 𝘉𝘳𝘰𝘬𝘦𝘳. 𝘚𝘪𝘯𝘤𝘦 𝘦𝘢𝘳𝘭𝘺 2020, 𝘕𝘦𝘣𝘶𝘭𝘢 𝘉𝘳𝘰𝘬𝘦𝘳 𝘩𝘢𝘴 𝘦𝘮𝘱𝘭𝘰𝘺𝘦𝘥 𝘤𝘶𝘴𝘵𝘰𝘮-𝘮𝘢𝘥𝘦 𝘮𝘢𝘭𝘸𝘢𝘳𝘦 𝘵𝘰 𝘤𝘰𝘮𝘱𝘳𝘰𝘮𝘪𝘴𝘦 𝘴𝘺𝘴𝘵𝘦𝘮𝘴 𝘮𝘢𝘪𝘯𝘭𝘺 𝘪𝘯 𝘵𝘩𝘦 𝘵𝘳𝘢𝘯𝘴𝘱𝘰𝘳𝘵 𝘢𝘯𝘥 𝘢𝘦𝘳𝘰𝘯𝘢𝘶𝘵𝘪𝘤𝘴 𝘪𝘯𝘥𝘶𝘴𝘵𝘳𝘪𝘦𝘴. 𝘛𝘩𝘦 𝘷𝘪𝘳𝘶𝘴'𝘴 𝘱𝘦𝘳𝘷𝘢𝘴𝘪𝘷𝘦 𝘱𝘳𝘦𝘴𝘦𝘯𝘤𝘦 𝘢𝘤𝘳𝘰𝘴𝘴 𝘷𝘢𝘳𝘪𝘰𝘶𝘴 𝘴𝘦𝘤𝘵𝘰𝘳𝘴 𝘪𝘮𝘱𝘭𝘪𝘦𝘴 𝘵𝘩𝘢𝘵 𝘵𝘩𝘦 𝘵𝘩𝘳𝘦𝘢𝘵 𝘢𝘤𝘵𝘰𝘳 𝘪𝘴 𝘱𝘶𝘳𝘴𝘶𝘪𝘯𝘨 𝘢 𝘯𝘰𝘯-𝘵𝘢𝘳𝘨𝘦𝘵𝘦𝘥 𝘰𝘧𝘧𝘦𝘯𝘴𝘪𝘷𝘦 𝘴𝘵𝘳𝘢𝘵𝘦𝘨𝘺, 𝘢𝘯 𝘢𝘴𝘴𝘶𝘮𝘱𝘵𝘪𝘰𝘯 𝘴𝘵𝘳𝘦𝘯𝘨𝘵𝘩𝘦𝘯𝘦𝘥 𝘣𝘺 𝘵𝘩𝘦 𝘮𝘢𝘭𝘸𝘢𝘳𝘦'𝘴 𝘜𝘚𝘉 𝘱𝘳𝘰𝘱𝘢𝘨𝘢𝘵𝘪𝘰𝘯 𝘤𝘢𝘱𝘢𝘣𝘪𝘭𝘪𝘵𝘪𝘦𝘴.
𝘕𝘦𝘣𝘶𝘭𝘢 𝘉𝘳𝘰𝘬𝘦𝘳 𝘴𝘩𝘰𝘸𝘤𝘢𝘴𝘦𝘴 𝘥𝘪𝘴𝘵𝘪𝘯𝘤𝘵 𝘛𝘛𝘗𝘴 𝘵𝘩𝘢𝘵 𝘦𝘷𝘰𝘭𝘷𝘦 𝘰𝘷𝘦𝘳 𝘵𝘪𝘮𝘦. 𝘍𝘳𝘰𝘮 𝘣𝘶𝘤𝘰𝘭𝘪𝘤 𝘰𝘣𝘧𝘶𝘴𝘤𝘢𝘵𝘪𝘰𝘯 𝘢𝘯𝘥 𝘦𝘯𝘤𝘰𝘥𝘪𝘯𝘨 𝘵𝘦𝘤𝘩𝘯𝘪𝘲𝘶𝘦𝘴 𝘵𝘩𝘢𝘵 𝘦𝘮𝘱𝘭𝘰𝘺 𝘪𝘯𝘵𝘦𝘳𝘮𝘦𝘥𝘪𝘢𝘵𝘦 𝘎𝘪𝘵𝘏𝘶𝘣-𝘩𝘰𝘴𝘵𝘦𝘥 𝘧𝘪𝘭𝘦𝘴 𝘧𝘪𝘭𝘭𝘦𝘥 𝘸𝘪𝘵𝘩 𝘣𝘭𝘢𝘯𝘬 𝘴𝘱𝘢𝘤𝘦𝘴 𝘵𝘰 𝘵𝘩𝘦 𝘶𝘴𝘦 𝘰𝘧 𝘱𝘭𝘢𝘵𝘧𝘰𝘳𝘮𝘴 𝘭𝘪𝘬𝘦 𝘝𝘪𝘮𝘦𝘰 𝘢𝘯𝘥 𝘈𝘳𝘴𝘛𝘦𝘤𝘩𝘯𝘪𝘤𝘢 𝘧𝘰𝘳 𝘤𝘰𝘥𝘦 𝘩𝘰𝘴𝘵𝘪𝘯𝘨.
𝘈 𝘥𝘦𝘵𝘢𝘪𝘭𝘦𝘥 𝘪𝘯𝘴𝘱𝘦𝘤𝘵𝘪𝘰𝘯 𝘰𝘧 𝘵𝘩𝘦 𝘮𝘢𝘭𝘸𝘢𝘳𝘦'𝘴 𝘰𝘱𝘦𝘳𝘢𝘵𝘪𝘰𝘯 𝘳𝘦𝘷𝘦𝘢𝘭𝘴 𝘤𝘰𝘯𝘴𝘵𝘢𝘯𝘵 𝘥𝘰𝘸𝘯𝘭𝘰𝘢𝘥𝘴 𝘰𝘧 𝘢𝘥𝘥𝘪𝘵𝘪𝘰𝘯𝘢𝘭 𝘱𝘢𝘺𝘭𝘰𝘢𝘥𝘴 𝘶𝘱𝘰𝘯 𝘭𝘢𝘶𝘯𝘤𝘩𝘪𝘯𝘨 𝘙𝘶𝘯𝘵𝘪𝘮𝘦𝘉𝘳𝘰𝘬𝘦𝘳.𝘦𝘹𝘦. 𝘋𝘰𝘮𝘢𝘪𝘯𝘴 𝘢𝘳𝘦 𝘢𝘭𝘴𝘰 𝘳𝘦𝘨𝘶𝘭𝘢𝘳𝘭𝘺 𝘴𝘸𝘪𝘵𝘤𝘩𝘦𝘥 𝘵𝘰 𝘢𝘷𝘰𝘪𝘥 𝘱𝘳𝘦𝘥𝘪𝘤𝘵𝘪𝘷𝘦 𝘢𝘯𝘢𝘭𝘺𝘴𝘪𝘴 𝘧𝘳𝘰𝘮 𝘵𝘩𝘦 𝘤𝘺𝘣𝘦𝘳𝘴𝘦𝘤𝘶𝘳𝘪𝘵𝘺 𝘵𝘦𝘢𝘮. 𝘛𝘩𝘦 𝘳𝘦𝘱𝘰𝘳𝘵 𝘤𝘰𝘯𝘧𝘪𝘥𝘦𝘯𝘵𝘭𝘺 𝘢𝘵𝘵𝘳𝘪𝘣𝘶𝘵𝘦𝘴 𝘵𝘩𝘦 𝘢𝘵𝘵𝘢𝘤𝘬𝘴 𝘵𝘰 𝘕𝘦𝘣𝘶𝘭𝘢 𝘉𝘳𝘰𝘬𝘦𝘳 𝘸𝘪𝘵𝘩 𝘴𝘰𝘭𝘪𝘥 𝘦𝘷𝘪𝘥𝘦𝘯𝘤𝘦, 𝘪𝘯𝘤𝘭𝘶𝘥𝘪𝘯𝘨 𝘶𝘯𝘪𝘲𝘶𝘦 𝘮𝘢𝘭𝘸𝘢𝘳𝘦 𝘯𝘢𝘮𝘪𝘯𝘨 𝘤𝘰𝘯𝘷𝘦𝘯𝘵𝘪𝘰𝘯𝘴 𝘢𝘯𝘥 𝘐𝘵𝘢𝘭𝘪𝘢𝘯 𝘮𝘢𝘯𝘪𝘧𝘦𝘴𝘵𝘴 𝘪𝘯 𝘵𝘩𝘦 𝘨𝘦𝘯𝘦𝘳𝘢𝘵𝘦𝘥 𝘙𝘶𝘯𝘵𝘪𝘮𝘦𝘉𝘳𝘰𝘬𝘦𝘳.𝘦𝘹𝘦 𝘧𝘪𝘭𝘦𝘴.
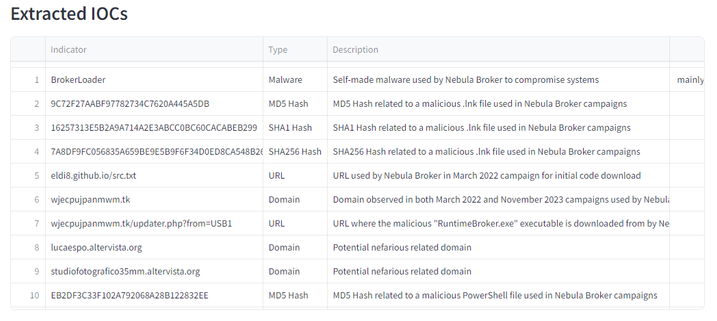
𝘍𝘰𝘳 𝘥𝘦𝘵𝘦𝘤𝘵𝘪𝘰𝘯 𝘰𝘱𝘱𝘰𝘳𝘵𝘶𝘯𝘪𝘵𝘪𝘦𝘴, 𝘬𝘦𝘺 𝘐𝘖𝘊𝘴 𝘪𝘯𝘤𝘭𝘶𝘥𝘦 𝘶𝘯𝘪𝘲𝘶𝘦 𝘯𝘢𝘮𝘪𝘯𝘨 𝘱𝘢𝘵𝘵𝘦𝘳𝘯𝘴 𝘪𝘯 𝘴𝘰𝘮𝘦 𝘴𝘢𝘮𝘱𝘭𝘦𝘴, 𝘥𝘪𝘴𝘵𝘪𝘯𝘤𝘵 𝘊2𝘴 𝘶𝘵𝘪𝘭𝘪𝘻𝘦𝘥, 𝘦𝘯𝘤𝘰𝘥𝘦𝘥 𝘧𝘪𝘭𝘦𝘴 𝘦𝘹𝘱𝘭𝘰𝘪𝘵𝘦𝘥 𝘧𝘰𝘳 𝘮𝘢𝘭𝘸𝘢𝘳𝘦 𝘱𝘳𝘰𝘱𝘢𝘨𝘢𝘵𝘪𝘰𝘯, 𝘢𝘯𝘥 𝘵𝘩𝘦 𝘱𝘳𝘦𝘴𝘦𝘯𝘤𝘦 𝘰𝘧 𝘴𝘱𝘦𝘤𝘪𝘧𝘪𝘤 𝘧𝘪𝘭𝘦𝘴 𝘴𝘶𝘤𝘩 𝘢𝘴 “𝘙𝘶𝘯𝘵𝘪𝘮𝘦𝘉𝘳𝘰𝘬𝘦𝘳.𝘦𝘹𝘦”.
Original blog by Fortgale: https://fortgale.com/blog/featured/nebula-broker-offensive-operations-italy/
#timindmap #threatintelligence #ai #genai #openai #azureopenai #azure #ioc #ttp #timeline #soc #llm
𝐂𝐨𝐩𝐢𝐥𝐨𝐭 𝐟𝐨𝐫 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲: 𝐞𝐥𝐞𝐦𝐞𝐧𝐭𝐬 𝐨𝐟 𝐚𝐧 𝐞𝐟𝐟𝐞𝐜𝐭𝐢𝐯𝐞 𝐩𝐫𝐨𝐦𝐩𝐭
From the "Get started with Microsoft Copilot for Security" online training, I highlight this interesting in-depth analysis.
𝐄𝐟𝐟𝐞𝐜𝐭𝐢𝐯𝐞 𝐩𝐫𝐨𝐦𝐩𝐭𝐬 give Copilot adequate and useful parameters to generate a valuable response. Security analysts or researchers should include the following elements when writing a prompt.
💡 𝐆𝐨𝐚𝐥 - specific, security-related information that you need
💡𝐂𝐨𝐧𝐭𝐞𝐱𝐭 - why you need this information or how you'll use it
💡𝐄𝐱𝐩𝐞𝐜𝐭𝐚𝐭𝐢𝐨𝐧𝐬 - format or target audience you want the response tailored to
💡𝐒𝐨𝐮𝐫𝐜𝐞 - known information, data sources, or plugins Copilot should use
At this link other prompting tips:
Full training: https://learn.microsoft.com/en-us/training/paths/security-copilot-and-ai/
#copilot #copilotforsecurity #securitycopilot #microsoft #microosoftsecurity #llm #openai #azureopenai #llmapps #soc #generativeai #genai #cybersecurity #azure #cloudsecurity #cloudnative #defender #sentinel #microsoftsentinel #xdr #defenderxdr #prompt #promptengineering
𝐏𝐫𝐨𝐭𝐞𝐜𝐭 𝐮𝐧𝐦𝐚𝐧𝐚𝐠𝐞𝐝 𝐨𝐫 3𝐫𝐝 𝐩𝐚𝐫𝐭𝐲 𝐌𝐃𝐌 𝐦𝐚𝐧𝐚𝐠𝐞𝐝 𝐢𝐎𝐒/𝐀𝐧𝐝𝐫𝐨𝐢𝐝 𝐝𝐞𝐯𝐢𝐜𝐞𝐬 𝐰𝐢𝐭𝐡 𝐌𝐃𝐄
In this blog post, you will learn how to protect unmanaged (personal) or 3rd party MDM managed iOS and Android devices with Microsoft Defender for Endpoint as your Mobile Threat Defense (MTD) solution.
The solution leverages Intune’s App Protection Policies aka MAM to enforce Device Protection with MDE regardless of the device enrollment state.
#mde #defender #defenderforendpoint #mtd #mobile #mobileprotection #mobilerhreatdefence #edr #xdr #microsoft #microsoftsecurity #soc #intune #mdm #mam #byod #ios #android #cloudnative
🚀 Excited to share our latest #CyberSignals report for February 2024! 🛡️
This edition explores the profound effects of AI on cybersecurity, highlighting its dual role as both a powerful defender in enhancing security protocols and a potential vector for cyber threats.
Key insights include:
▶ AI's pivotal function in addressing the global shortage of cybersecurity talent.
▶The significant improvement in accuracy and efficiency of security operations through tools like Copilot for Security.
▶Our strategies for counteracting AI-powered threats to promote a secure online environment.
https://news.microsoft.com/wp-content/uploads/prod/sites/626/2024/02/CyberSignals-Feb-2024.pdf
#Cybersecurity #AI #Microsoft #OpenAI #DigitalDefense #Innovation #genai #cybersecurity #aisecurity #cloud #cloudsecurity #llm #copilot #threat #microsoftsecurity
𝐀𝐧𝐧𝐨𝐮𝐧𝐜𝐢𝐧𝐠 𝐧𝐞𝐰 𝐟𝐞𝐚𝐭𝐮𝐫𝐞𝐬 𝐚𝐧𝐝 𝐢𝐦𝐩𝐫𝐨𝐯𝐞𝐦𝐞𝐧𝐭𝐬 𝐢𝐧 𝐀𝐳𝐮𝐫𝐞 𝐅𝐢𝐫𝐞𝐰𝐚𝐥𝐥
➡Flow Trace logs are now generally available.
➡Autoscaling based on the number of connections is now generally available.
➡Parallel IP Group update support is now in public preview.
#azure #firewall #azurefirewall #cloudfirewall #cloudsecurity #network #networksecurity #monitoring #soc #monitoring #azurenetworksecurity #cloudnative
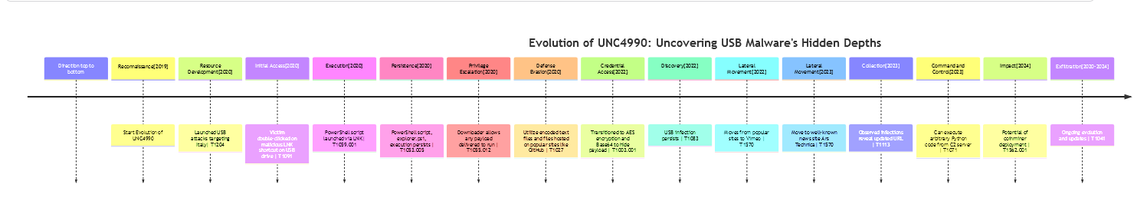
Let's test 𝐓𝐈 𝐌𝐢𝐧𝐝𝐦𝐚𝐩 with this interesting article: https://www.mandiant.com/resources/blog/unc4990-evolution-usb-malware
𝐀𝐳𝐮𝐫𝐞 𝐎𝐩𝐞𝐧𝐀𝐈 𝐆𝐞𝐧𝐞𝐫𝐚𝐭𝐞𝐝 𝐒𝐮𝐦𝐦𝐚𝐫𝐲
𝘛𝘩𝘦 𝘳𝘦𝘱𝘰𝘳𝘵 𝘥𝘰𝘤𝘶𝘮𝘦𝘯𝘵𝘴 𝘵𝘩𝘦 𝘰𝘯𝘨𝘰𝘪𝘯𝘨 𝘢𝘤𝘵𝘪𝘷𝘪𝘵𝘪𝘦𝘴 𝘰𝘧 𝘵𝘩𝘦 𝘵𝘩𝘳𝘦𝘢𝘵 𝘢𝘤𝘵𝘰𝘳 𝘨𝘳𝘰𝘶𝘱 𝘜𝘕𝘊4990, 𝘸𝘩𝘪𝘤𝘩 𝘱𝘳𝘪𝘮𝘢𝘳𝘪𝘭𝘺 𝘵𝘢𝘳𝘨𝘦𝘵𝘴 𝘶𝘴𝘦𝘳𝘴 𝘣𝘢𝘴𝘦𝘥 𝘪𝘯 𝘐𝘵𝘢𝘭𝘺. 𝘜𝘕𝘊4990, 𝘭𝘪𝘬𝘦𝘭𝘺 𝘮𝘰𝘵𝘪𝘷𝘢𝘵𝘦𝘥 𝘣𝘺 𝘧𝘪𝘯𝘢𝘯𝘤𝘪𝘢𝘭 𝘨𝘢𝘪𝘯, 𝘩𝘢𝘴 𝘣𝘦𝘦𝘯 𝘢𝘤𝘵𝘪𝘷𝘦 𝘴𝘪𝘯𝘤𝘦 2020. 𝘛𝘩𝘦 𝘨𝘳𝘰𝘶𝘱 𝘦𝘮𝘱𝘭𝘰𝘺𝘴 𝘜𝘚𝘉 𝘥𝘦𝘷𝘪𝘤𝘦𝘴 𝘧𝘰𝘳 𝘪𝘯𝘪𝘵𝘪𝘢𝘭 𝘪𝘯𝘧𝘦𝘤𝘵𝘪𝘰𝘯 𝘢𝘯𝘥 𝘦𝘷𝘰𝘭𝘷𝘦𝘴 𝘵𝘩𝘦𝘪𝘳 𝘵𝘰𝘰𝘭𝘴, 𝘵𝘢𝘤𝘵𝘪𝘤𝘴, 𝘢𝘯𝘥 𝘱𝘳𝘰𝘤𝘦𝘥𝘶𝘳𝘦𝘴 (𝘛𝘛𝘗𝘴) 𝘰𝘷𝘦𝘳 𝘵𝘪𝘮𝘦. 𝘛𝘩𝘦 𝘢𝘤𝘵𝘰𝘳 𝘩𝘢𝘴 𝘱𝘳𝘰𝘨𝘳𝘦𝘴𝘴𝘦𝘥 𝘧𝘳𝘰𝘮 𝘶𝘴𝘪𝘯𝘨 𝘣𝘦𝘯𝘪𝘨𝘯 𝘦𝘯𝘤𝘰𝘥𝘦𝘥 𝘵𝘦𝘹𝘵 𝘧𝘪𝘭𝘦𝘴 𝘵𝘰 𝘩𝘰𝘴𝘵𝘪𝘯𝘨 𝘱𝘢𝘺𝘭𝘰𝘢𝘥𝘴 𝘰𝘯 𝘱𝘰𝘱𝘶𝘭𝘢𝘳 𝘴𝘪𝘵𝘦𝘴 𝘭𝘪𝘬𝘦 𝘈𝘳𝘴 𝘛𝘦𝘤𝘩𝘯𝘪𝘤𝘢, 𝘎𝘪𝘵𝘏𝘶𝘣, 𝘎𝘪𝘵𝘓𝘢𝘣, 𝘢𝘯𝘥 𝘝𝘪𝘮𝘦𝘰. 𝘏𝘰𝘸𝘦𝘷𝘦𝘳, 𝘯𝘰 𝘷𝘶𝘭𝘯𝘦𝘳𝘢𝘣𝘪𝘭𝘪𝘵𝘪𝘦𝘴 𝘸𝘦𝘳𝘦 𝘦𝘹𝘱𝘭𝘰𝘪𝘵𝘦𝘥 𝘸𝘪𝘵𝘩𝘪𝘯 𝘵𝘩𝘦𝘴𝘦 𝘴𝘪𝘵𝘦𝘴, 𝘯𝘰𝘳 𝘸𝘦𝘳𝘦 𝘵𝘩𝘦𝘺 𝘮𝘪𝘴𝘤𝘰𝘯𝘧𝘪𝘨𝘶𝘳𝘦𝘥 𝘵𝘰 𝘦𝘯𝘢𝘣𝘭𝘦 𝘵𝘩𝘪𝘴 𝘢𝘣𝘶𝘴𝘦.
𝘐𝘯 𝘪𝘵𝘴 𝘤𝘢𝘮𝘱𝘢𝘪𝘨𝘯, 𝘜𝘕𝘊4990 𝘶𝘵𝘪𝘭𝘪𝘻𝘦𝘴 𝘵𝘸𝘰 𝘬𝘦𝘺 𝘮𝘢𝘭𝘸𝘢𝘳𝘦 𝘵𝘰𝘰𝘭𝘴, 𝘌𝘔𝘗𝘛𝘠𝘚𝘗𝘈𝘊𝘌 𝘢𝘯𝘥 𝘘𝘜𝘐𝘌𝘛𝘉𝘖𝘈𝘙𝘋. 𝘌𝘔𝘗𝘛𝘠𝘚𝘗𝘈𝘊𝘌, 𝘢𝘭𝘴𝘰 𝘬𝘯𝘰𝘸𝘯 𝘢𝘴 𝘝𝘌𝘛𝘛𝘈 𝘓𝘰𝘢𝘥𝘦𝘳 𝘢𝘯𝘥 𝘉𝘳𝘰𝘬𝘦𝘳𝘓𝘰𝘢𝘥𝘦𝘳, 𝘪𝘴 𝘢 𝘥𝘰𝘸𝘯𝘭𝘰𝘢𝘥𝘦𝘳 𝘵𝘩𝘢𝘵 𝘥𝘦𝘭𝘪𝘷𝘦𝘳𝘴 𝘢𝘯𝘺 𝘱𝘢𝘺𝘭𝘰𝘢𝘥 𝘴𝘦𝘳𝘷𝘦𝘥 𝘣𝘺 𝘪𝘵𝘴 𝘤𝘰𝘮𝘮𝘢𝘯𝘥 𝘢𝘯𝘥 𝘤𝘰𝘯𝘵𝘳𝘰𝘭 𝘴𝘦𝘳𝘷𝘦𝘳. 𝘖𝘯 𝘵𝘩𝘦 𝘰𝘵𝘩𝘦𝘳 𝘩𝘢𝘯𝘥, 𝘘𝘜𝘐𝘌𝘛𝘉𝘖𝘈𝘙𝘋 𝘪𝘴 𝘢 𝘮𝘶𝘭𝘵𝘪-𝘤𝘰𝘮𝘱𝘰𝘯𝘦𝘯𝘵 𝘣𝘢𝘤𝘬𝘥𝘰𝘰𝘳 𝘤𝘢𝘱𝘢𝘣𝘭𝘦 𝘰𝘧 𝘴𝘦𝘷𝘦𝘳𝘢𝘭 𝘧𝘶𝘯𝘤𝘵𝘪𝘰𝘯𝘴, 𝘴𝘶𝘤𝘩 𝘢𝘴 𝘢𝘳𝘣𝘪𝘵𝘳𝘢𝘳𝘺 𝘤𝘰𝘮𝘮𝘢𝘯𝘥 𝘦𝘹𝘦𝘤𝘶𝘵𝘪𝘰𝘯, 𝘤𝘭𝘪𝘱𝘣𝘰𝘢𝘳𝘥 𝘤𝘰𝘯𝘵𝘦𝘯𝘵 𝘮𝘢𝘯𝘪𝘱𝘶𝘭𝘢𝘵𝘪𝘰𝘯, 𝘜𝘚𝘉/𝘳𝘦𝘮𝘰𝘷𝘢𝘣𝘭𝘦 𝘥𝘳𝘪𝘷𝘦 𝘪𝘯𝘧𝘦𝘤𝘵𝘪𝘰𝘯, 𝘴𝘺𝘴𝘵𝘦𝘮 𝘪𝘯𝘧𝘰𝘳𝘮𝘢𝘵𝘪𝘰𝘯 𝘨𝘢𝘵𝘩𝘦𝘳𝘪𝘯𝘨, 𝘢𝘯𝘥 𝘊2 𝘤𝘰𝘮𝘮𝘶𝘯𝘪𝘤𝘢𝘵𝘪𝘰𝘯.
𝘛𝘩𝘦 𝘪𝘯𝘧𝘦𝘤𝘵𝘪𝘰𝘯 𝘭𝘪𝘧𝘦𝘤𝘺𝘤𝘭𝘦 𝘴𝘵𝘢𝘳𝘵𝘴 𝘸𝘪𝘵𝘩 𝘵𝘩𝘦 𝘥𝘰𝘶𝘣𝘭𝘦-𝘤𝘭𝘪𝘤𝘬𝘪𝘯𝘨 𝘰𝘧 𝘢 𝘮𝘢𝘭𝘪𝘤𝘪𝘰𝘶𝘴 𝘓𝘕𝘒 𝘴𝘩𝘰𝘳𝘵𝘤𝘶𝘵 𝘧𝘪𝘭𝘦 𝘰𝘯 𝘢 𝘳𝘦𝘮𝘰𝘷𝘢𝘣𝘭𝘦 𝘜𝘚𝘉 𝘥𝘳𝘪𝘷𝘦, 𝘸𝘩𝘪𝘤𝘩 𝘱𝘳𝘰𝘮𝘱𝘵𝘴 𝘵𝘩𝘦 𝘦𝘹𝘦𝘤𝘶𝘵𝘪𝘰𝘯 𝘰𝘧 𝘢 𝘗𝘰𝘸𝘦𝘳𝘚𝘩𝘦𝘭𝘭 𝘴𝘤𝘳𝘪𝘱𝘵 𝘦𝘹𝘱𝘭𝘰𝘳𝘦𝘳.𝘱𝘴1. 𝘛𝘩𝘪𝘴 𝘴𝘤𝘳𝘪𝘱𝘵 𝘴𝘶𝘣𝘴𝘦𝘲𝘶𝘦𝘯𝘵𝘭𝘺 𝘥𝘰𝘸𝘯𝘭𝘰𝘢𝘥𝘴 𝘢 𝘧𝘰𝘳𝘵𝘯𝘪𝘨𝘩𝘵𝘭𝘺 𝘱𝘢𝘺𝘭𝘰𝘢𝘥, 𝘵𝘺𝘱𝘪𝘤𝘢𝘭𝘭𝘺 𝘵𝘩𝘦 𝘌𝘔𝘗𝘛𝘠𝘚𝘗𝘈𝘊𝘌 𝘥𝘰𝘸𝘯𝘭𝘰𝘢𝘥𝘦𝘳. 𝘜𝘕𝘊4990 𝘢𝘭𝘴𝘰 𝘢𝘥𝘦𝘱𝘵𝘭𝘺 𝘭𝘦𝘷𝘦𝘳𝘢𝘨𝘦𝘴 𝘵𝘩𝘪𝘳𝘥-𝘱𝘢𝘳𝘵𝘺 𝘸𝘦𝘣𝘴𝘪𝘵𝘦𝘴 𝘧𝘰𝘳 𝘱𝘢𝘺𝘭𝘰𝘢𝘥 𝘩𝘰𝘴𝘵𝘪𝘯𝘨.
𝐌𝐢𝐧𝐝𝐌𝐚𝐩, 𝐄𝐱𝐭𝐫𝐚𝐜𝐭𝐞𝐝 𝐈𝐎𝐂𝐬, 𝐓𝐓𝐏𝐬 𝐭𝐚𝐛𝐥𝐞, 𝐚𝐧𝐝 𝐓𝐓𝐏𝐬 𝐓𝐢𝐦𝐞𝐥𝐢𝐧𝐞 𝐢𝐧 𝐭𝐡𝐞 𝐟𝐨𝐥𝐥𝐨𝐰𝐢𝐧𝐠 𝐢𝐦𝐚𝐠𝐞𝐬
If you want to try it too: https://ti-mindmap-gpt.streamlit.app/
#timindmap #threatintelligence #ai #genai #openai #azureopenai #azure #llm
𝐇𝐨𝐰 𝐌𝐃𝐓𝐈 𝐇𝐞𝐥𝐩𝐬 𝐏𝐨𝐰𝐞𝐫 𝐂𝐨𝐩𝐢𝐥𝐨𝐭 𝐟𝐨𝐫 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲
A critical aspect of any security analyst's work is keeping up to date with the latest developments in the threat landscape. Copilot for Security allows users to make simple requests known as prompts to learn about threat actors, tools, indicators of compromise (IoCs), and threat intelligence related to their organization's security incidents and alerts.
Below, are three important scenarios the MDTI plugin on Copilot for Security helps teams with:
✔The Reactive approach
➡ Emphasizes investigations and enhancing threat intelligence enrichment and additional context for the entities involved in the incident.
✔The Proactive approach
➡Emphasizing the ability to detect and address threats targeting organizations like mine. It uses threat intelligence to prioritize incidents, trace possible intrusions, and expedite mitigation of misconfigurations and vulnerable software, while simultaneously assessing the organization's impact and posture against specific threats.
✔Keeping up with the latest threat intelligence Trends
➡Detecting emerging threats by analyzing articles and trends, and subsequently disseminating relevant threat data.
#copilot #copilotforsecurity #securitycopilot #microsoftsecurity #microsoft #azure #cyber #cybersecurity #threatintellitence #ti #mdti #defender #defenderthreatintelligence #soc #investigation #cloudsecurity #ai #genai #generativeai #azureopenai #openai
𝐁𝐞𝐜𝐨𝐦𝐞 𝐚 𝐌𝐢𝐜𝐫𝐨𝐬𝐨𝐟𝐭 𝐃𝐞𝐟𝐞𝐧𝐝𝐞𝐫 𝐕𝐮𝐥𝐧𝐞𝐫𝐚𝐛𝐢𝐥𝐢𝐭𝐲 𝐌𝐚𝐧𝐚𝐠𝐞𝐦𝐞𝐧𝐭 𝐍𝐢𝐧𝐣𝐚
We collected content with multiple modules. We will keep updating this training on a regular basis.
Training content:
➡Module 1- Getting started
➡Module 2 – Portal Orientation
➡Module 3 -Prioritization
➡Module 4- Remediation
➡Module 5 - Posture and Compliance
➡ Module 6 – Data access
#defender #xdr #vulnerability #management #vulnerabilitymanagement #microsoft #microsoftsecurity #soc #cve #azure #soc #mdvm #cyber #cybersecurity #tvm
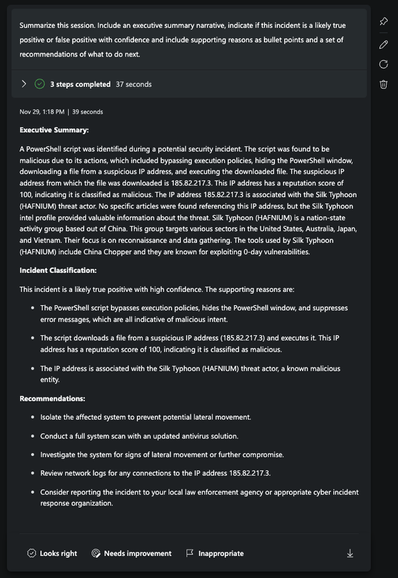
𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐂𝐨𝐩𝐢𝐥𝐨𝐭: 𝐭𝐡𝐞 𝐚𝐫𝐭 𝐨𝐟 𝐩𝐫𝐨𝐦𝐩𝐭𝐢𝐧𝐠 𝐟𝐨𝐫 𝐞𝐟𝐟𝐢𝐜𝐢𝐞𝐧𝐭 𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐢𝐧𝐯𝐞𝐬𝐭𝐢𝐠𝐚𝐭𝐢𝐨𝐧 𝐬𝐮𝐦𝐦𝐚𝐫𝐢𝐞𝐬
Security Copilot employs promptbooks—a series of user-input-driven prompts that analyze cybersecurity threats. Every interaction within Security Copilot, be it an individual prompt or a promptbook, generates a session. These sessions, which are storable and shareable within your workspace.
Generating a summary within Security Copilot can vary in complexity and detail, influenced by how you craft your prompt.
More details:
#ai #genai #security #copilot #securitycopilot #microsoft #microsoftsecurity #azure #xdr #soc #llm #cybersecurity #prompt #prompting #promptengineering #promptbooks #securityincident #hunting #triage