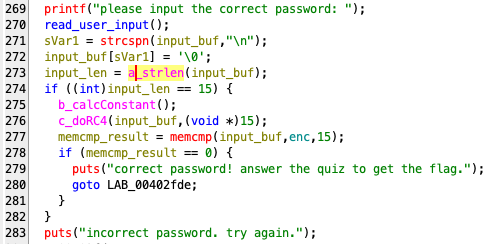
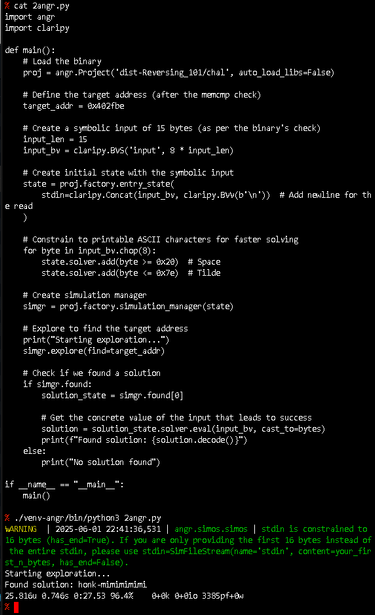
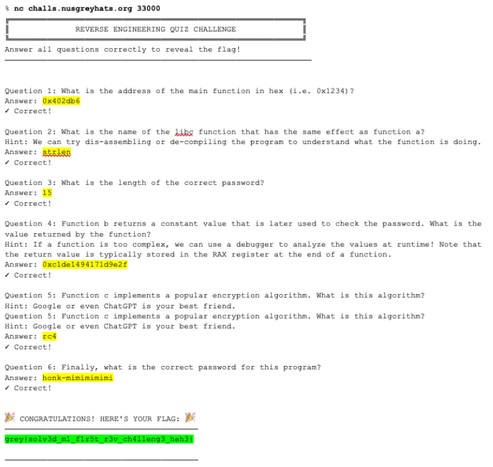
This weekend's GreyCatCTF had an interesting "Reverse 101" challenge in the "EZPZ" category. In "nc" a number of questions were asked on the binary, and the most interesting one was what a certain function did (RC4 encrypt) and what input is required to get the flag.
Besides ghidra & gdb, angr was very helpful here to get the plaintext for the RC4 encryption. See pictures for details.
#greycat #ctf #cybersecurity #angr #reverseengineering #rc4 #decrypt #ezpz #writeup #notawriteup #lazy