World's first #CPU-level #ransomware can "bypass every freaking traditional technology we have out there" — new #firmware-based attacks could usher in new era of unavoidable ransomware
Beek, #Rapid7's senior director of threat analytics, revealed AMD Zen chip bug gave him idea that highly skilled attacker could in theory "allow those intruders to load unapproved #microcode into the processors, breaking encryption at the hardware level and modifying CPU behavior at will."
https://www.tomshardware.com/pc-components/cpus/worlds-first-cpu-level-ransomware-can-bypass-every-freaking-traditional-technology-we-have-out-there-new-firmware-based-attacks-could-usher-in-new-era-of-unavoidable-ransomware
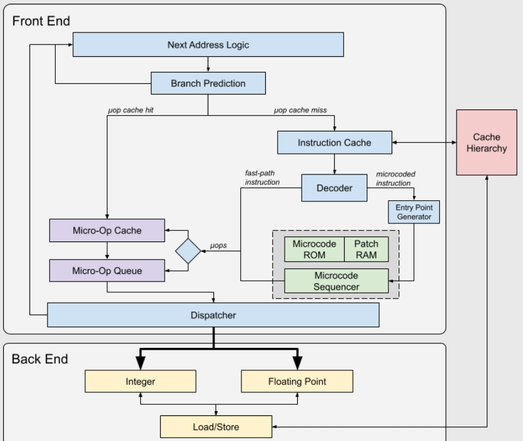
#Microcode
https://www.theregister.com/2025/05/11/cpu_ransomware_rapid7/
Spoiler alert: Beek followed through and wrote proof-of-concept code for #ransomware that hides in the computer's #processor. "Of course, we won't release that, but it's fascinating, right?"
This, according to Beek, is the worst-case scenario. "Ransomware at the #CPU level, #microcode alteration, and if you are in the CPU or the #firmware, you will bypass every freaking traditional [anti-malware] technology we have out there."
Von #AMD-Lücke inspiriert:
#Forscher warnt vor #Ransomware im #CPU-Microcode
Eine Lücke in #AMD-CPUs ermöglicht manipulative Eingriffe in den #Microcode. Darin eingeschleuste #Ransomware wäre äußerst schwer zu bezwingen.
Eine #Ransomware-Infektion kann für Unternehmen weitreichende Folgen haben, die nicht selten auch in einer Insolvenz münden. Durch geeignete Maßnahmen lassen sich die Risiken für solche #Sicherheitsvorfälle eindämmen.
Linux 6.16 will warn users about outdated Intel microcode
Intel is routinely releasing new microcode for their processors to improve the processor’s performance and to fix critical issues, especially when dealing with security vulnerabilities that may be found in old microcode versions. This is to ensure that your system becomes more secure than before by eliminating security vulnerabilities.
A patch has been queued to the Linux kernel tip repository that will make its way to the Linux 6.16 kernel. It warns the user on boot that the microcode version for the processor is old and that it needs to be updated to ensure security. Userspace applications can determine whether your computer is using the old microcode via the /sys/devices/system/cpu/vulnerabilities/old_microcode file.
The kernel, if running in the old microcode, will be tainted with the TAINT_CPU_OUT_OF_SPEC flag, making it more difficult for kernel bugs that have to do with the old microcode to be reported directly to the bug tracker. The implementation relies on a manually-maintained list of processors found in the intel-ucode-defs.h file. It contains a list of structures that contain the following variables:
- flags: List of flags (always
X86_CPU_ID_FLAG_ENTRY_VALID) - vendor: Processor vendor (always
X86_VENDOR_INTEL) - family: Processor family (usually
0x6or0xf) - model: Processor model
- steppings: Processor stepping
- driver_data: Processor microcode ID as an integer
Not only that, but all processors that are running on a debug microcode (that is, microcode ID with the 31st bit set to 1) are considered to be old.
We advise you to update your processor’s microcode to the latest version to ensure that there are no security vulnerabilities present.
#intel #Kernel #Linux #LinuxKernel #Microcode #news #processor #processors #Tech #Technology #update
🤡 Ah yes, because rewriting #microcode to run #RISC-V on #AMD #CPUs is *definitely* something everyone has on their weekend to-do list. 🛠️ What's next, trying to make a toaster run Crysis? 💡
https://rvspoc.org/en/S2502/ #weekendprojects #techhumor #toastergaming #HackerNews #ngated
Run RISC-V Binaries on AMD Zen-Series CPUs via Microcode Modification
#HackerNews #RISC-V #AMD #Microcode #Zen-Series #Binaries #Technology
#NixOS is interesting. Pretty reliable (not as much as #AtomicDesktops in my noob tests) while also performant
Note that such old hardware will have #microcode vulnerabilities and locking it down will further slow it down. At least thinking of #spectre or #meltdown (not sure if hyperthreading was even thought of back then)
Undocumented 8086 instructions, explained by the microcode
https://www.righto.com/2023/07/undocumented-8086-instructions.html
#HackerNews #Undocumented #8086 #instructions #microcode #technology #computing #retro #programming
Notes on the Pentium's Microcode Circuitry
https://www.righto.com/2025/03/pentium-microcde-rom-circuitry.html
#HackerNews #Pentium #Microcode #Microelectronics #ComputerArchitecture #TechHistory
Extensive Analysis of the Raptor Lake CPU Bug
Intel’s Raptor Lake CPUs, which form part of the 13th and 14th generation Intel Core desktop processor line, were celebrated for their hybrid architecture combining high-performance cores with efficiency cores. However, shortly after their release, a critical bug emerged that has led to system instability and, in some cases, permanent degradation of the affected chips.
Read More: https://machaddr.substack.com/p/extensive-analysis-of-the-raptor
AMD CPU microcode 的簽名漏洞 在 Lobsters 上看到 Google 對上個月 AMD CPU 的 microcode 耕更新漏洞的分析:「Zen and the Art of Microcode Hacking」,看完後發現原來是自己設計出來的簽名驗證導致的... CPU 透過修正 microcode 修正問題算是行之有年的方法,可以在開機後讀進來改變本來設計的行為,也因為這個動作很危險,通常會加上數位簽名的方式確保只有原廠可以改。 AMD 在這邊的設計是用了 RSA 2048 bit 簽名保護,但把整把 RSA public key 放進去驗證會吃太多電晶體,所以這邊只存了 128-bit value 以節省電晶體空間,這邊本來以為是用 MD5 被撞,或是用… https://blog.gslin.org/archives/2025/03/06/12295/amd-cpu-microcode-%e7%9a%84%e7%b0%bd%e5%90%8d%e6%bc%8f%e6%b4%9e/ #algorithm #amd #cmac #cpu #hardware #key #microcode #number #random #rsa #security #vulnerability
Zen and the Art of Microcode Hacking:
https://bughunters.google.com/blog/5424842357473280/zen-and-the-art-of-microcode-hacking
#processor #cybersecurity #microcode #microcodehacking #hacking #exploitation
Zen and the Art of Microcode Hacking:
https://bughunters.google.com/blog/5424842357473280/zen-and-the-art-of-microcode-hacking
#processor #cybersecurity #microcode #microcodehacking #hacking #exploitation
🚀🤖 Behold, the 'Zentool' saga: yet another #GitHub repository hiding behind buzzwords like "microcode manipulation" 🙄. Apparently, the secret to CPU security is buried in a README.md file, because who needs actual documentation? 🧐🔐
https://github.com/google/security-research/blob/master/pocs/cpus/entrysign/zentool/README.md #Zentool #microcode #CPUsecurity #techbuzzwords #documentation #HackerNews #ngated
Zentool – AMD Zen Microcode Manipulation Utility — https://github.com/google/security-research/blob/master/pocs/cpus/entrysign/zentool/README.md
#HackerNews #Zentool #AMD #Zen #Microcode #Manipulation #Utility #security #research #GitHub #tech #news
One of the organisations I work for is so poor, we should not exist by any account.
How poor?
Our main server is fifteen years old.
Only reason we got it, it was abandoned in a rack we bought for $50 and I resurrected it.
This transcends boneyard.
This is summoning machine spirits from beyond, Deus Mechanics incantations.
I yelled at the Operations manager today, calling him a Necromancer because he was praising this ancient "Raid" box as "better than what we used to have" when all I want to do is nail it to the wall as a warning to others.
Anyhoo...
This is how I found today that a 15 year old iron running #Debian 10 simply could not run any #docker images of this particular package because the #nodej component just won't run on the #microcode
I don't even realise it was a thing.
But then, how many of you run a box that's 15 years old in production...
...how "slow" is that rack server?
I pulled one of the Intel NUCs out of the boneyard (it's one of those paper book sized box "computers") and put Debian on THAT...
...it runs 33% faster and that thing was binned because it couldn't pull an office admin desktop workload.
33% faster!!!
Security Week 2507: вредоносный микрокод для серверных процессоров AMD
На прошлой неделе компания AMD выпустила патчи для серверных процессоров AMD EPYC, закрывающие уязвимость, которая позволяет загружать вредоносные обновления микрокода. Уязвимость была обнаружена в сентябре прошлого года компанией Google, которая также опубликовала информацию о проблеме. Оба источника предлагают довольно краткое описание уязвимости, но в Google обещают раскрыть больше деталей в марте. Судя по тому, что все же было опубликовано (включая ограниченный по возможностям демонстрационный код ), ошибка присутствует в функции хеширования, которая в свою очередь используется для верификации официальных обновлений микрокода. Proof-of-Concept раскрывает чуть больше информации. Во-первых, там указано, что код успешно работает не только на серверных процессорах AMD EPYC, но и на потребительском процессоре AMD Ryzen 9 7940HS. Во-вторых, в описании к демонстрационному коду показано, как заставить генератор случайных чисел RDRAND всегда возвращать одно и то же число, что, судя по всему, является ступенью на пути к загрузке неавторизованного патча.
https://www.theregister.com/AMP/2025/02/04/google_amd_microcode/
I just bought a new nuc with a ryzen5 cpu. Damn. #AMD #Ryzen #Epyc #microcode