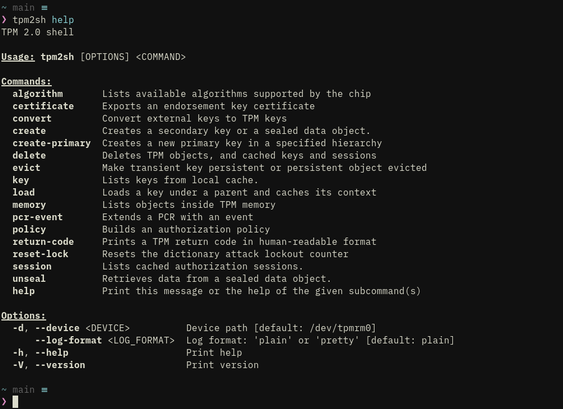
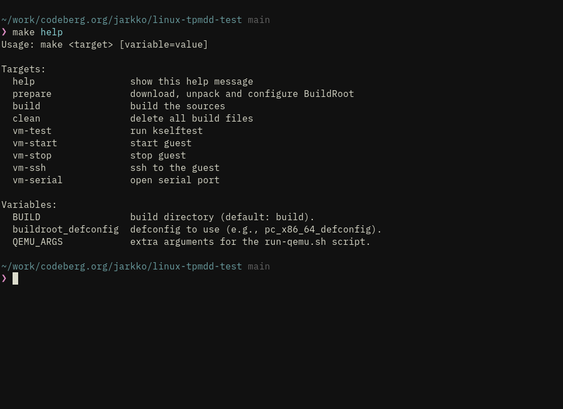
tpm2sh 0.11.16
This is the release where things mostly work and is first usable version for wider audience than just me.
Functionality is focused on key management and it is quite limited on operations.
That said, it the most important functionalities, and most difficult to implement, in place:
- Implicit creation of HMAC sessions to protect communication, and hiding its complexity . It is still a stub as parameter encryption is not in place but the mechanism is working correctly.
- Key management including direct support for PKCS#1, PKCS#8 and SEC1 external keys with custom parsers so that dependencies are light for e.g., BuildRoot embedded/VM targets. 3, Seamless over-subscription with key context cache (in ~/.cache/tpm2sh). Detects stale contexts from previous power cycles. “Cache keys” can be referred bit “key:<hex grip>” type of “URI”, where grip is 8 bytes of the key’s name hash.
- Seamless policy sessions with policy command, which can output both composite digest and session handle.
- Intuitive way to download vendor certificates from the chip.
- Full support for the TPMKey ASN.1 format, which is what kernel speaks.
Adding signing etc. ops would have been worse mistake to do before getting this basis right.
It’s not aiming to do all what tpm2-tools does but more like do stuff that I want to do and implementing that as a command-line tool :-) I.
#linux #kernel #tpm #rustlang #buildroot