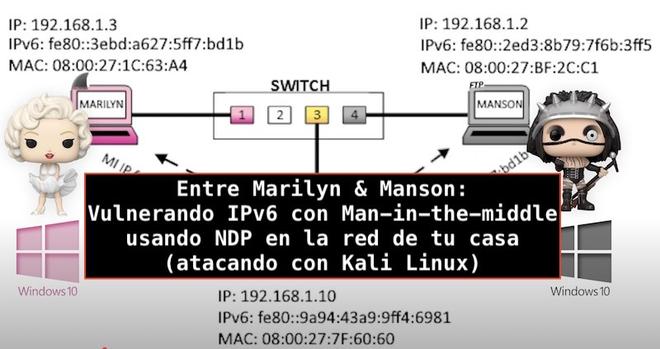
El lado del mal - Entre Marilyn & Manson: Vulnerando IPv6 con Man-in-the-middle usando NDP en la red de tu casa con Kali Linux https://www.elladodelmal.com/2025/05/entre-marilyn-manson-vulnerando-ipv6.html #Hacking #IPV6 #Mitm #redes #Wireshark #Kali #pentest #pentesting
#Mitm
Hello, readers and followers.
Last week, feeling rather bored, I decided to write a small script to assist in identifying centralised servers within the fediverse.
This is particularly useful as the fediverse is intended to be free, open, and decentralised, in order to safeguard democracy, free speech, and, most importantly, to protect democracy and human freedom, which are fundamental human rights and online privacy.
At this stage, the script identifies centralised and privacy-invasive servers operating on the #MITM networks of AWS, CloudFlare, and Azure (Microsoft). By now, we should all be aware that these networks are detrimental to privacy, as they do everything possible to identify you for the purpose of collecting your Personally Identifiable Information (PII), fingerprinting your browsers, and censoring the internet for those who refuse to be part of the walled garden.
The results from running the collection of previously connected servers to my fediverse instance are as in the file attached
#fediverse #freespeech #decentralization #cloudflare #crimeflare #infosec #privacy #azure #aws #amazon #onlineprivacy #privacymatters #democracy #protectdemocracy
Эти хакерские штучки
Привет, Хабр! На связи Аеза и сегодня мы хотели бы рассказать о так называемых “хакерских штучках” – устройствах, которые могут использоваться злоумышленниками для реализации различных атак. Возможно, многие наши читатели помнят статью о Flipper Zero . Это учебное устройство позволяло попрактиковаться в различных техниках тестирования на проникновение, таких как атаки BadUSB, копирование RFID-карт и брелоков iButton и других. Однако, в этой статье мы рассмотрим более серьезные устройства, предназначенные не для обучения, а для использования на практике, то есть для проведения атак или для тестов на проникновение. При этом мы постарались рассмотреть в статье решения, актуальные на начало 2025 года.
https://habr.com/ru/companies/aeza/articles/906946/
#киберпреступность #гаджеты #информационная_безопасность #хакинг #badusb #mitm #защита_данных #кибербезопасность
Lately I've been using Google messages on my android phone. I know, silly of a privacy focused person to do, but whatever.
Anyway, lately, when discussing taboo topics in my group chats such as web pen testing, or guns, messages sent to the chat are being dropped. I didn't receive a message with an SQL injection and I didn't receive a picture of an AK-47. I'm certain the rest of the group received these messages. I find it fundamentally wrong to have communications intercepted and dropped. In no way should Google determine whether or not I should receive information.
#fuckgoogle #mitm #unethical
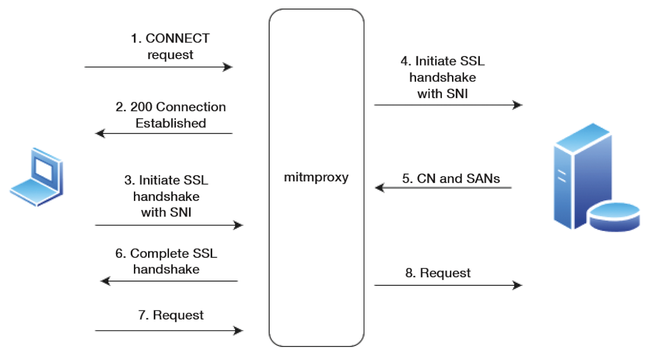
The developers of the mitmproxy tool describe it as the Swiss army knife for debugging, testing, data protection analysis, and penetration testing HTTP(S) connections. Holger Reibold shows you how mitmproxy can be a useful addition to your security toolbox.
https://www.admin-magazine.com/Archive/2025/85/Traffic-analysis-with-mitmproxy?utm_source=mlm
#OpenSource #mitmproxy #debugging #testing #security #proxy #MITM
@Linux #ClownFlare is literally a #ValueRemoving #RentSeeker that #MITM's traffic to capture #Logins in #PlainText & also acts as #RogueISP hosting everything from #CSAM to #Cybercrime and #Terrorism.
- There is no legitimate reason to use #CloudFlare for anything!
surely one of you #infosec peers has a guide or article on why #VPN services aren't the privacy silver bullet they often advertise themselves to be. something that mentions you're paying co-conspirators to #mitm your own traffic in addition to lowering the reputation to that of your new address space?
@ErikvanStraten@infosec.exchange
Dankjewel voor deze verhelderende uitleg. Ik heb er niet bij stilgestaan dat door Cloudflare grote blokken van het internet letterlijk kunnen worden uitgeschakeld, door simpelweg een script te draaien
#Risico #Economie #Cloudflare #Fastly #CDN #AitM #MitM #FISASection702 #FISA #ThreeLetterAgencies #Trump #Sbowden #E2EE #InfoSec #VVD #PVV #CIDI #VT #VirusTotal #DVCerts #DV #OV #EV #QWAC #CyberCrime #NepWebsites #FakeWebsites
@cR0w @troyhunt @dangoodin @benjojo @Viss @matthew_d_green
Seriously, #ClownFlare are at best a #ValueRemoving #MITM and more often than not a #RogueISP who's business model is a #RacketeeringScheme that should not exist to begin with.
- There is no legitimate reason to use #Cloudflare!
@0xF21D #ClownFlare is a #RogueISP and their #MITM-based approach eould've always allowed that.
- Why is ANYONE here surprised of that?
Don’t make me encrypt the data in the browser before sending it. #mitm
https://benjojo.co.uk/u/benjojo/h/cR4dJWj3KZltPv3rqX
Eavesdropping on Black-box Mobile Devices via Audio Amplifier’s EMR
https://www.ndss-symposium.org/wp-content/uploads/2024-240-paper.pdf
https://arcanechat.me server reached 1500 users!!!
the server is using around 1GB of RAM, CPU is almost unused, and only 1.4GB of storage used for encrypted user volatile data, that is around 1MB per user on average!
the cost of self-hosting a #chatmail server for #ArcaneChat / #DeltaChat is really low! and you don't even need to trust the server operator or even the VPS provider if you are selfhosting since all is #e2ee and safe against #mitm thanks to the green checkmark in chats
Uh, if that's Schrodinger's mouse, then clearly it's a Quantum MITM attack!!!
You need PQCs now!!! (Pest Quelling Cryptography)
@torproject same with #obfs4 bridges: there is no option to say like ports=80,443 or similar, which makes it cumbersome to get said bridges.
- And yes, for people stuck on #publicWiFi and shitty #MVNO|s this is most likely the only way they can get any #Tor connection work through #CGNAT and #firewall|s, as most do #BlockTor and it's associated #ports alongside common #proxy ports like 8000-9999 and anything they can't #MITM that isn't #HTTPS or #IMAP!
And trying to get places to #DontBlockTor that criminalize the use of #Tor is foolish at best.
Pros, cons and potential alternatives to Cloudflare for the #selfhost or #homelab.
https://blog.k3can.us/index.php?post/2025/02/Cloudflare-for-the-Selfhoster