Tomorrow is summer, it is time to summarize the FLOSS contributions and sponsoring we achieved in the past 3 months. There was mostly things about #oidc and #oauth tooling in #python
https://yaal.coop/blog/en/dernieres-contributions-logiciels-libres-printemps-2025
#OIDC
Demain c'est l'été, il est temps de faire le point sur le mécénat et les contributions à des logiciels libres commis par l'équipe de Yaal Coop ces 3 derniers mois ! Au menu, beaucoup de choses autour d'outils #oidc et #oauth en #python
https://yaal.coop/blog/dernieres-contributions-logiciels-libres-printemps-2025
#CyMaIS now supports #moodle with #SSO via #OIDC.
Implemented via https://github.com/kevinveenbirkenbach/cymais/tree/master/roles/docker-moodle
You can register and check out the demo here:
https://academy.cymais.cloud/
CC: @moodle @dag_moodle
#CyMaIS now supports #pixelfed with #SSO via #OIDC.
Implemented via https://github.com/kevinveenbirkenbach/cymais/tree/master/roles/docker-pixelfed
You can register and check out the demo here:
https://picture.cymais.cloud/
CyMaIS statt Workday: Digitale Souveränität für HR & Organisationen
Während viele Organisationen sich von Workday begeistern lassen, wird oft übersehen, dass diese Lösung in einer proprietären Blackbox läuft – mit allen Risiken von Vendor-Lock-in, Datenspeicherung in Drittstaaten und hohen Lizenzkosten.Doch es gibt eine echte Alternative: CyMaIS, das freie Framework für selbstbestimmte IT-Infrastruktur.
[…]
So, since I need #mobilizon to use only my external #authentik for user base, I think I'll try to set it up via #LDAP instead of #OIDC, since when OIDC is plugged in, it still offers it's own login form, and that's not something I like or want, fingers crossed
huh, WebFinger is also used in OpenID Connect
https://openid.net/specs/openid-connect-discovery-1_0.html#IssuerDiscovery
Zero Trust в облаке: практическое руководство
В этом руководстве рассматривается современный подход к безопасности — Zero Trust Network Access (ZTNA) — и показано, как его реализовать с помощью SPIFFE/SPIRE и OpenID Connect (OIDC). Материала много, по этому я предоставлю его в сухой форме. В основе ZTNA лежит принцип «никогда не доверяй, всегда проверяй»: каждый запрос на доступ считается потенциально небезопасным и проходит обязательную аутентификацию и авторизацию. По сравнению с классическими VPN-сетями решения ZTNA на базе SPIFFE/SPIRE и OIDC: Ускоряют процедуру аутентификации в 20–80 раз, Повышают производительность на 46–64 %, В облаках AWS и Google Cloud позволяют снизить задержки до 50–100 мс вместо привычных 2–4 с.
https://habr.com/ru/articles/917440/
#zerotrust #spiffe #spire #oidc #kubernetes #aws #gcp #ztna #security
I finally finished my #Fail2Ban setup and am quite happy with the result. I've got #discord and #email notifications, global IP banning (on all servers) and automatic reporting to #abuseipdb based on multiple factors. This is awesome.
I'm so happy that i took the time to set up #Authelia as it's a breeze to #protect a single #endpoint and cover 70-80% of all services.
#homelab #selfhosting #linux #security #sso #oidc #OpenIDConnect
Hey #pocketid users!
I submitted 2 feature requests on GitHub for Pocket-ID. Feel free to upvote them if you find them useful :-)
🚀 Feature: Approximate Location Recognizes Local IPv6 as LAN, Internal Network
https://github.com/pocket-id/pocket-id/issues/634
🚀 Feature: Global Audit Log Adds a Local Traffic Filter
https://github.com/pocket-id/pocket-id/issues/635
Thanks
Today I released the first version of #Lokksmith, a #KotlinMultiplatform OpenID Connect client library for #Android and #iOS. I've been working on this in my spare time for the past few weeks. I finally reached a state that I can proudly show to the world.
The first release contains a fully working implementation for Android. The iOS integration is not yet available. Any help regarding iOS is greatly appreciated.
New Open-Source Tool Spotlight 🚨🚨🚨
Pocket ID is an OIDC provider simplifying authentication with passkeys. No passwords. Think secure logins using Yubikeys or biometrics. Lightweight compared to Keycloak or Hydra and ideal for focused use cases. Built for Docker setups. #Passkeys #OIDC
🔗 Project link on #GitHub 👉 https://github.com/pocket-id/pocket-id
#Infosec #Cybersecurity #Software #Technology #News #CTF #Cybersecuritycareer #hacking #redteam #blueteam #purpleteam #tips #opensource #cloudsecurity
— ✨
🔐 P.S. Found this helpful? Tap Follow for more cybersecurity tips and insights! I share weekly content for professionals and people who want to get into cyber. Happy hacking 💻🏴☠️
AWS IAMのOIDC認可を理解する 〜 GitLab CI/CDからAWSのマネージメントコンソールにログイン案内を出してみる
https://qiita.com/ssc-ksaitou/items/34dd310271b33735f95b?utm_campaign=popular_items&utm_medium=feed&utm_source=popular_items
I love #PocketID, a light weight #selfhosted #OIDC using only #Passkey.
After using it for several months with an LXC installation using Proxmox Helper Scripts, I noticed that the service runs as root. I also learned that a VM installation is more secure than an LXC. This article will guide you through installing Pocket-ID as a non-root service on Debian. Additionally, there's an upgrade script included.
#Proxmox #debian #selfhosting #homelab #openID #passkeys #SSO
https://www.lucasjanin.com/2025/06/02/pocket-id-bare-metal-installation-on-debian
Après avoir utilisé #PocketID pendant plusieurs mois avec une installation LXC via les Proxmox Helper Scripts, j'ai remarqué que le service s'exécute en tant que root. J'ai également appris qu'une VM est plus sécurisée qu'un LXC. Cet article vous guidera dans l'installation de PocketID en tant que service non root sur Debian. De plus, un script de mise à niveau est inclus.
#Proxmox #debian #selfhosted #selfhosting #homelab #OIDC #openID #passkey #passkeys #SSO
https://www.lucasjanin.com/2025/06/02/pocket-id-installation-bare-metal-sur-debian/
Pocket-ID: Bare Metal Installation on Debian
After using PocketID for several months with an LXC installation and Proxmox Helper Scripts, I noticed that the service runs as root. I also learned that a VM installation is more secure than an LXC. This article will guide you on installing Pocket-ID as a non-root service on Debian.
Presentation
First, if you’re not familiar with Pocket-ID, it’s a modern and lightweight OIDC client designed for managing authentication for services like Authentic and Aurelia. Its unique feature is that it exclusively supports passkeys. I use it with several self-hosted services, including Proxmox, Proxmox Backup Server, Komodo, Betszel, Karakeep, and, of course, Headscale/Headplane. For more details, the official website will surely answer many of your questions. If a Docker installation is more suitable for your environment, I invite you to visit BlackVoid’s excellent post. It also details the configuration for using Pocket-ID to connect to Synology DSM.
Preamble
Since I’m not short on memory on my Proxmox node and I’m very particular about the security of my home lab, I set about installing a VM. This was laborious, as up to version 0.53, there were two services, numerous dependencies, and required compilations. Despite the many obstacles, I succeeded in my mission! Then, a few hours later, without even having time to savour my small victory, version 1.0 was released. This major revision greatly simplifies things, as it’s an executable. Here is the procedure for a streamlined installation as a service with a non-root user in a Proxmox Debian VM. This procedure should be relatively easy to adapt to other types of configurations. There are many other methods for installing Pocket-ID; I invite you to consult the installation page on the Pocket-ID website.
Preparing the VM in Proxmox
If you are in Proxmox, I invite you to install a Debian VM using the Proxmox Helper Scripts. It is also possible to do this with a lighter Alpine, but I have not yet embarked on this adventure. Choose the advanced mode and adjust for your situation, and change the hostname to “pocketid”.
bash -c "$(curl -fsSL https://raw.githubusercontent.com/community-scripts/ProxmoxVE/main/vm/debian-vm.sh)"QEMU
It’s a good practice to install the QEMU Guest Agent on your VM. You can follow these steps in the Proxmox console of the VM.
Update your package list:
sudo apt update && sudo apt upgrade -yInstall the Proxmox QEMU Guest Agent package:
sudo apt install qemu-guest-agent -yStart and enable the service:
sudo systemctl start qemu-guest-agentsudo systemctl enable emu-guest-agentVerify that the service is running:
sudo systemctl status qemu-guest-agentThis will ensure that the Proxmox QEMU Guest Agent is successfully installed and running on your Debian system.
Installing Pocket-ID
Get Debian ready
apt update && apt upgrade -yCreate a dedicated user
useradd -r -s /bin/false -m -d /opt/pocket-id pocketidInstall curl needed for the installation
apt install -y curlDownloading and Installing Pocket-ID
cd /opt/pocket-idARCH="amd64"LATEST_RELEASE_URL=$(curl -s https://api.github.com/repos/pocket-id/pocket-id/releases/latest | grep "browser_download_url.*pocket-id-linux-${ARCH}" | cut -d '"' -f 4)sudo curl -L -o pocket-id "${LATEST_RELEASE_URL}"sudo chmod +x pocket-idsudo chown pocketid:pocketid pocket-idCreating directories for Pocket-ID data
sudo mkdir -p /opt/pocket-id/data/uploadsPocket-ID configuration file. To locate visitors’ IP addresses, I invite you to create an API key on the Maxmind website.
sudo nano /opt/pocket-id/.envAPP_URL=https://id.xxxx.xxPORT=1411# Database: SQLite, file located at /opt/pocket-id/data/db.sqlite# (relative to WorkingDirectory=/opt/pocket-id)DB_CONNECTION_STRING=file:data/db.sqlite?_journal_mode=WAL&_busy_timeout=2500&_txlock=immediate# Optional: Maxmind License Key for IP GeolocationMAXMIND_LICENSE_KEY="YOUR-MAXMIND-LICENSE-KEY"# Optional: Logging level (debug, info, warn, error)LOG_LEVEL=infoMake sure all Pocket-ID files have the correct user permissions.
sudo chown pocketid:pocketid /opt/pocket-id/.envsudo chmod 600 /opt/pocket-id/.envSetting up the Pocket-ID service
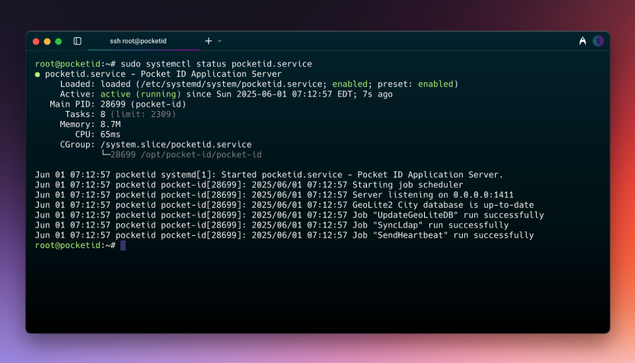
sudo nano /etc/systemd/system/pocketid.service[Unit]Description=Pocket ID Application ServerAfter=network.target[Service]Type=simpleUser=pocketidGroup=pocketidWorkingDirectory=/opt/pocket-idExecStart=/opt/pocket-id/pocket-idEnvironmentFile=/opt/pocket-id/.envRestart=alwaysRestartSec=10NoNewPrivileges=truePrivateTmp=true[Install]WantedBy=multi-user.targetsudo systemctl daemon-reloadsudo systemctl enable pocketid.servicesudo systemctl start pocketid.servicesudo systemctl status pocketid.serviceIf everything goes as planned, you should receive a confirmation.
● pocketid.service - Pocket ID Application Server Loaded: loaded (/etc/systemd/system/pocketid.service; enabled; preset: enabled) Active: active (running) since Sun 2025-06-01 07:12:57 EDT; 7s ago Main PID: 28699 (pocket-id) Tasks: 8 (limit: 2309) Memory: 8.7M CPU: 65ms CGroup: /system.slice/pocketid.service └─28699 /opt/pocket-id/pocket-idJun 01 07:12:57 pocketid systemd[1]: Started pocketid.service - Pocket ID Application Server.Jun 01 07:12:57 pocketid pocket-id[28699]: 2025/06/01 07:12:57 Starting job schedulerJun 01 07:12:57 pocketid pocket-id[28699]: 2025/06/01 07:12:57 Server listening on 0.0.0.0:1411Jun 01 07:12:57 pocketid pocket-id[28699]: 2025/06/01 07:12:57 GeoLite2 City database is up-to-dateJun 01 07:12:57 pocketid pocket-id[28699]: 2025/06/01 07:12:57 Job "UpdateGeoLiteDB" run successfullyJun 01 07:12:57 pocketid pocket-id[28699]: 2025/06/01 07:12:57 Job "SyncLdap" run successfullyJun 01 07:12:57 pocketid pocket-id[28699]: 2025/06/01 07:12:57 Job "SendHeartbeat" run successfullyCaddy Reverse Proxy
Here is my Caddyfile with the /robots.txt file in case it is respected (it’s nice to dream).
# Snippet for robots.txt(common_robots_txt) {handle /robots.txt {# Set the Content-Type headerheader Content-Type "text/plain; charset=utf-8"# Respond with the body and status code 200respond `User-agent: *Disallow: /` 200}}# Pocket-IDid.xxxx.xx {import common_robots_txt# Fallback to reverse proxy for other requestsreverse_proxy 192.168.x.yyy:1411 [xxxx:xxxx:xxxx:xxxx::yyyy]:1411}systemctl reload caddy.service For the first setup of your Pocket-ID instance, I invite you to create your administrator account at https://id.xxxx.xx/login/setup.It is strongly encouraged to have two passkeys since this is the only way to authenticate. I have one in Bitwarden/Vaultwarden and another in iCloud Keychain (via Safari).
Update
Since we’re not using Docker, updating can be a bit more complicated. However, it’s nothing insurmountable, especially since version 1.0 is already compiled. Here’s a small update script that allowed me to move from version 1.0 to 1.1.0 without a hitch.
nano /root/update-pocketid.sh#!/bin/bash# update-pocketid.sh# --- Configuration ---INSTALL_DIR="/opt/pocket-id"SERVICE_NAME="pocketid.service"USER="pocketid"GROUP="pocketid"VERSION_FILE="${INSTALL_DIR}/version.txt" ARCHITECTURE="amd64" # Change if needed (e.g., arm64)# --- End Configuration ---echo "Checking for the latest version of PocketID..."LATEST_TAG_JSON=$(curl -s https://api.github.com/repos/pocket-id/pocket-id/releases/latest)LATEST_TAG=$(echo "$LATEST_TAG_JSON" | grep '"tag_name":' | sed -E 's/.*"v([^"]+)".*/\1/') # Version without 'v'LATEST_TAG_WITH_V=$(echo "$LATEST_TAG_JSON" | grep '"tag_name":' | sed -E 's/.*"([^"]+)".*/\1/') # Version with 'v'if [ -z "$LATEST_TAG" ]; then echo "Could not retrieve the latest version from GitHub." exit 1fiecho "Latest version available: v${LATEST_TAG}"CURRENT_VERSION="0" # Default to 0 if no version fileif [ -f "$VERSION_FILE" ]; then CURRENT_VERSION=$(cat "$VERSION_FILE")fiecho "Currently installed version: v${CURRENT_VERSION}"if [ "$LATEST_TAG" = "$CURRENT_VERSION" ]; then echo "PocketID is already up to date (v${CURRENT_VERSION})." exit 0fiecho "New version v${LATEST_TAG} available. Updating..."DOWNLOAD_URL=$(echo "$LATEST_TAG_JSON" | grep -E "browser_download_url.*pocket-id-linux-${ARCHITECTURE}" | cut -d '"' -f 4)if [ -z "$DOWNLOAD_URL" ]; then echo "Could not find the download URL for linux-${ARCHITECTURE} and version v${LATEST_TAG}." exit 1fiecho "Stopping service ${SERVICE_NAME}..."sudo systemctl stop "${SERVICE_NAME}"echo "Backing up the old binary..."BACKUP_NAME="pocket-id_backup_v${CURRENT_VERSION}_$(date +%Y%m%d_%H%M%S)"sudo cp "${INSTALL_DIR}/pocket-id" "${INSTALL_DIR}/${BACKUP_NAME}"echo "Old binary backed up to ${INSTALL_DIR}/${BACKUP_NAME}"Make the script executable
sudo chmod +x /root/update-pocketid.shCreate an alias
alias update='/root/update-pocketid.sh'Consider updating the system before updating Pocket-ID.
sudo apt update && sudo apt upgrade -yIf you are using Proxmox, I encourage you to take a snapshot just before the update and have regular backups (you never know :-).
Conclusion
Now, you are ready to step into the future with OIDC and Passkey. You can visit the Client Examples page to easily configure your services with Pocket-ID. I wish you a safe journey into the exciting world of self-hosting!
Pocket-ID: Installation Bare-metal sur Debian
Après avoir utilisé PocketID pendant de nombreux mois via une installation dans un LXC avec les Proxmox Helper Scripts, j’ai constaté que le service tourne en tant que root. De plus, j’ai lu qu’une installation dans une VM s’avère davantage sécurisée qu’un LXC.
Présentation de Pocket-ID
Avant toute chose, si vous ne connaissez pas Pocket-ID, c’est un client OIDC moderne et léger pour gérer l’authentification de vos services tels qu’Authentific, Aurelia, etc. Sa particularité est qu’il ne prend en charge que les passkeys. Je l’utilise avec de nombreux services auto-hébergés tels que Proxmox, Proxmox Backup Server, Komodo, Betszel, Karakeep, et évidemment Headscale/Headplane. Pour davantage de détails, le site officiel répondra sûrement à beaucoup de vos questions. Si une installation via Docker est plus adaptée à votre environnement, je vous invite à visiter l’excellent billet de BlackVoid en anglais. Il détaille également la configuration pour utiliser Pocket-ID afin de se connecter à Synology DSM.
Préamble
Étant donné que je ne manque pas de mémoire sur mon nœud Proxmox et que je suis très attentif au niveau de sécurité de mon homelab, je me suis lancé dans l’installation d’une VM. Cela a été laborieux, car jusqu’à la version 0.53, il y avait deux services, de nombreuses dépendances et des compilations nécessaires. Malgré les nombreux obstacles, j’ai réussi ma mission ! Puis, quelques heures après, sans avoir même eu le temps de savourer ma petite victoire, la version 1.0 est sortie. Cette révision majeure simplifie grandement les choses, car c’est un exécutable. Voici la procédure pour une installation simplifiée en tant que service avec un utilisateur non root dans une VM Debian de Proxmox. Cette procédure devrait pouvoir s’adapter relativement facilement à d’autres types de configurations. Il existe beaucoup d’autres méthodes pour installer Pocket-ID, je vous invite à consulter la page “installation” sur du site de Pocket-ID.
Préparation de la VM dans Proxmox
Si vous êtes dans Proxmox, je vous invite à installer une VM Debian en utilisant les Proxmox Helper Scripts. Il est également possible de le faire avec une Alpine plus légère, mais je ne me suis pas encore lancé dans cette aventure. Choisir le mode mode advanced et ajuste pour votre situation et changer le nom du host à “pocketid”.
bash -c "$(curl -fsSL https://raw.githubusercontent.com/community-scripts/ProxmoxVE/main/vm/debian-vm.sh)"QEMU
Il est recommandé d’installer l’agent invité QEMU sur votre machine virtuelle. Vous pouvez suivre ces étapes dans la console Proxmox de la machine virtuelle.
Mettre à jour la liste des paquets :
sudo apt update && sudo apt upgrade -yInstaller le paquet Proxmox QEMU Guest Agent :
sudo apt install qemu-guest-agent -yDémarrer et activer le service :
sudo systemctl start qemu-guest-agentsudo systemctl enable emu-guest-agentVérifier que le service est en cours d’exécution
sudo systemctl status qemu-guest-agentCela garantira que l’agent invité Proxmox QEMU est correctement installé et exécuté sur votre système Debian.
Installation de Pocket-ID
Préparation du système
apt update && apt upgrade -yCréer un utilisateur dédié
useradd -r -s /bin/false -m -d /opt/pocket-id pocketidInstaller les dépendances nécessaires à l’installation
apt install -y curlTéléchargement et Installation de PocketID
cd /opt/pocket-idARCH="amd64"LATEST_RELEASE_URL=$(curl -s https://api.github.com/repos/pocket-id/pocket-id/releases/latest | grep "browser_download_url.*pocket-id-linux-${ARCH}" | cut -d '"' -f 4)sudo curl -L -o pocket-id "${LATEST_RELEASE_URL}"sudo chmod +x pocket-idsudo chown pocketid:pocketid pocket-idCréation des répertoires pour les données de Pocket-ID
sudo mkdir -p /opt/pocket-id/data/uploadsFichier de configuration de Pocket-ID. Pour obtenir la localisation des adresses IP des visiteurs, je vous invite à créer une clé API sur le site de Maxmind.
sudo nano /opt/pocket-id/.envAPP_URL=https://id.xxxx.xxPORT=1411# Database: SQLite, file located at /opt/pocket-id/data/db.sqlite# (relative to WorkingDirectory=/opt/pocket-id)DB_CONNECTION_STRING=file:data/db.sqlite?_journal_mode=WAL&_busy_timeout=2500&_txlock=immediate# Optional: Maxmind License Key for IP GeolocationMAXMIND_LICENSE_KEY="YOUR-MAXMIND-LICENSE-KEY"# Optional: Logging level (debug, info, warn, error)LOG_LEVEL=infoAssurez-vous que tous les fichiers de pocket-ID soient avec les bonnes permissions d’utilisateur.
sudo chown pocketid:pocketid /opt/pocket-id/.envsudo chmod 600 /opt/pocket-id/.envMise en place du service Pocket-ID
sudo nano /etc/systemd/system/pocketid.service[Unit]Description=Pocket ID Application ServerAfter=network.target[Service]Type=simpleUser=pocketidGroup=pocketidWorkingDirectory=/opt/pocket-idExecStart=/opt/pocket-id/pocket-idEnvironmentFile=/opt/pocket-id/.envRestart=alwaysRestartSec=10NoNewPrivileges=truePrivateTmp=true[Install]WantedBy=multi-user.targetsudo systemctl daemon-reloadsudo systemctl enable pocketid.servicesudo systemctl start pocketid.servicesudo systemctl status pocketid.serviceSi tout se passe comme prévu, vous devriez recevoir une confirmation.
● pocketid.service - Pocket ID Application Server Loaded: loaded (/etc/systemd/system/pocketid.service; enabled; preset: enabled) Active: active (running) since Sun 2025-06-01 07:12:57 EDT; 7s ago Main PID: 28699 (pocket-id) Tasks: 8 (limit: 2309) Memory: 8.7M CPU: 65ms CGroup: /system.slice/pocketid.service └─28699 /opt/pocket-id/pocket-idJun 01 07:12:57 pocketid systemd[1]: Started pocketid.service - Pocket ID Application Server.Jun 01 07:12:57 pocketid pocket-id[28699]: 2025/06/01 07:12:57 Starting job schedulerJun 01 07:12:57 pocketid pocket-id[28699]: 2025/06/01 07:12:57 Server listening on 0.0.0.0:1411Jun 01 07:12:57 pocketid pocket-id[28699]: 2025/06/01 07:12:57 GeoLite2 City database is up-to-dateJun 01 07:12:57 pocketid pocket-id[28699]: 2025/06/01 07:12:57 Job "UpdateGeoLiteDB" run successfullyJun 01 07:12:57 pocketid pocket-id[28699]: 2025/06/01 07:12:57 Job "SyncLdap" run successfullyJun 01 07:12:57 pocketid pocket-id[28699]: 2025/06/01 07:12:57 Job "SendHeartbeat" run successfullyReverse Proxy avec Caddy
Voici mon Caddyfile avec le fichier /robots.txt au cas où il serait respecté (c’est beau de rêver).
# Snippet for robots.txt(common_robots_txt) {handle /robots.txt {# Set the Content-Type headerheader Content-Type "text/plain; charset=utf-8"# Respond with the body and status code 200respond `User-agent: *Disallow: /` 200}}# Pocket-IDid.xxxx.xx {import common_robots_txt# Fallback to reverse proxy for other requestsreverse_proxy 192.168.x.yyy:1411 [xxxx:xxxx:xxxx:xxxx::yyyy]:1411}systemctl reload caddy.service Pour la première configuration de votre instance Pocket-ID, je vous invite à créer votre compte administrateur sur https://id.xxxx.xx/login/setup. Il est très fortement encouragé d’avoir deux passkeys vu que c’est la seule manière d’authentification. J’en ai une dans Bitwarden/Vaultwarden et une autre dans le trousseau iCloud (via Safari).
Mise à jour
Puisque nous ne sommes pas dans Docker, la mise à jour peut être un peu plus compliquée. Cependant, rien d’insurmontable, surtout depuis la version 1.0 déjà compilée. Voici un petit script de mise à jour qui m’a permis de passer de la version 1.0 à 1.1.0 sans encombre.
nano /root/update-pocketid.sh#!/bin/bash# update-pocketid.sh# --- Configuration ---INSTALL_DIR="/opt/pocket-id"SERVICE_NAME="pocketid.service"USER="pocketid"GROUP="pocketid"VERSION_FILE="${INSTALL_DIR}/version.txt" ARCHITECTURE="amd64" # Change if needed (e.g., arm64)# --- End Configuration ---echo "Checking for the latest version of PocketID..."LATEST_TAG_JSON=$(curl -s https://api.github.com/repos/pocket-id/pocket-id/releases/latest)LATEST_TAG=$(echo "$LATEST_TAG_JSON" | grep '"tag_name":' | sed -E 's/.*"v([^"]+)".*/\1/') # Version without 'v'LATEST_TAG_WITH_V=$(echo "$LATEST_TAG_JSON" | grep '"tag_name":' | sed -E 's/.*"([^"]+)".*/\1/') # Version with 'v'if [ -z "$LATEST_TAG" ]; then echo "Could not retrieve the latest version from GitHub." exit 1fiecho "Latest version available: v${LATEST_TAG}"CURRENT_VERSION="0" # Default to 0 if no version fileif [ -f "$VERSION_FILE" ]; then CURRENT_VERSION=$(cat "$VERSION_FILE")fiecho "Currently installed version: v${CURRENT_VERSION}"if [ "$LATEST_TAG" = "$CURRENT_VERSION" ]; then echo "PocketID is already up to date (v${CURRENT_VERSION})." exit 0fiecho "New version v${LATEST_TAG} available. Updating..."DOWNLOAD_URL=$(echo "$LATEST_TAG_JSON" | grep -E "browser_download_url.*pocket-id-linux-${ARCHITECTURE}" | cut -d '"' -f 4)if [ -z "$DOWNLOAD_URL" ]; then echo "Could not find the download URL for linux-${ARCHITECTURE} and version v${LATEST_TAG}." exit 1fiecho "Stopping service ${SERVICE_NAME}..."sudo systemctl stop "${SERVICE_NAME}"echo "Backing up the old binary..."BACKUP_NAME="pocket-id_backup_v${CURRENT_VERSION}_$(date +%Y%m%d_%H%M%S)"sudo cp "${INSTALL_DIR}/pocket-id" "${INSTALL_DIR}/${BACKUP_NAME}"echo "Old binary backed up to ${INSTALL_DIR}/${BACKUP_NAME}"Rendre le script exécutable
sudo chmod +x /root/update-pocketid.shJ’ai ajouté dans mes alias.
alias update='/root/update-pocketid.sh'Pensez à faire une mise à jour du système avant celle de Pocket-ID.
sudo apt update && sudo apt upgrade -ySi vous utilisez Proxmox, je vous encourage à faire un snapshot juste avant la mise à jour et à avoir des sauvegardes régulières (on ne sait jamais :-).
Conclusion
Vous êtes maintenant prêt a entrer dans le futur avec OIDC et Passkey. Vous pouvez visiter la page Exemples de clients pour configurer facilement vos services avec Pocket-ID. Je vous souhaite un bon voyage dans le monde captivant de l’auto-hébergement !
Blogged: Handling OpenID Connect error events in ASP.NET Core
https://damienbod.com/2025/06/02/handling-openid-connect-error-events-in-asp-net-core/
#aspnetcore #dotnet #identity #openidconnect #oauth #oidc #iam