#flashback with this #soundtrack of the #performance “Microcosmos” I #composed in #copenhagen
A Fabulous #show for #young #audiences created by Giacomo Ravicchio - #production : Meridiano #theater 🇩🇰
A #journey of #visual #magic for #children to #discover the #sizes of #things , large, small, #scale of #universe versus the one of an #ant
For this #music I #explored many #timbres of the #bassclarinet its #sounds #harmonics #percussions merged with #minimal #electro
#SCaLE
LLM-D: Kubernetes-Native Distributed Inference at Scale
https://github.com/llm-d/llm-d
#HackerNews #LLM-D #Kubernetes #Distributed #Inference #Scale #MachineLearning
[. . . 2 of 2 thread on binary fractal in computing]
Take the following real world network structure as an illustration of that point. #Purism provides a mobile network service called AweSIM. That is a private company network inside of T-mobile which is owned by Deutsche Telecom which operates in many countries around the world. The internet backbone is inside the US (with various intercept points throughout) but the nature of the internet is global. The internet is not a local intranet.
We’ve all seen illustrations of scale that take the following form: your house, your country, your planet, the solar system, the milky way. Computing and networking are essentially re-namings of scale relationships.
AweSIM is a VPN (plus mobile network) inside an ISP inside a global internet. There may be further subdivisions inside that “VPN.” What if you used a “VPN” inside a VPN, a walled network inside another walled network? We do all the time. https inside a VPN is not entirely visible to the VPN. SSL and private DNS still encrypts even if the domain name can be known by the network provider. For even greater privacy, a circuit of connections can be connected to multiple circuits of proxies just as a VPN can take multiple hops (i.e Tor). So really, it is all a matter of sub- and super- division in addition to certain other network design principles.
You can even think in terms of this scale paradigm when people start moaning that FTP is plaintext. The real reason my friends like this protocol is that FTP also stands for F the Police. https://ftp. - is not plaintext. It is like a VPN inside a ISP; an non-encrypted domain inside encryption. Do you think an onionsite is plaintext if it is http: //56randomcharacters .onion? Remember, just http and no s! No, of course not.
The question is: where is the wall of your scale and who has permission to get in?
#FTP #Encryption #Security #networking #CS #Tor #VPN #ISP #Scale
First plague, then war.
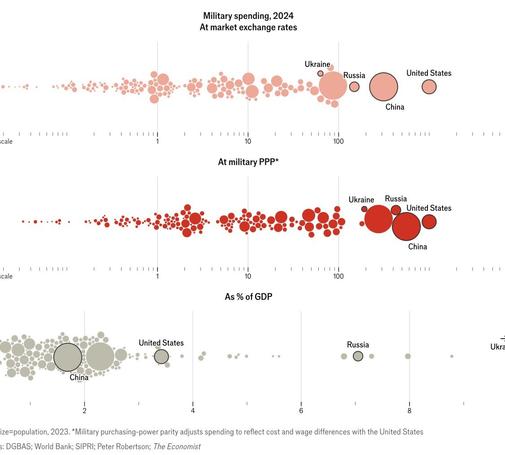
“Regardless of which measure you consult, the past year has seen a sharp increase in global #spending on #defence. Budgets totalled $2.7trn in 2024—up by 9.4% from 2023, the biggest jump since at least 1988.
#Military outlays now account for 2.5% of countries’ gdp on average, and 7.1% of government budgets. But the increase is even steeper when adjusted for purchasing power (see chart 1). With help from #PeterRobertson of the #UniversityofWesternAustralia, we estimate that global #defence #spending rose by 10% in real terms.”
What got me to read the article? The notation, “$bn, log scale” graph. #Graphs shown in log #scale.
Meaning the economist pitch to readership is high in statistical education OR it’s from an Academic source.
<https://archive.md/I8SBL> / <https://www.economist.com/graphic-detail/2025/05/16/how-do-countries-rank-by-military-spending> (paywall)
#macro #nature #insect #scale #auswildlife #insectsofaustralia #insectsofthefediverse
Garbage Collection of Object Storage at Scale
#HackerNews #GarbageCollection #ObjectStorage #Scale #TechInnovation #DataManagement #CloudComputing
#BSI WID-SEC-2025-0996: [NEU] [mittel] #IBM #Storage #Scale: Mehrere Schwachstellen
Ein entfernter, authentisierter Angreifer kann mehrere Schwachstellen in IBM Storage Scale ausnutzen, um beliebigen Programmcode auszuführen oder einen Denial-of-Service auszulösen.
https://wid.cert-bund.de/portal/wid/securityadvisory?name=WID-SEC-2025-0996
#scale : the thin metallic side plate of the handle of a pocketknife. see illust. of pocketknife
- French: échelle
- German: die Skala
- Italian: bilancia
- Portuguese: balança
- Spanish: escala
------------
Join our new subreddit for language learners @ https://reddit.com/r/LearnANewLanguage
Tuning Timbre Spectrum Scale
https://sethares.engr.wisc.edu/ttss.html
#HackerNews #Tuning #Timbre #Spectrum #Scale #music #theory #sound #design #acoustics #frequency
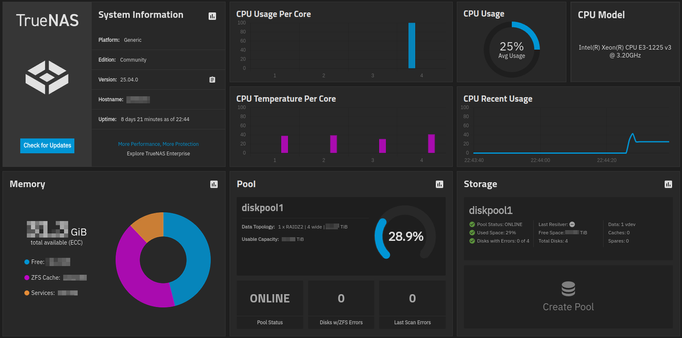
Just for fun... i (very) recently built myself a "real" NAS, to be honest, the very first one i ever own as such..
I reused some pc i had sitting inactive for some few years after i got it as a gift..
Had to put at least a nice amount of ram, harddisk and SSD space into it (mkay, for SSD, even a single 16gig sata drive would do... maybe even a usb stick in a pinch, but have it be USB3 or faster at least. ;))
So now i have a nice dashboard like this:
I first had another (more nas styled) box where i threw in 3 older 500gig sata disks to test out some few options, but to be honest, after looking at truenas and a short run of HexOS, i didn't even want to try out Unraid or others... Truenas fits the bill perfectly. ;)
No i'm not sponsored and no i don't wanna brag about what a nice big nas i have or something .. just put out a nice screenshot of something which solves any storage concerns i have for now and the forseeable future. ;)
(For the nerds: It is a dual-sata-ssd mirror for the boot-pool and a 4 sata spinning rust drive storage pool in raidz2, which means i can lose 2 of the 4 drives before i lose data. OpenZFS rocks too! ;) ;)
#RandomShit #TrueNAS #Scale #DIY #NAS #ZFS #OpenZFS #HomeStorage
April 30, 2025: Weighing Krishna with gold*. ⚖️
ಶ್ರೀಕೃಷ್ಣ ಸುವರ್ಣ ತುಲಾಭಾರ
shree krishna suwarna tulaabhaara
On account of "akshaya tadige".
*Make believe: The idol can't be weighed because it is permanently installed; can't be moved.
#Udupi #Krishna #Hindu #Religion #India #Kannada #Sanskrit #temple #gold #scale #balance #weigh #orange #festival #seated #Wednesday
#KnowledgeByte: The #Kardashev #Scale was developed as a way of measuring a civilization's technological advancement based upon how much usable #Energy it has at its disposal.
Here is a short overview.
https://knowledgezone.co.in/posts/What-is-Kardashev-scale-5ea95d0b247bb32e6075ab46
On a clear day, it's visible from huge areas of Yorkshire.
#Yorkshire #Scale #Distance #Tower #EmleyMoor
@errpunkterr #Unraid ist ein gutes NAS System. Nicht umsonst hat es viele Anhänger. Für mich ist das nichts. Mein #TrueNAS #Scale schnurrt wie ein Kätzchen. 😉
You don't have to chase the commercial endeavor, but it may come [...] to you. [...] So I would think of it this way: If you want there to be peace in the project, give people extension points where necessary, so that everything doesn't have to flow into core in order to feel like it's a first class citizen. - @kelseyhightower at PlanetNix 2025
Quite some interesting takes by Kelsey on the Nix project. I hope we can get to a point where commercial and non-commercial interests can co-exist in the project. Watch the full thing here:
Fireside Chat with Kelsey Hightower: An Outsider’s Look at Nix
https://youtu.be/caxcawUCSZ8
#Nix #NixOS #Kubernetes #OpenSource #SCALE #PlanetNix @planetnix
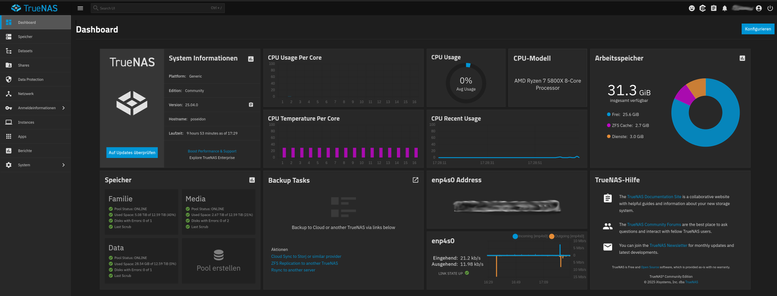
Das #Dashboard von #TrueNAS #Scale sieht einfach aufgeräumt und Professionell aus.
Bevor ich auf #TrueNAS #Scale umgestiegen bin, war meine erste Wahl für NAS-SW ganz klar #UnRaid – vor allem wegen der größeren Flexibilität bei der Hardware. Was ich jedoch nie nachvollziehen konnte: Wie kann man sich bei einem Betriebssystem ausgerechnet auf einen USB-Stick als Bootmedium verlassen? Die Probleme damit sind doch quasi vorprogrammiert. TNAS ist sicherlich auch nicht fehlerfrei, aber dass es nicht vom USB-Stick bootet, ist definitiv ein Pluspunkt.