It's wild how wrong the amd's programmer manual(https://www.amd.com/content/dam/amd/en/documents/processor-tech-docs/programmer-references/26568.pdf) is wrong. it says one thing and then later on contrast it....
for example,
In AESDEC instruction the description says "Performs one decryption round on a state value in xmm1 using the key value in xmm2 or mem128. Writes results to xmm1." so we can assume that the xmm1 will be the destination register right? wrong it's the xmm2 register! why I don't know ask AMD.
#linux #gnu #lowlevelprogramming #programming #assembly
#lowlevelprogramming
Unlocking the Power of VLSI in Automotive and Embedded Systems
Join yours Educational open Source community
👉 Download Now from Google Play
🔗 https://play.google.com/store/apps/details?id=com.piembsystech&pcampaignid=web_share
👉 Visit for more :
🌎 https://piembsystech.com/basic-understanding-of-vlsi/
#VLSIDesign #EmbeddedSystems #AutomotiveElectronics #ChipDesign #SystemOnChip #CMOSTechnology #SemiconductorEngineering #ECUDevelopment #ADAS #BMS #VehicleNetworking #ASICDesign #RTLDesign #MicrocontrollerDesign #HardwareArchitecture #AutomotiveSoftware #LowLevelProgramming
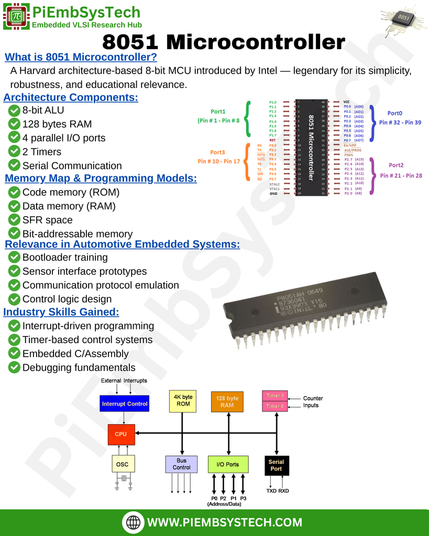
8051 Microcontroller
Join yours Educational open Source community
👉 Download Now from Google Play
🔗 https://play.google.com/store/apps/details?id=com.piembsystech&pcampaignid=web_share
👉 Visit for more :
🌍 https://piembsystech.com/8051-microcontroller/
#8051Microcontroller #EmbeddedSystems #AutomotiveEmbedded #ECUProgramming
#MCUDevelopment #CANProtocol #UDSProtocol #LowLevelProgramming
#PiEmbSysTech #MicrocontrollerBasics #KeilSoftware #AssemblyLanguage
#EmbeddedC #InterruptHandling #TimersAndCounters #EmbeddedArchitecture
#IoTDevices #RealTimeEmbedded
🎩✨ Behold, the riveting saga of #syscalls on OpenBSD! Because, naturally, manually entering addresses for every build wasn't enough of a party 🚀. Now, watch in awe as one brave soul ports a "real" application to raw syscalls—truly, the Shakespeare of low-level programming! 🐢🔧
https://nullprogram.com/blog/2025/03/06/ #OpenBSD #lowlevelprogramming #technews #softwaredevelopment #codingadventures #HackerNews #ngated
https://github.com/kolunmi/gtk-crusader-village is a AIV editor made by @kolunmi is so cool! please check him out 🥺
💻 CodeForge Live | S1E4 starts today!
We’re diving into x86 32-bit assembly, breaking down how registers work and writing a simple program to reinforce key concepts. If you’re into low-level programming, pull up a chair—we’re getting hands-on.
🔴 Live soon! #Assembly #LowLevelProgramming #CodeForgeLive
#Programming
#ComputerScience
⚙️ CodeForge Live - S1E2! 🔥
We’re taking a step back before moving forward—today, we’re diving into the fundamentals of x86 Assembly before continuing our bootloader journey. Understanding the low-level stuff is key, so we’re breaking it down in a hands-on, beginner-friendly way! 💻✨
🔴 Live later today! https://youtube.com/@geekstaparadise
I'm working on a new project called #fox #monitor.
This project is a simple system monitor #software for #linux os.
Check this out :honeybadger:
#c #cpp #lowlevelprogramming #clanguage #code #programming #systemmonitor #application #app
https://github.com/Mr-Fox-h/fox_monitor
💥 Want to see how simple ASM can be and dilly-dally some more with syscalls and OS security mechanisms?
Then, "Let's Reflect: Simple ASM Review and OS Security Mechanisms"
🎯 Want to level up your low-level programming?
Check out yet another blog entry: https://dreaming-of-dragons.blogspot.com/2024/12/wherein-we-pause-to-reflect-simple-asm.html
#ASM #ReverseEngineering #Linux #TechBlog #LowLevelProgramming #Syscalls #Security #GDB
Have you ever followed this rule when programming in C++ ?
Inclusive Language
Use inclusive language and avoid terms that other programmers might find disrespectful or offensive (such as "master", "slave" and "blacklist")
https://google.github.io/styleguide/cppguide.html#Inclusive_Language
🔍 Lost in the maze of debugging? I've got your map: the "Useful GDB Commands" Quick Reference Guide!
In this post you'll find:
--> 🎯 Essential commands to control program execution
--> 🔬 Memory inspection tricks that actually work
--> 🛠️ Compilation flags to make debugging easier
👉 Check out the full guide here: https://dreaming-of-dragons.blogspot.com/2024/10/useful-gdb-commands.html
#Debugging #GDB #ReverseEngineering #LowLevelProgramming #TechBlog #CProgramming #Linux #ProgrammingTips #ASM
Exciting news for low-level devs! Learn Rust the Dangerous Way series is a game-changer for firmware, game engine and OS kernel devs looking to up their game with Rust. You won't regret digging in. #Rust #LowLevelProgramming #SystemsProgramming https://cliffle.com/p/dangerust/
Ready to navigate the treacherous waters of buffer overflows?
Check my latest blog post: "Wherein We Study A Buffer Overflow And Ready Our Aim: testing the waters"
We'll now be ready to actually exploit the return address and use it for our own means.
Consider this the first step before shellcoding gallore.
🦶 Dip your toe here: https://dreaming-of-dragons.blogspot.com/2024/10/wherein-we-study-buffer-overflow.html
#Shellcode #CyberSecurity #ReverseEngineering #LowLevelProgramming #TechBlog #ExploitDevelopment
Ready for the troubled waters of shellcode? I'm not. Not just yet, at least. But I'm by the shore and telling you about it in my latest blog post: "Wherein We Wade Through A Shellcode Shore: before the dive
"
Spoiler alert: shellcode remains relevant (and fun).
👉 Check out: https://dreaming-of-dragons.blogspot.com/2024/10/wherein-we-wade-through-shellcode-shore.html
#Shellcode #CyberSecurity #ReverseEngineering #LowLevelProgramming #TechBlog #ExploitDevelopment
Gibson machine loaded, let's crack another program's password in my latest blog post:
'Wherein I Crack A Simple Program: level Leviathan'
All within a real, true, certified, classy Gibson machine (or so I was told).
This post is the second in my series on breaking increasingly secure programs.
So let’s unravel these fun topics together—one byte at a time!
👉 Check out the full post here: https://dreaming-of-dragons.blogspot.com/2024/10/wherein-i-crack-simple-program-level.html
#ReverseEngineering #CyberSecurity #LowLevelProgramming #TechBlog #CodeDive
Check out my latest article: Is http://main.py == main.txt? 🐍💻 https://linkedin.com/pulse/mainpy-maintxt-akshat-singh-ux0yc
New blog post:
"Wherein I Crack A Simple Program: level 1"
In this post I'll cover:
🖥️ xxd to view binary data
📜 readable strings with strings
🔍 function calls with ltrace
🕵️ gdb for deeper insights
👉 Check out the full journey here:
https://dreaming-of-dragons.blogspot.com/2024/10/wherein-i-crack-simple-program-level-1.html
Next level, we'll be tackling basic obfuscation techniques and environment variables.
🐍 Join me in this exploration of Reverse Engineering!
#ReverseEngineering #CProgramming #Cybersecurity #LowLevelProgramming #CTF
Want to play some fun hacking games? 🕵️♂️
Then this intermezzo is for you 👉 https://dreaming-of-dragons.blogspot.com/2024/09/wherein-i-finish-bandit-game-otw-part-2.html
I've recently finished the Bandit game in Over The Wire and decided to share a couple of tips and ideas I'd like to have known before starting the game myself.
No spoilers. Or your money back! ☺️
#overthewire #CTF #OTW #ReverseEngineering #EthicalHacking #Cybersecurity #LowLevelProgramming #CodeDive
🕵️♂️ I got hacked, and because of that you get my 6th blog post: "Wherein I Get Hacked And Learn In The Process: OTW" 🔐
Ever had a friendly chat with a "hacker" in OverTheWire? I have.
👉 Join the adventure here: https://dreaming-of-dragons.blogspot.com/2024/09/wherein-i-get-hacked-and-learn-in.html
#overthewire #CTF #OTW #ReverseEngineering #EthicalHacking #Cybersecurity #LowLevelProgramming #CodeDive
I started with C, you get to see, learn, experience things you wouldn't in another language. Not because it's so good but that's how it is. Gives you a different perspective of the machine.
Then you learn something that doesn't have the flaws of C and never want to get back.