wsuks - ein elegantes Hacking Tool für jedes #Windows #AD, wo ein #WSUS ohne #PKI betrieben wird.
#Pki
Как отправлять документы с грифом ДСП по электронной почте: законы, шифрование, автоматизация
Документы с грифом «Для служебного пользования» (ДСП) содержат сведения ограниченного распространения. Это информация, не подпадающая под государственную тайну, но доступ к которой ограничен по служебной необходимости или в соответствии с законами. На бумаге такие документы пересылают в плотных непрозрачных пакетах через фельдъегерскую службу, курьером или заказным письмом. Но можно ли передавать такие данные по электронной почте — и если да, чем заменить этот самый «плотный пакет» в цифровом виде?
https://habr.com/ru/articles/924106/
#дсп #шифрование #почта #email #mime #документооборот #автоматизация_документооборота #pki #гост
Building Your Own PKI with Step-CA – From Root CA to Proxmox Integration with ACME!
In this #HowTo we create an own, decentralized PKE with #stepca, enable #ACME and integrate a #Proxmox node to obtain a certificate.
#proxmox #stepca #opensource #howto #homelab #enterprise #pki #security #decentralized #x509 #certificates
Action Steps:
Monitor all outbound PKI cert traffic to DoD/DISA and volume spikes—especially on non-admin systems.
Dump & hash all current root/intermediate certs.
Verify your “trusted roots” against air-gapped, known-good images.
Don’t trust “automated recovery” if you notice PKI/OCSP anomalies.
We are witnessing the weaponization of certificate trust infrastructure against military/civilian defense.
#infosec #DoD #PKI #cybersecurity #zerotrust #supplychain #nationalsecurity
Dear #pki (specifically #xpki) people: are you aware of any relying party that uses CN as part of the #certificate validation. I was told that having IP addresses in X.509 CN field (corresponding to an existing IP SAN) poses a security danger, but I cannot figure out why...
Настройка КриптоПро HSM Client на Suse/RedHat/ROSA Linux и Мир будущего
В новой публикации я покажу, как разработчику информационных систем со встроенными СКЗИ настроить интеграцию с программно-аппаратным криптографическим модулем КриптоПро HSM. Научимся использовать HSM, как самостоятельный криптографический провайдер с выполнением всей математики на борту или только в качестве надежного хранилища ключевого материала. И в завершении затронем важные вопросы ответственности и этики, которые неизбежно возникают при работе с данными технологиями и инструментами.
https://habr.com/ru/companies/alfa/articles/917198/
#linux #криптопро #hsm #cryptopro #pki #криптопровайдер #криптография #электронная_подпись #ключи_шифрования #альфабанк
🔐 Un certificat auto-signé n’est pas une sécurité.
Il ne prouve rien, ne garantit rien, n’est reconnu par personne.
Si ton système est partagé, connecté ou critique : PKI obligatoire.
Même en test, même en préprod.
Une dette technique dangereuse, pas une “solution pragmatique”.
I'm jealous, bitcoiners can backup their wallers to seed phrases. It's not really possible to do the same thing with PGP keys.
🎙️ Nouveau podcast sur les Key Ceremonies avec Dominique Derrier et Thomas Veynachter
Saviez-vous que seulement 0,04% de la population connaît ces processus ultra-secrets qui protègent TOUTES vos transactions numériques ? 🔐
15 personnes dans des cages de Faraday, des clés qui valent des milliards, des héros invisibles...
🎧 Web: https://polysecure.ca/posts/episode-0x597.html#32756e1b
🎧 Spotify: https://open.spotify.com/episode/2zcXdViHv1EsDetCsAX2OM?si=9SsT57CiQtuA31YJLydRsw
🎧 YouTube: https://youtu.be/wAmQg7BAGu0
I know #Docker is THE hot thing these days, but I swear, sometimes is JUST makes my life much more difficult than it needs to be.
e.g. I have an internal-only service, Zero WAN/Internet access, which will not run without HTTPS/certs as it leans on browser crypto APIs.
Okay, not unusual, but can I deploy certs to a container easily? Fuuckkkkk no. The tool's creator recommends #ACME (#LetsEncrypt or another tool implementing ACME) but again, no-internet.
Well, I have an internal #PKI. Their docs contain a one-liner saying it should use #Caddy / #traefik / #nginx reverse proxy in that situation. Now, I have to stand up, configure, manage, etc. something else just to drop a cert in front of this thing. It's still not natively encrypted.
Took me 10 seconds to whip up a cert from my infra and it's gonna take me longer to build something to actually dish it out.
OpenBAO (Vault open-source fork) Namespaces
https://openbao.org/blog/namespaces-announcement/
#ycombinator #openbao #secrets_management #open_source #linux_foundation #encryption_as_aservice #key_management_system #pki #transit #ssh #secret_vault #database_passwords
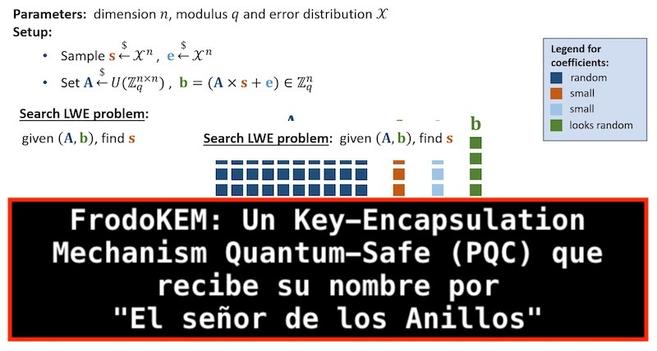
El lado del mal - FrodoKEM: Un Key-Encapsulation Mechanism Quantum-Safe (PQC) que recibe su nombre por "El señor de los Anillos" https://elladodelmal.com/2025/05/frodokem-un-key-encapsulation-mechanism.html #PQC #Criptografía #Quantum #LearnWithErrors #Cifrado #PKI #KEM
Il y a des experts en cryptograhie ici ?
Un certificat avec des SANs mais sans Common Name / Subject ; c'est possible ?
https://crt.sh/?id=18519921301
#tls #pki #https
Wir sind auf der Zielgeraden zu unserer Secure #Linux #Administration Conference 2025 in Berlin und die Vorfreude steigt. 🎉 Nutzt die Chance und seid vom 2.-4. Juni 2025 dabei!
Die letzten Programmslots sind gefüllt mit Vorträgen zu #PKI-Architekturen und zu UC Cloud Services sowie mit einem Workshop zu modernen #Shell-Features - insgesamt warten 20 Vorträge und 6 Workshops auf euch.
🎟️ Jetzt anmelden:
https://www.heinlein-support.de/news/last-call-slac-2025
The SignServer Team is happy to announce the release of SignServer CE 7.1.1
Featuring NIST approved quantum-safe algorithms ML-DSA and SLH-DSA.
https://github.com/Keyfactor/signserver-ce/releases/tag/v7.1.1
#Keyfactor #SignServer #digitalsignatures #codesigning #pki #postquantum
MT @digicert@x.com
#TLS cert lifetimes are shrinking to 47 days by 2029. The message is clear: #automation isn’t optional anymore. As DigiCert’s Dean Coclin says, “success depends on #cryptoagility + treating #DigitalTrust as a strategy, not a set-it-and-forget-it task.” 🔐
https://www.digicert.com/blog/tls-certificate-lifetimes-will-officially-reduce-to-47-days #pki #news #x509
New Open-Source Tool Spotlight 🚨🚨🚨
Active Directory Certificate Services (AD CS) can be a goldmine if misconfigured. Tools like Certipy simplify enumeration and abuse, leveraging techniques like Shadow Credentials, Golden Certificates, and domain escalation paths (ESC1-ESC11). #CyberSecurity #RedTeam
Certipy's `shadow` command exemplifies ADCS weaknesses. By manipulating `msDS-KeyCredentialLink`, you can take over accounts via PKINIT. It's seamless but devastating for privilege escalation. #Pentesting #ActiveDirectory
Golden Certificates mimic Golden Tickets but target ADCS. Using a compromised CA private key, an attacker can forge certs for domain controllers or users. Certipy automates this process—caution with CA backups. #InfoSec #PKI
🔗 Project link on #GitHub 👉 https://github.com/ly4k/Certipy
#Infosec #Cybersecurity #Software #Technology #News #CTF #Cybersecuritycareer #hacking #redteam #blueteam #purpleteam #tips #opensource #cloudsecurity
— ✨
🔐 P.S. Found this helpful? Tap Follow for more cybersecurity tips and insights! I share weekly content for professionals and people who want to get into cyber. Happy hacking 💻🏴☠️
So it's official: TLS certificate lifetimes will reduce from the current max of 398 days to:
* 200 days in March 2026
* 100 days in March 2027
* 47 days in March 2029
For web servers/proxies etc. it's reasonably simple, at least for smaller orgs but for e.g. network kit it might be more of a challenge. Having a timeframe to aim at definitely focusses the mind!
Via @riskybiz / https://risky.biz/risky-bulletin-ca-b-forum-approves-47-day-tls-certs/
Specific schedule:
March 15, 2026 - Cert validity (and Domain Control Validation) limited to 200 days.
March 15, 2027 - Cert validity (and Domain Control Validation) limited to 100 days.
March 15, 2029 - Cert validity limited to 47 days and Domain Control Validation limited to 10 days.
There's gonna be a lot of complaints about this in change control meetings over the next year200 days.
#Certificate #Certificate_Management #CABForum #PKI #WebPKI #SSL #TLS
Buckle up, kids. Automate your certificate rotations or die trying. WebPKI certificate validity period will be 47 days by 2029. https://www.bleepingcomputer.com/news/security/ssl-tls-certificate-lifespans-reduced-to-47-days-by-2029/
#Certificate #Certificate_Management #CABForum #PKI #WebPKI #SSL #TLS