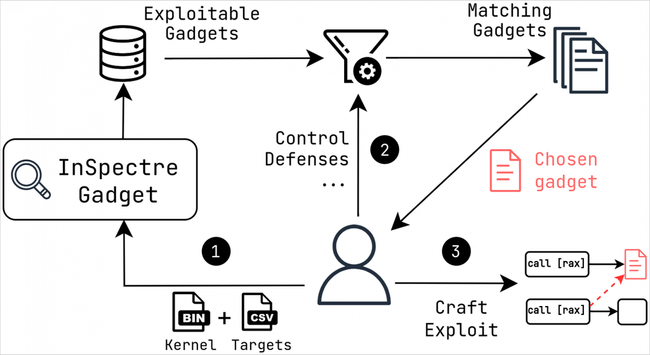
Want more #SpeculativeExecution bugs? “You’re gonna be in a great mood all day.”
#Apple’s latest three generations of #ARM ISA chips have a pair of #Spectre-like vulnerabilities. But, unlike other #SpeculativeExecution flaws, this one seems like the real deal: It could actually be exploited to steal your private info. “Four or five seconds—it’s done!”
#Apple’s known about at least one of the bugs for TEN months. In #SBBlogwatch, we wonder why Tim’s crew did nothing about it. @TheFuturumGroup @TechstrongGroup @SecurityBlvd: https://securityboulevard.com/2025/01/slap-flop-apple-silicon-richixbw/?utm_source=richisoc&utm_medium=social&utm_content=richisoc&utm_campaign=richisoc $AAPL