The world needs a #luks2 enrypted, #immutable #atomic #linux whith #selinux, #flatpaks and the #COSMICdesktop to attack Microsoft. Right now, would be perfect :owi: #aerynos #fedora #opensuse
#luks2
I know probably nobody's gonna care, but support for #Argon2 was finally merged in upstream #grub and I'm so happy. I kinda disliked the fact that we had to rely on downstream patches. Now that it's all upstream, I can setup full disk encryption, including /boot, with #luks2 on my #libreboot #thinkpad
So i just tried to install #Debian13 with only one ESP and two #LUKS2 partitions of which one is for swap and other for the OS itself.
And guess what?
The installer error'ed out due to the fact it could not install the #Grub #Bootloader, because i didn't setup a separate partition for `/boot`.
Well i fucking do NOT want grub on my system, I want to use `systemd-boot`!
It doesn't even want to install sd -boot if it can't install grub first!
So once again "up-yours" #Debian....🖕
I finally got my #ArchLinux disk encryption upgraded to #LUKS2. It certainly was a challenge because #grub does not seem to play nicely with it but I did get it to work. Grub has a bug in it where passphrases entered from the keyboard need to use PBDKF2 and key files need to use Argon2id. Once I figured this out, everything worked smoothly.
The #GMKtec NucBox M5 Plus is now up and running @chimera_linux
Thx again @q66 for puting all theat time and work in what is rapidly becoming my fav Linux Distro of all times.
#linux #kde #screenshot #btrfs #LUKS2 #2025
Vollständige Festplattenverschlüsselung unter Manjaro Linux
Manjaro Linux bringt mit Calamares einen hervorragenden Installer mit, der aber leider nur eingeschränkte Möglichkeiten bezüglich des Partitionenlayout bietet. Eine komplette Verschlüsselung aller Linux Partitionen, inkl. /boot und dann noch […]
#btrfs #grub #luks #luks2 #manjaro #verschlüsselung
https://dirkwouters.de/vollstaendige-festplattenverschluesselung-unter-manjaro-linux/
Arch Linux mit vollständiger Festplattenverschlüsselung
GRUB Bootloader zusammen mit LUKS2 und BTRFS Dateisystem Die Einrichtung von Arch Linux mit vollständiger Festplattenverschlüsselung durch LUKS2 bietet ein hohes Maß an Sicherheit für Benutzerdaten und Systemintegrität. LUKS2 (Linux […]
#arch #btrfs #grub #installation #linux #luks #luks2 #verschlüsselung
https://dirkwouters.de/arch-linux-mit-vollstaendiger-festplattenverschluesselung/
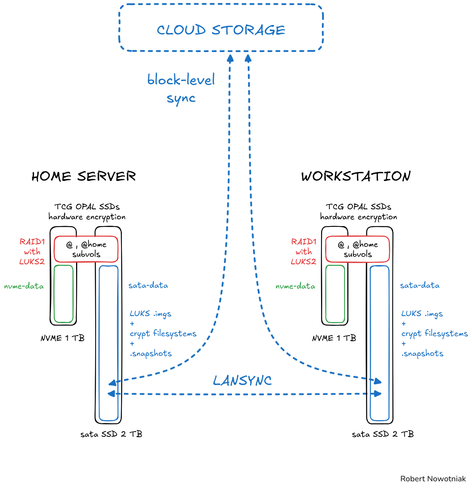
I organized my #storage like this. I think it's quite well thought out. All disks are SED hardware encrypted with TCG OPAL, root @ and @ home subvolumes are on #btrfs (mdadm RAID1), additionally encrypted with #LUKS2. A fast storage for less important local data is on NVMe drives. Data on large SATA drives is encrypted in LUKS images or using a cloud-friendly filesystems (#gocryptfs), quickly synchronized via LAN sync, and efficiently synced with cloud storage using block-level sync.
Te lo Enseño y Te lo Cuento,Seguridad física en Linux(TPM2.0, Yubikey, Luks2, clevis ySystemd) [aHAJCrYG0VY]
https://fediverse.tv/videos/watch/b453ef5d-5ce1-4c8d-a9dc-63a62778b6ab
LUKS2 and distributions starting to support it motivated me to rewrite the buffering code last Spring because that was my main turn-down in the original patch set, and then James took over and cleaned up the functionality and I reviewed it for few rounds until it was good enough.
With this and TPM2 sealed hard drive encryption there is a somewhat reasonable security model without having to type encryption password to a bootloader prompt (which is tedious). I.e. login and go.
A rare case of security feature also increasing user experience.
#linux #kernel #tpm #luks2
Is this still true ...
via https://docs.voidlinux.org/installation/guides/fde.html#encrypted-volume-configuration ...
『Cryptsetup defaults to #LUKS2, yet #GRUB releases before 2.06 only had support for LUKS1.
LUKS2 is only partially supported by GRUB; specifically, only the PBKDF2 key derivation function is implemented, which is not the default KDF used with LUKS2, that being Argon2i (GRUB Bug 59409 https://savannah.gnu.org/bugs/?59409 [0]). LUKS encrypted partitions using Argon2i (as well as the other KDF) can not be decrypted. For that reason, this guide only recommends LUKS1 be used.』
... per that bug link, seems so. Damn ... ah yes, all is coming back to me now :flashback: when I saw Justine S' https://social.treehouse.systems/@JustineSmithies efforts of installing encrypted ZFS root (& encrypted swap & hibernation)[1].
---
0- See also: GNU GRUB - Bugs: bug #55093, Add [full] LUKS2 support, https://savannah.gnu.org/bugs/index.php?55093
1- Have the bookmark ...
Installing Void Linux with encrypted Root on ZFS, published 20240103, https://justine.smithies.me.uk/void-linux-with-encrypted-root-on-zfs.html
New: Encryption with LUKS2 when installing from ISO image
Read more: https://www.tuxedocomputers.com/en/New-ISO-Image-for-TUXEDO-OS-with-encryption.tuxedo
#news #encryption #installation #ISO #luks2 #linux #linuxuser
Linux Weekly Roundup: EndeavourOS Galileo with KDE, Rocky Linux 9.3 Updates, Proxmox VE 8.1 Enhancements, and More!
#EndeavourOS #RockyLinux #Proxmox #FreeBSD #OpenMandriva #KDE #LUKS2 #Calamares #SecureBoot #CephReef #OpenSSH #Plasma
https://linuxtldr.com/weekly-roundup/
LUKS2 + YubiKey Bio https://funzt.info/howto/linux/2023/07/16/luks2-+-yubikey-bio.html #HOWTO #Linux #LUKS2
#Tails 5.14 Ships with Automatic Migration to #LUKS2 :linux: 🔒
https://linuxiac.com/tails-5-14-ships-with-automatic-migration-to-luks2/