#gocryptfs
https://bshankar.pages.dev/full-disk-encryption/
#linux #security #performance #diskencryption #veracrypt #gocryptfs #ssd #nixos #tailsos
Just published a blog post about how I use gocryptfs to encrypt some sensitive files. https://gyorban.net/blog/how-to-encrypt-your-sensitive-files-with-gocryptfs/
#SoftwareLivre #FDroid #criptografia #Apps #Android #InfoSec #gocryptfs #CryFS #dicas
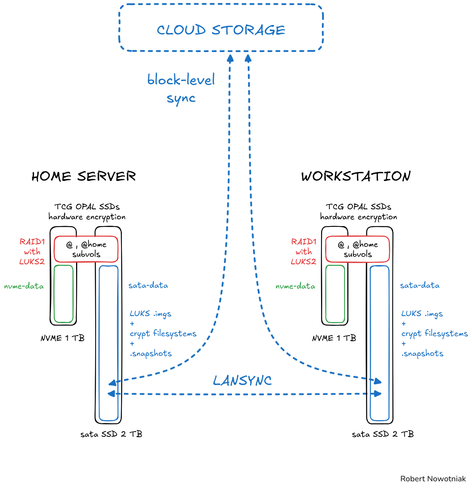
I organized my #storage like this. I think it's quite well thought out. All disks are SED hardware encrypted with TCG OPAL, root @ and @ home subvolumes are on #btrfs (mdadm RAID1), additionally encrypted with #LUKS2. A fast storage for less important local data is on NVMe drives. Data on large SATA drives is encrypted in LUKS images or using a cloud-friendly filesystems (#gocryptfs), quickly synchronized via LAN sync, and efficiently synced with cloud storage using block-level sync.
#linuxhint - automatic opening of kde vaults on login
first step is to make your vault with #gocryptfs for example for ~/Documents. then create an entry in #kwallet by creating a password in your "Passwords"-group (create it too if not present) named "vaultpass" and enter the password you used for ~/Documents. then create a bash script and let it autostart:
gocryptfs --extpass="kwallet-query -f Passwords -r vaultpass kdewallet" [.enc folder] ~/Documents
have fun :)
https://github.com/rfjakob/gocryptfs/wiki/Mounting-on-login-with-KDE-Wallet
(24/N) There are some best practices that will make it easier to answer threat modeling question #3, "What are you going to do about it?". These will help you protect a wide range of assets by taking care of your devices, so let's look at them first:
- Encrypt data at rest
- Bootstrap your workplace
- Actively maintain your devices
- Secure your devices
- Prepare for repair
1. Encrypt data at rest
What can you achieve with intermediate knowledge, without fully descending into the rat hole?
⚠️ Caveat: this is best done when setting up #Linux on a new device. Modifying an existing installation on your own IMHO isn't advisable if you're not a seasoned user. If you still decide to venture into it, make SURE you have backed up all your assets, before following "howtos on the internet". You have been warned.
Likening your device to a medieval city:
1) Full-Disk Encryption (FDE) is like locking the "city gate". Most popular Linux distributions offer FDE during the installation process. FDE is also your last line of defense when your device gets stolen, or your disk fails and cannot be safely wiped before disposing of it. Use FDE. (Yes, technically, "Full" is not absolutely accurate. We'll leave it at that.)
2) Within your "city", there will likely be at least two "houses": the home of the admin account, and your personal home. Using FDE alone, the "doors" of these homes won't have any locks of their own. Possibly not a big deal with respect to the administrative account, but admins being able to access any of your non-public assets, even when you're not logged in, is probably not what you want.
While the specific steps depend on your preferred Linux distro, a "portable" solution is to create a separate, encrypted disk partition, and have it mounted as your user home directory, when you log in. That solution is based on cryptsetup and the pam_mount module, a nice tutorial example is:
3) Within your "house", you may wish to have a locked "chest", e.g. for your #FYEO assets. There's essentially two options: a) a single, encrypted container file that acts as a "#vault" for your asset files; or b) an encrypted overlay file system that maintains an openly visible directory hosting your encrypted assets, including directory structures, in the background; and allows you to mount a decrypted counterpart, for working on your assets.
a) A "vault", being a single file, is easy to copy and carry around, on arbitrary storage media, e.g. USB sticks. It doesn't reveal too much about its contents, but resizing it takes a little effort. Also, you can't "incrementally backup" content changes, just copy the whole, changed vault.
A nice tutorial for creating and using a vault using plain, standard cryptsetup is https://opensource.com/article/21/4/linux-encryption by @seth . If you must have a GUI for creating and mounting vaults, look at #zuluCrypt https://mhogomchungu.github.io/zuluCrypt/ – IMHO the app is still in need of a little polish, though.
b) An encrypted overlay file system allows for incrementally backing up changed assets, but exposes considerable metadata (rough file sizes, directory structures, modification dates).
The most widely used package for this is probably #gocryptfs. Its "HowTo" is literally a one-pager: https://nuetzlich.net/gocryptfs/quickstart/
Start of this thread:
https://mastodon.de/@tuxwise/113503228291818865
🔄 Back In Time seeking help to test its new #gocryptfs feature
Шифрование для облака: разные подходы
Облачные сервисы по-разному подходят к шифрованию данных на своём хостинге. В некоторых случаях это шифрование не удовлетворяет требованиям безопасности, поэтому приходится брать задачу в свои руки и шифровать файлы самостоятельно.
https://habr.com/ru/companies/ruvds/articles/846478/
#бэкапы #шифрование #Encryption_SDK #Database_Encryption_SDK #Secrets_Manager #Clean_Rooms #C3R #CloudHSM #KMS #HSM #DEK #KEK #multikeyring #restic #rsync #gocryptfs #cppcryptfs #DroidFS #gocryptfsinspect #Cryptomator #ruvds_статьи
#clt2024 folien & video zur sicheren Datenhaltung in der #Cloud sind on
#gocryptfs #rclone #duplicity #kryptographie
https://chemnitzer.linux-tage.de/2024/media/programm/folien/211.pdf
https://media.ccc.de/v/clt24-211-sichere-datenhaltung-und-backup-in-der-cloud
@VerseAndVermin Thanks for the follow-up. I never used their cloud service (I generally prefer #gocryptfs or #cryfs encrypted volumes on providers like dropbox.
However, that does sound concerning - I'll avoid using them too - I liked that they were a very old player that was in the market since the #wordperfect days, but the times have changed.
Hopefully #freeoffice works better for you, though I've found myself liking #onlyoffice over freeoffice.
Compiling a list of my favourite niche FOSS applications, after all it's #FossFriday
#Diylc
#Kicad
#Arduino
#Stellarium
#Kstars
#KeepassXC
#Gocryptfs
#Cryptomator
#libreoffice
Python is there as I use it as a scientific calculator and to test designs.
What are your goto #FOSS favourites?
@UmWerker
Hallo, ist zwar nicht pgp aber verschlüsselt auch sicher mit #gocryptfs , die APP bei f-droid --> #droidfs, unter Linux mit #SiriKali, als Alternative, Grüße Rallo
Playing around with #salt on #plantuml to write #wireframes out of boredom. Had been aware, but not really tried my hand at this stuff - it is pretty convenient.
I do have a shell script wrapper at the moment that I've been using locally to automount/unmount my #gocryptfs and #cryfs folders while storing the passwords in #kdewallet. I'd like to convert that to a #python UI (I'm not proficient in python or GUI design). Been reading up in my spare time on #qtquick #qml etc.
@cybersoldier @tuxi in the background, I generally have #signal desktop, #bitwarden , #cryfs #gocryptfs and other messaging/music apps. While these are generally not CPU intensive, they eat up a reasonable amount of RAM
@spinlock I use #gocryptfs to encypt folders and safely move them around (#syncthing, cloud, flash drive, etc)
Some new development here: I actually took the advice of above article and use #gocryptfs for this now with the "plaintextnames" parameter, such that file names stay un-obfuscated and #rsync's exclude option works as intended.
Looks like gocryptfs is a lot faster too. Seems like the ideal option for my #backup needs